shotlooter
Shotlooter tool is developed to find sensitive data inside the screenshots which are uploaded to https://prnt.sc/ (via the LightShot software) by applying OCR and image processing methods.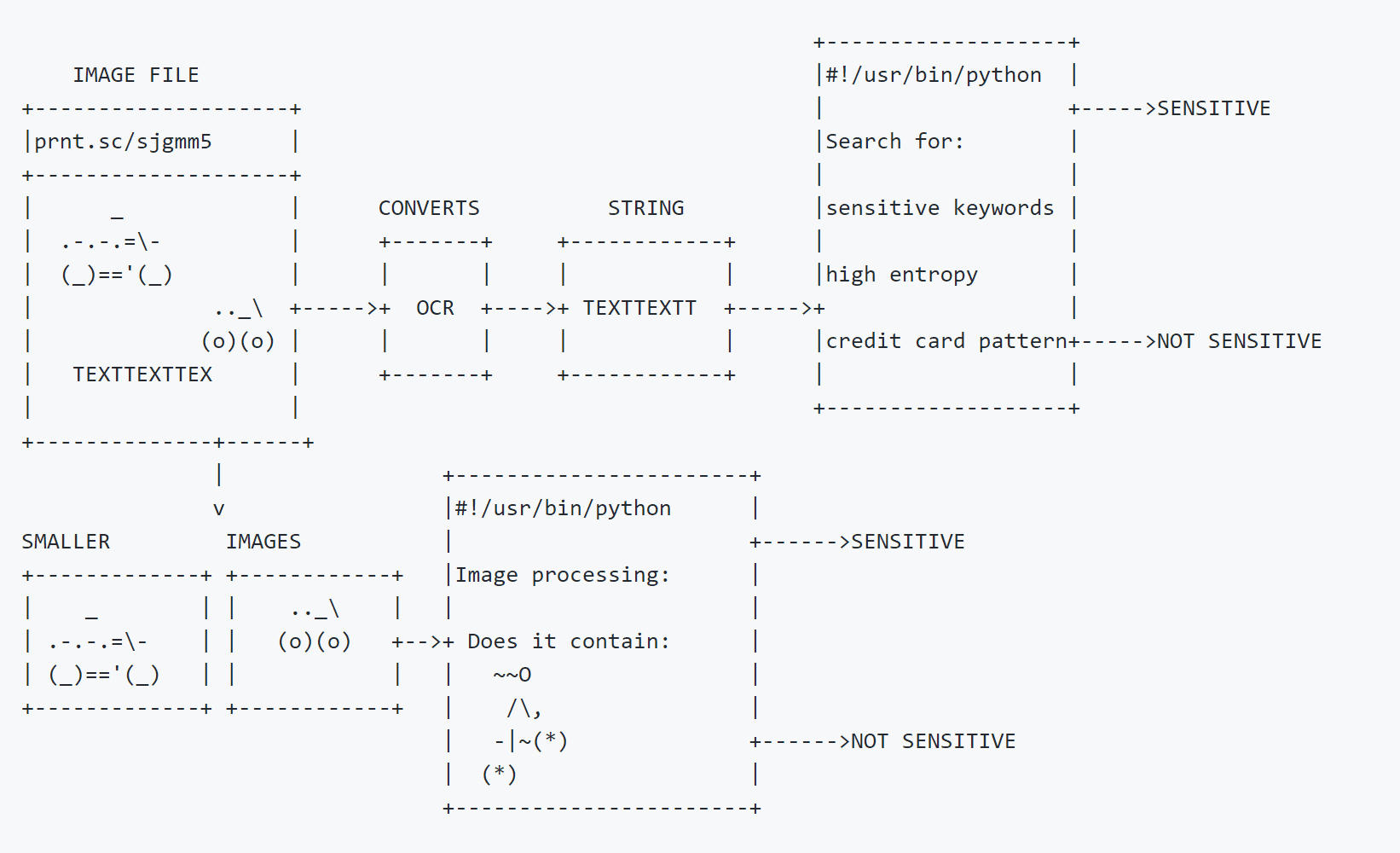
How does it work?
- Starting from the given image id, Shotlooter iterates through images (yes, image ids are not random) and downloads them locally.
- Converts the text inside the image by using tesseract OCR library.
- Searches for predefined keywords on the image (private_key,smtp_pass,access key,mongodb+srv etc.)
- Searches strings with high entropy (API keys usually have high entropy)
- Searches small images (e.g Lastpass logo) inside the downloaded image (Template Matching) with OpenCV.
- Saves the results to a CSV file
- Saves images that contain sensitive data to the
outputfolder
What You Should Expect to Find?
