SharpFtpC2: Streamlined FTP-Driven Command and Control Conduit
SharpFtpC2
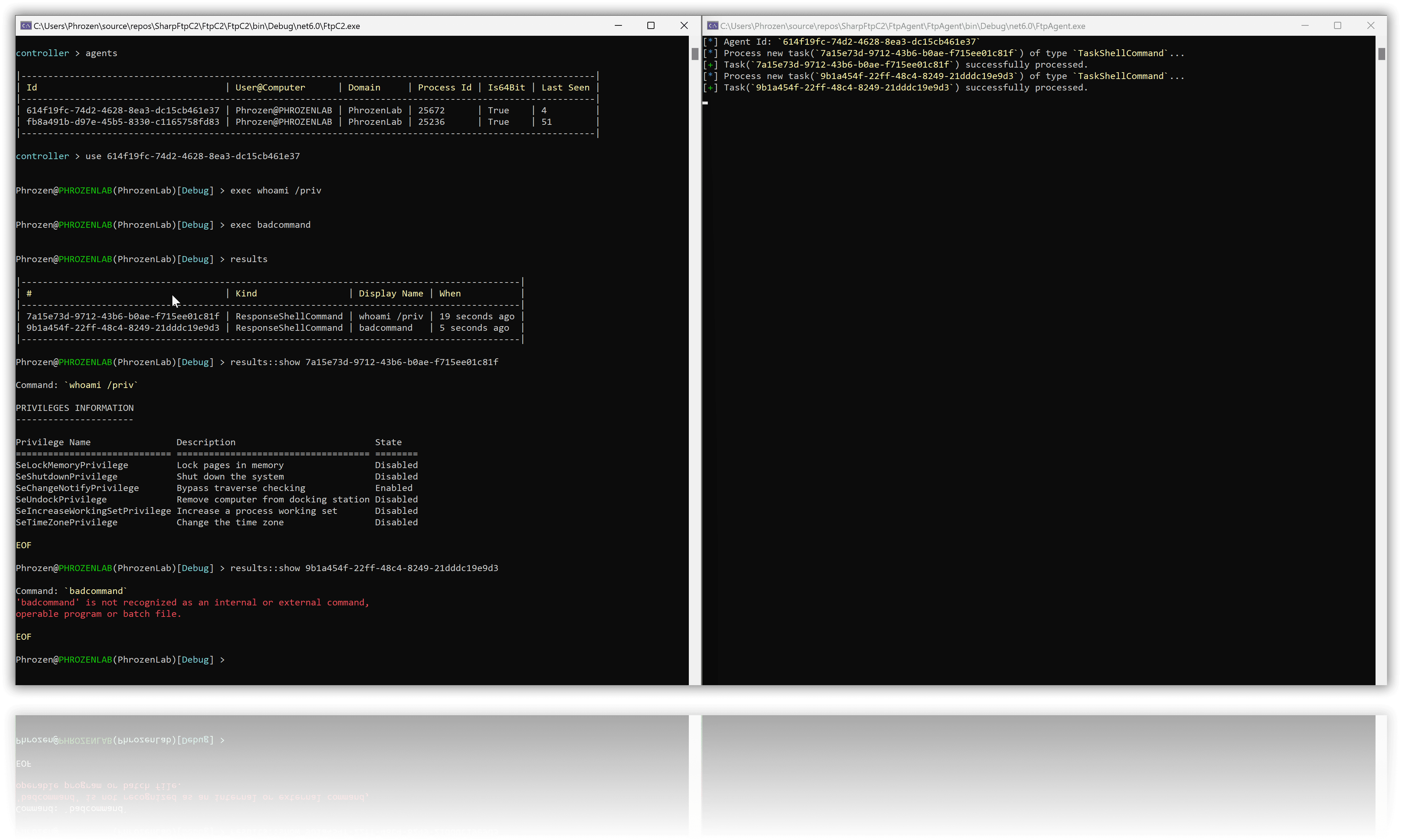
SharpFtpC2 is a small, experimental project aimed at exploring the possibility of using FTP(S) for relaying commands and responses between two remote computers. It employs the FTP protocol as a makeshift tunnel through which the computers, both acting as clients connected to an FTP server, can communicate. A simple session management scheme is used to keep track of the exchange of requests and responses.
