Researchers from the University of California, San Diego, and Northeastern University have uncovered a potential vulnerability in wireless gear-shifting tools used by professional cyclists. This flaw could allow hackers to remotely manipulate a bicycle’s movement during a race.
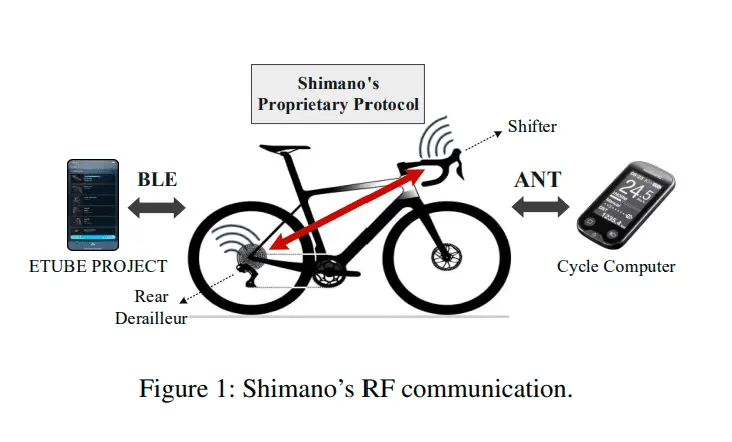
Modern high-end bicycles are increasingly equipped with electronic components, including power meters and wireless suspension control systems. Nearly all professional athletes now use electronic gear shifters, which respond to digital signals from handlebar controls, providing more precise and reliable shifting compared to mechanical systems.
The scientists demonstrated that with equipment costing only a few hundred dollars, it is possible to hack Shimano systems, which are widely used by the world’s leading cycling teams, including in prestigious competitions such as the Olympic Games and the Tour de France.
The developed attack model allows for signal emulation from up to 9 meters away, causing unexpected gear shifts on the targeted bicycle. Additionally, hackers can lock the shifters, trapping the bicycle in an incorrect gear.
To exploit the vulnerability, a hacker must first intercept the gear-shifting signals of the target bicycle. These signals can be replayed even months later. The experiment required a $300 software-defined radio, antennas, and a laptop. According to the researchers, this setup can be miniaturized enough to be concealed on the roadside, in a team car, or even in the rider’s back pocket.
It turns out that jamming wireless shifters with such a device is significantly easier than attacks involving signal replay. According to the scientists, it’s even possible to read the shifting signals from an entire group of cyclists (the peloton) and then jam the gears for everyone except one rider.
Shimano, upon learning of the research results in March, closely collaborated with the scientists to release a fix as quickly as possible. A Shimano representative recently stated that the company has developed a new firmware version to enhance the security of Di2 wireless communication systems.
The fix has already been provided to professional cycling teams using Shimano components. However, it will not be available to the general public until the end of August. The company is withholding specific details for security reasons.
Experts note that other brands of wireless shifters may also be vulnerable to similar hacking methods. They focused on Shimano only because the company holds the largest market share.
In the world of professional cycling, which has been rocked by doping scandals in recent decades, hacking competitors’ shifters could very well become a reality.
In a broader context, the researchers view their work as a warning about the consequences of the widespread adoption of wireless electronic features in various technologies—from garage doors to cars and bicycles.
Related Posts:
- The Public City Bikes System in Copenhagen was hacked and the database was deleted
- Signal Desktop Application Exists Code Injection Vulnerability