SharpZipRunner: Executes position independent shellcode from an encrypted zip
SharpZipRunner
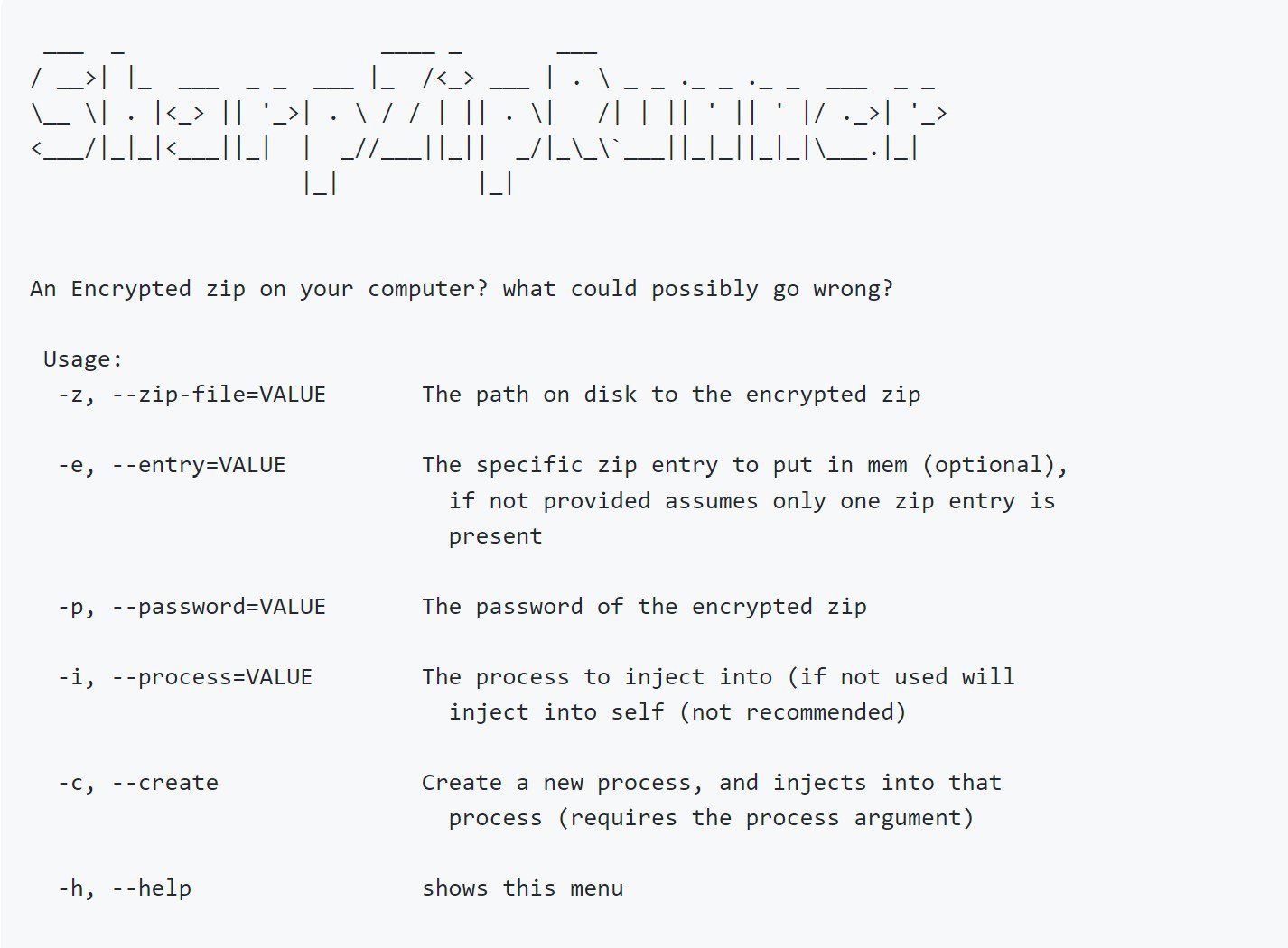
Executes position independent shellcode from an encrypted zip Get PIC code from your assembly either by using a donut or Metasploit or cobaltstrike RAW format.
zip the .bin file and encrypt it with a password, this assembly decrypts the zip entry in memory and executes it using D/Invokes injection API.
capable of injecting in a running process, or by creating a new process first and injecting into the newly created process. injection in itself should theoretically be possible, but causes crashes. as injecting into yourself is not really what I wanted to achieve here, did not really try to fix that issue.
tested by dropping the encrypted zip on disk, but could probably also work entirely in memory with some modifications. only supports PIC payloads, tried creating a runPE variant but failed miserably 🙂
Copyright (C) 2020 jfmaes