SharpFtpC2 employs a basic session management system. Although quite elementary, it serves the purpose of keeping communications synchronized and related, which is essential for the back-and-forth between remote systems.
It’s worth noting that this project can be effortlessly ported by utilizing version control systems such as git, svn, or similar protocols.
If you have an interest in the nitty-gritty of network communication or just want to fiddle with C# and .NET Core, SharpFtpC2 might be an intriguing starting point. Don’t expect a polished gem, but maybe, just maybe, you might learn something interesting from tinkering with it.

C2 Encryption (RSA + AES)
To ensure the integrity and confidentiality of all communications between the agents and the C2, encryption has been seamlessly incorporated into the communication protocol, employing both RSA and AES-GCM 256-bit algorithms. The primary objective of this feature is to thwart the possibility of a compromised FTP server delivering malicious commands. By employing encryption, command injection is rendered impossible without access to the agent’s public key. Similarly, it is not feasible to inject fake agent responses without possession of the C2’s public key.
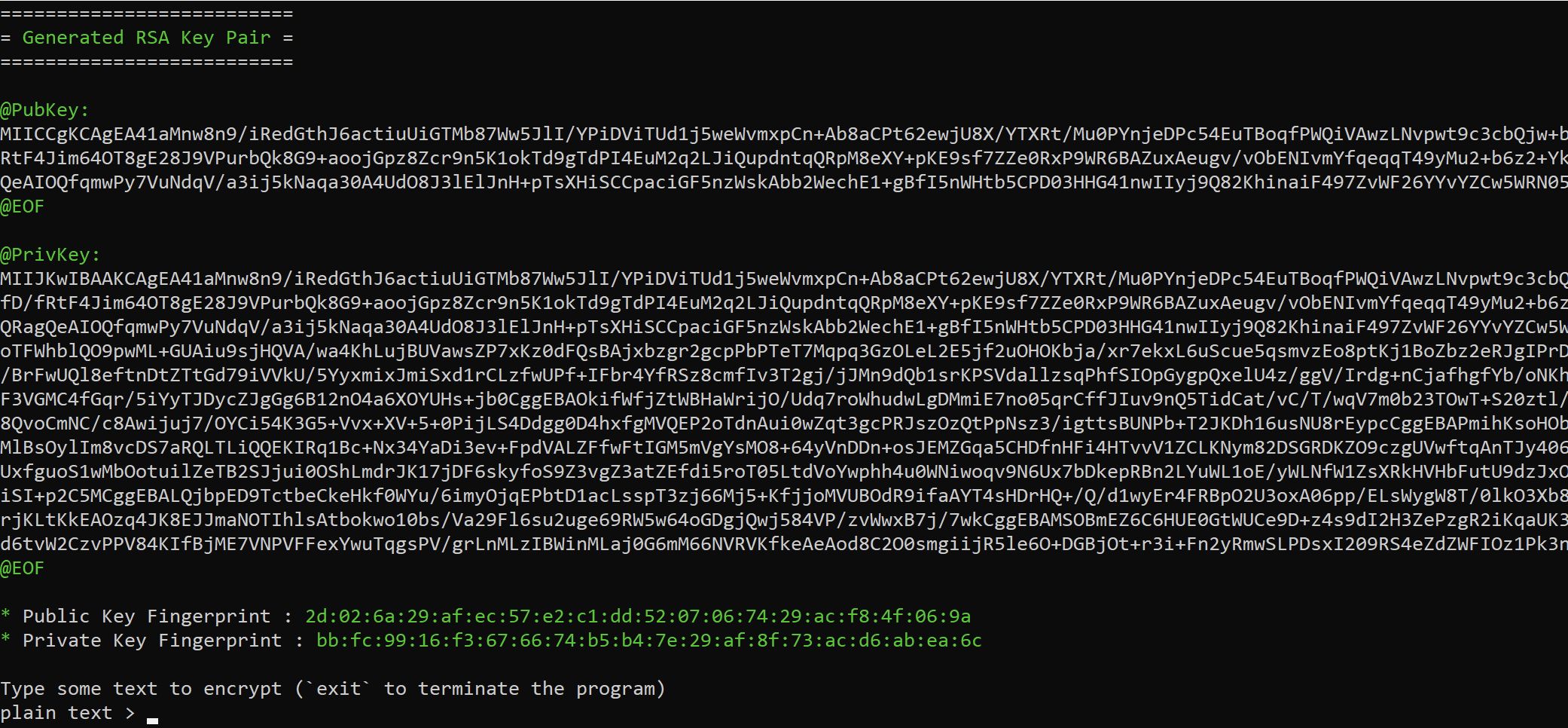
To make the process of generating your own key pairs easier (one key pair for the agent and one for the C2), I have included a third-party tool called RSAKeyHelper Each time you run the application, it will present you with a freshly generated pair of public and private keys, which can be utilized within the program if you opt to employ encryption.
