shellen v0.2.1: Interactive shellcoding environment to easily craft shellcodes
Shellen
Shellen is an interactive shellcoding environment. If you want a handy tool to write shellcodes, then shellen may be your friend. Also, it can be used just as assembly/disassembly tool.

It uses keystone and capstone engines for all provided operations.
Shellen works only on python3. Maybe support for python2 will appear in the future.
Features
Shellen was created for assembling and disassembling instructions, so there are two modes of using the tool: asm and dsm respectively. Of course, there are some other possibilities like syscalls tables, common shellcodes and other.
Problems/New features
If you find a problem/bug or something, then just write an issue about this problem. Also, if you think, that some feature will be nice to use in shellen, then do the same — write an issue and I will try to add this feature.
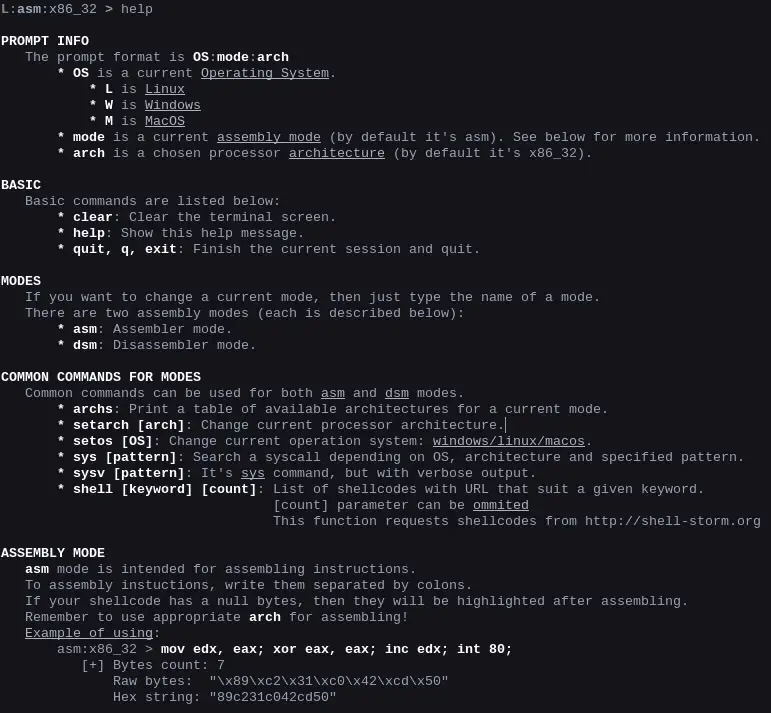
Prompt
It also has a usefull prompt, displaying current mode, OS (Operating System for syscalls) and chosen architecture exactly for this mode. It looks as follows:
You can edit your input like you’re typing in a terminal. Also, it has a history of commands (just type up arrow to see them).
L is the shortened name of Linux in the prompt. Below listed all other OS names:
Lis LinuxWis WindowsMis MacOS
Assembling
To assembly instructions, type them separated by colons as follows:
Disassembling
Architectures
asm and dsm modes work for different architectures. To see a list of available architectures for a current mode, type this:
Syscalls
It’s apparent that in process of crafting a shellcode you will be needed syscalls. So, shellen will help you with that. Just type sys with a name of desired syscall and shellen will show you a list of possible syscalls you were looking for.
This prints possible variants of syscall depending on entered pattern. Syscall table for searching depends on chosen architecture and OS (Operating System). In this case it’s x86_32 and Linux.
Common shellcodes
Shellen can show you a list of common shellcodes depending on your keyword. The example of using placed in Picturessection. It uses API of shell-storm.org site (thanks to the author!). You can use it like this:
Actually, count parameter isn’t required.
Operating Systems
It was assumed that there will be several OSs (Linux, Windows, and MacOS), but right now supported only Linux.
Changlog v0.2.1
- Fixed bugs with a prompt
- Added an ability to execute shellcodes
- Little code fixes
Installing
Copyright (c) 2017 Mike Evdokimov
Source: https://github.com/merrychap/




