Image: Reversing Labs
Microsoft, having previously apologized and reinstated developer themes following an erroneous deletion of two popular Visual Studio Code extensions, has now removed two extensions containing ransomware payloads, and this time, the detection is not a false positive.
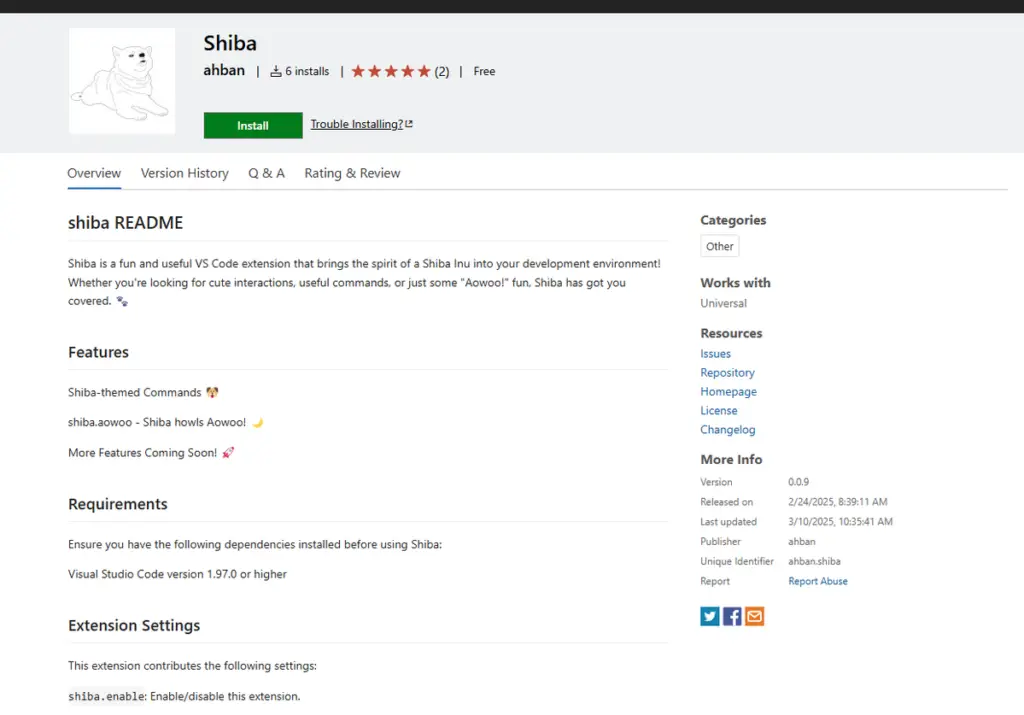
The extensions harboring the malicious ransomware payload, identified as “ahban.shiba” and “ahban.cychelloworld,” were flagged by the security research firm Reversing Labs, who promptly notified Microsoft.
These extensions integrated code that invoked PowerShell commands, subsequently downloading and executing scripts laced with malicious code from command-and-control (C2) servers. Upon execution, the scripts proceeded to encrypt files on the compromised system.
However, these extensions appear to be in their nascent developmental or testing phase, as the PowerShell payload, upon completing file encryption, displays a message stating: “Your files have been encrypted. Pay 1 ShibaCoin to ShibaWallet to recover them.” Notably, the perpetrators omitted a wallet address, suggesting this phase is experimental.
Currently, no cryptocurrency by the name of ShibaCoin exists; however, there is a related entity, Shiba Inu, which possesses an exceedingly low market value, rendering it an improbable ransom medium. It is surmised that upon finalizing development, the malefactors intend to transition to Bitcoin for ransom demands.
Those who have installed these extensions and observe a folder named “testShiba” on their desktops have likely been compromised. At this juncture, the ransomware’s scope is confined to encrypting files within the “testShiba” folder, thus mitigating any substantial repercussions.
In the interest of safeguarding user security, Microsoft has expunged these extensions and remotely disabled all installations of these two extensions within Visual Studio Code. Users will observe the automatic deactivation of these extensions and are advised to manually remove them.