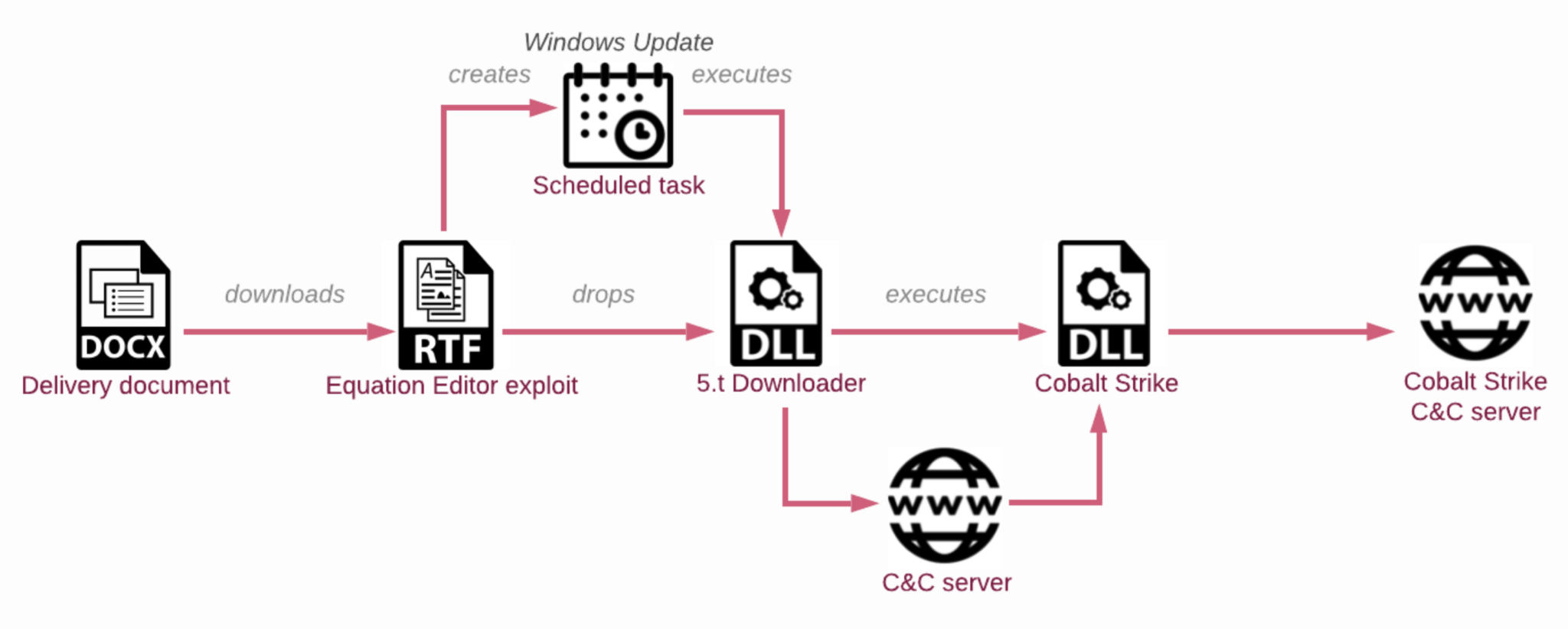
Sharp Dragon’s Infection chain since May 2023 campaign
A new report from Check Point Research reveals a significant shift in the tactics and targets of the Chinese state-sponsored advanced persistent threat (APT) group, Sharp Dragon. Previously focused on Southeast Asia, the group has now expanded its cyber espionage operations to government entities in Africa and the Caribbean.
Starting in November 2023, Sharp Dragon began targeting governmental entities in Africa and the Caribbean. This strategic shift involved exploiting previously compromised entities in Southeast Asia to launch phishing attacks on new territories. The threat actors used highly-tailored lures related to inter-governmental relations between Southeast Asia and the targeted regions.
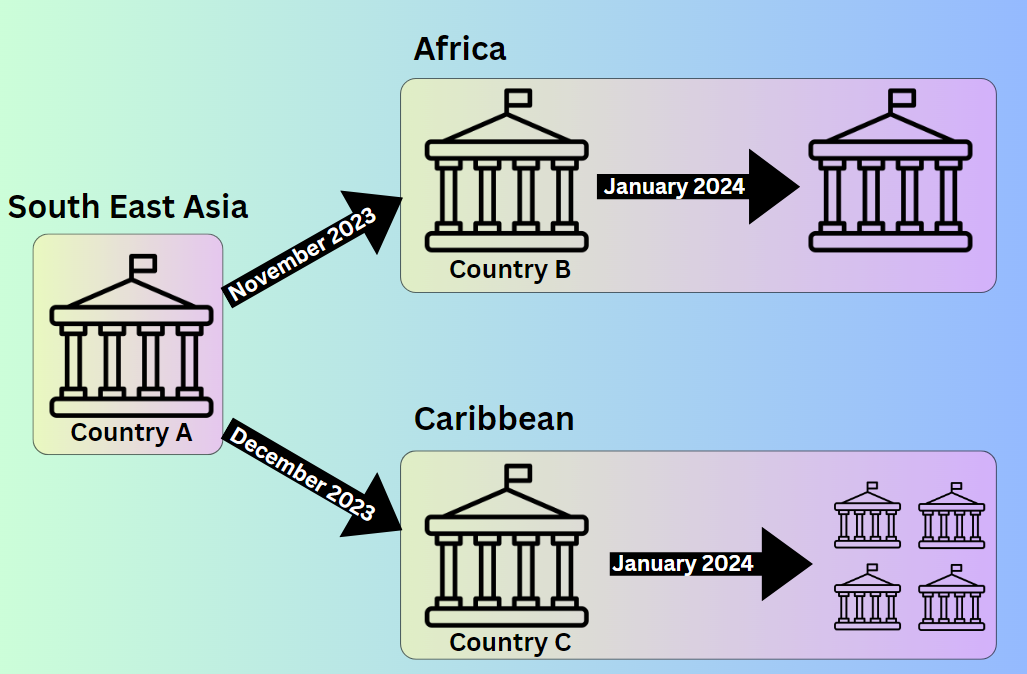
The first observed phishing attack targeting Africa originated from a Southeast Asian country and was sent to a government in Africa. The phishing document, which focused on industrial relations, appeared authentic and was likely derived from genuine correspondence. By January 2024, Sharp Dragon had launched direct attacks within Africa, indicating the initial phishing campaigns were successful.
In a parallel effort, Sharp Dragon targeted governmental organizations in the Caribbean, using compromised networks from Southeast Asia. The first malicious documents, sent in December 2023, used a lure related to a Caribbean Commonwealth meeting. By January 2024, compromised email infrastructure in the Caribbean was used to send a large-scale phishing campaign targeting multiple governments in the region, this time using a survey on the opioid threat as a lure.

The group’s adaptability is evident in their evolving tactics, techniques, and procedures (TTPs). Sharp Dragon has adopted wider reconnaissance practices on target systems, enabling them to identify and exploit vulnerabilities more effectively. They have also shifted to using the Cobalt Strike Beacon payload, a versatile tool for establishing backdoor access and executing commands remotely. This move away from custom malware indicates a deliberate effort to evade detection and attribution.
Furthermore, CPR discovered that Sharp Dragon has shifted from using dedicated servers to leveraging compromised servers as C2 servers. In a campaign observed in May 2023, Check Point Research noted that some servers used by Sharp Dragon were legitimate servers that had been compromised. It is suspected that Sharp Dragon exploited the CVE-2023-0669 vulnerability in the GoAnywhere platform to achieve this.