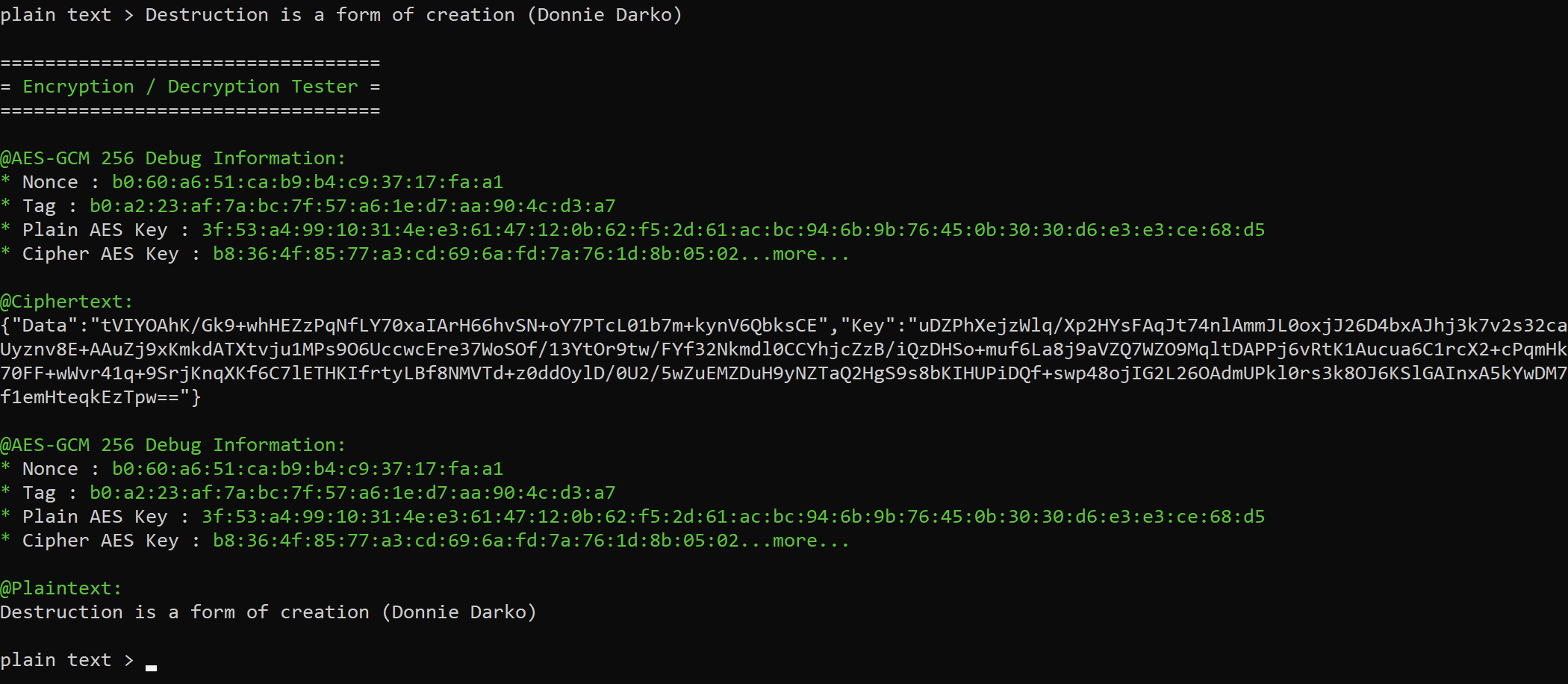
To verify that everything operates as intended, I have also integrated a feature within the same tool that allows you to test string encryption.
Supported Commands
- Run a shell command and echo the response.
- Terminate agent process.
Download & Use
Copyright (C) 2023 DarkCoderSc





