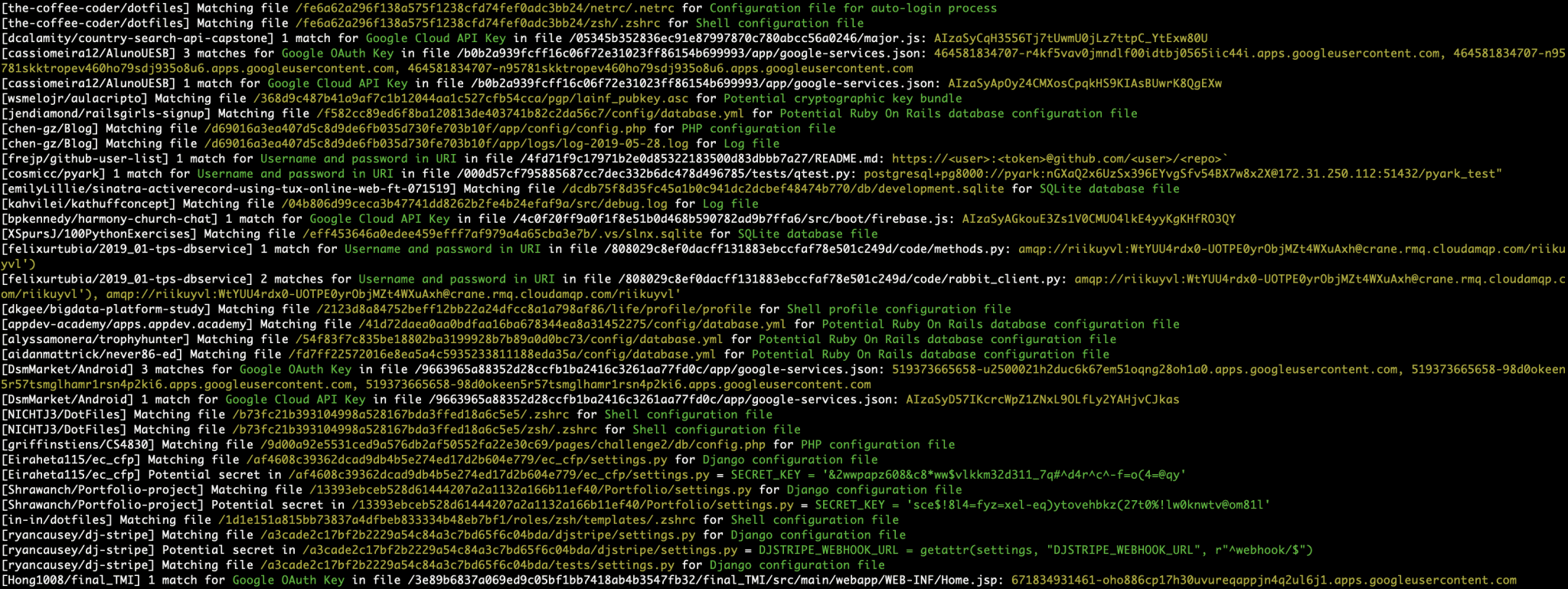
shhgit: find GitHub secrets in real-time
Shhgit finds secrets and sensitive files across GitHub code committed in near real-time by listening to the GitHub Events API.
Finding secrets in GitHub is nothing new. There are many great tools available to help with this depending on which side of the fence you sit. On the adversarial side, popular tools such as gitrob and truggleHog focus on digging in to commit history to find secret tokens from specific repositories, users or organizations. On the defensive side, GitHub themselves are actively scanning for secrets through their token scanning project. Their objective is to identify secret tokens within committed code in real-time and notify the service provider to action. So in theory, if any AWS secret keys are committed to GitHub, Amazon will be notified and automatically revoke them.
Installation
- Install Go for your platform.
- $ go get github.com/eth0izzle/shhgit will download and build shhgit.
Use
shhgit needs to access the public GitHub API so you will need to obtain and provide an access token. The API has a hard rate limit of 5,000 requests per hour per account, regardless of what token is used. The more account-unique tokens you provide, the faster you can process the events. Follow this guide to generate a token; it doesn’t require any scopes or permissions. And then place it under github_access_tokens in config.yaml.
Unlike other tools, you don’t need to pass any targets with shhgit. Simply run $ shhgit to start watching GitHub commits and find secrets or sensitive files matching the included 120 signatures.
Copyright (c) 2019 Paul
Source: https://github.com/eth0izzle/