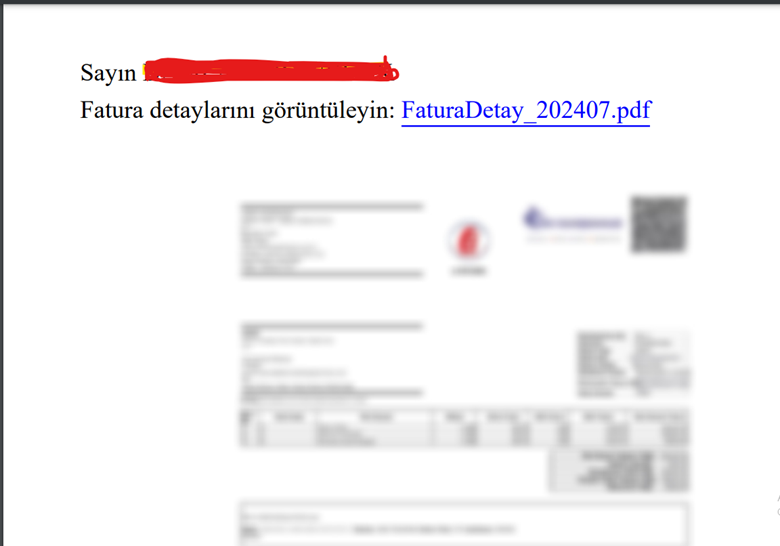
PDF attachment
Forcepoint X-Labs, a leading cybersecurity research team, has unveiled a new ransomware strain dubbed “ShadowRoot” specifically targeting Turkish businesses. The attack begins with phishing emails containing malicious PDF attachments disguised as invoices, originating from a Russian domain.
The attack commences with the delivery of seemingly legitimate invoices as PDF attachments via email. Embedded within these PDFs is a malicious link that, upon user interaction, triggers the download of an executable file hosted on a compromised GitHub repository.

The downloaded payload is a Delphi binary engineered to drop additional components designed to obfuscate its activities and evade conventional security measures. These components culminate in the deployment of the primary ransomware payload, “RootDesign.exe,” which systematically encrypts files across the victim’s system, appending the “.shadowroot” extension to each compromised file. Victims are subsequently presented with a ransom note in Turkish, directing them to initiate contact with the threat actors via email for further instructions regarding ransom payment and decryption.
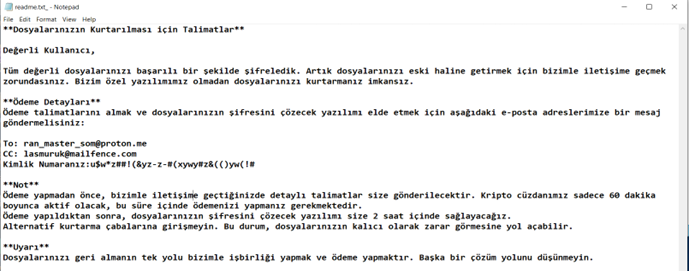
The ransomware establishes an SMTP command and control (C2) connection to smtp[.]mail[.]ru on port 587, sending details to suspicious email accounts associated with “kurumsal[.]tasilat @internet[.]ru”.
ShadowRoot appears to be a relatively rudimentary ransomware variant, likely the product of an inexperienced developer. Despite its basic functionality, the ransomware effectively targets Turkish businesses by exploiting fake PDF invoices to lure victims into downloading malicious payloads. The encryption of files with the “.ShadowRoot” extension and connection to a Russian SMTP server indicate a targeted and somewhat sophisticated approach.
The Forcepoint X-Labs Research Team urges businesses to remain vigilant and employ robust email security measures to mitigate the risk of such ransomware attacks. As cyber threats continue to evolve, maintaining up-to-date security protocols and educating employees about phishing tactics are essential steps in safeguarding against potential breaches.