I run Shotlooter for 2 weeks and identified 300+ images that contain various sensitive data. You can check the findings that I encountered more than others below:
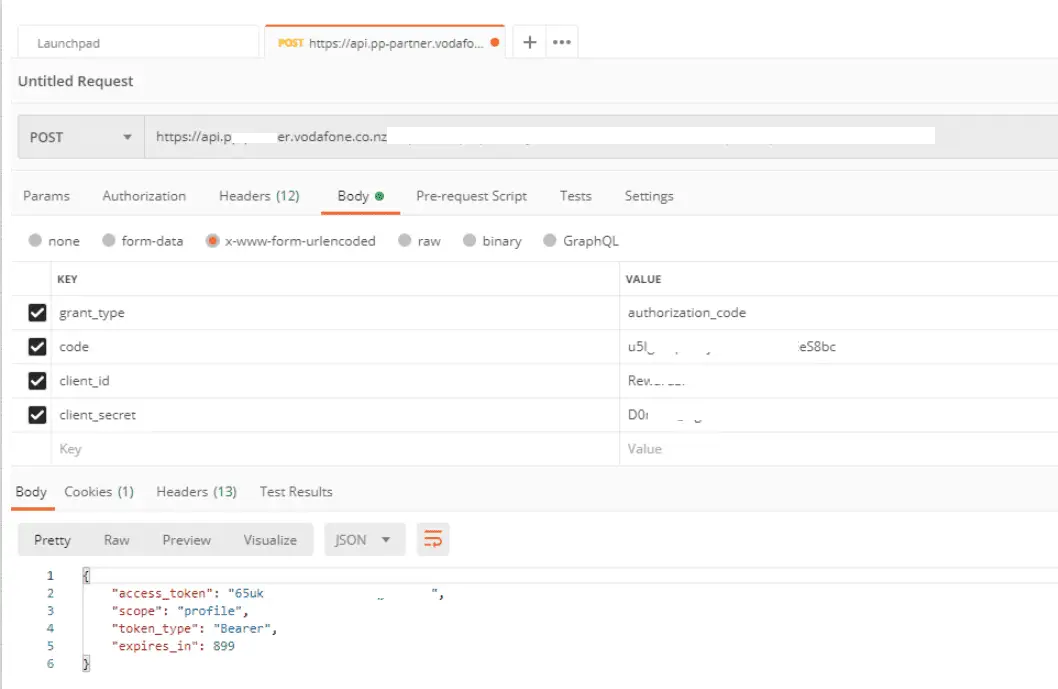
Postman Requests
Contains useful session IDs, access tokens, etc.
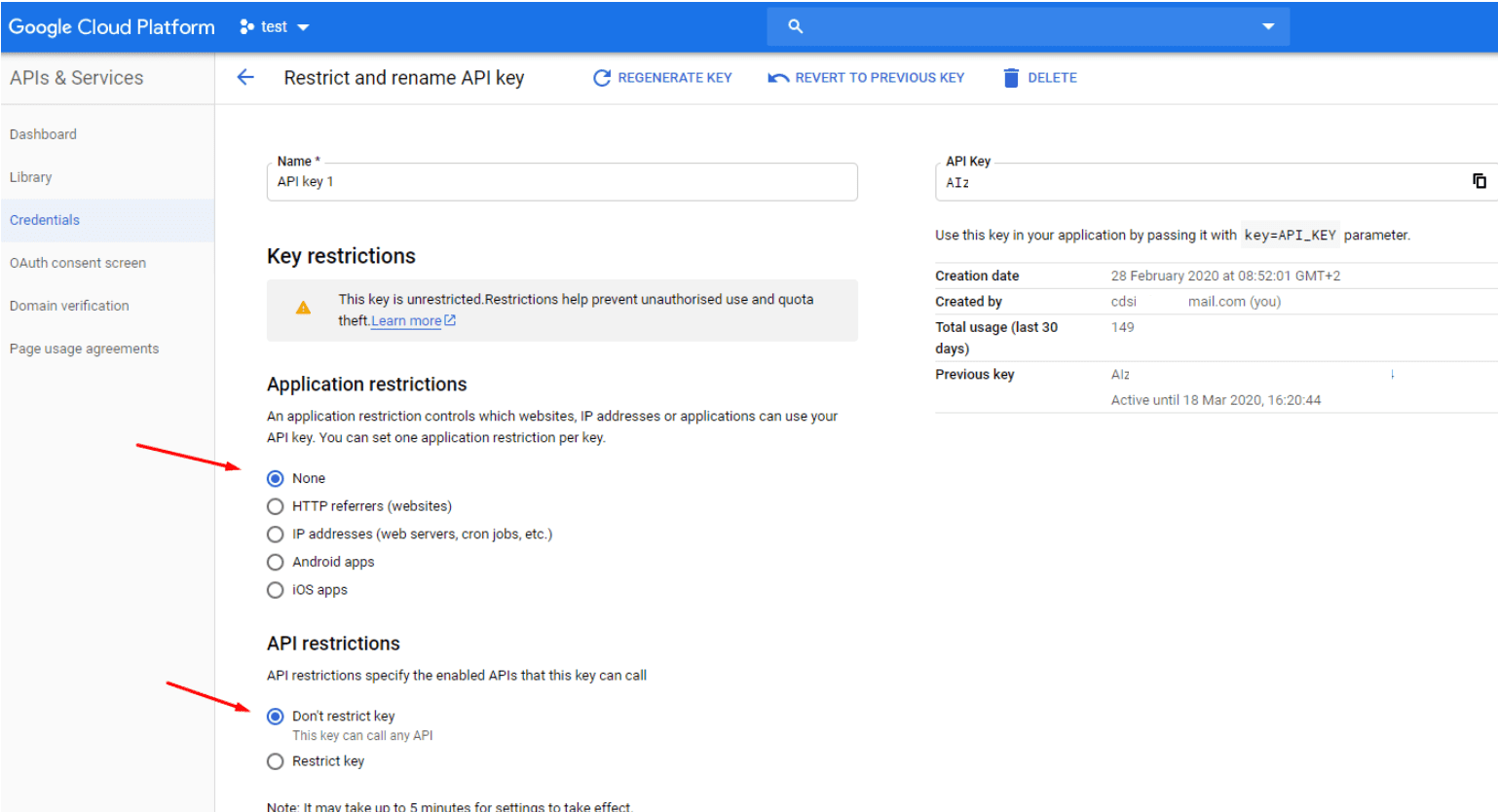
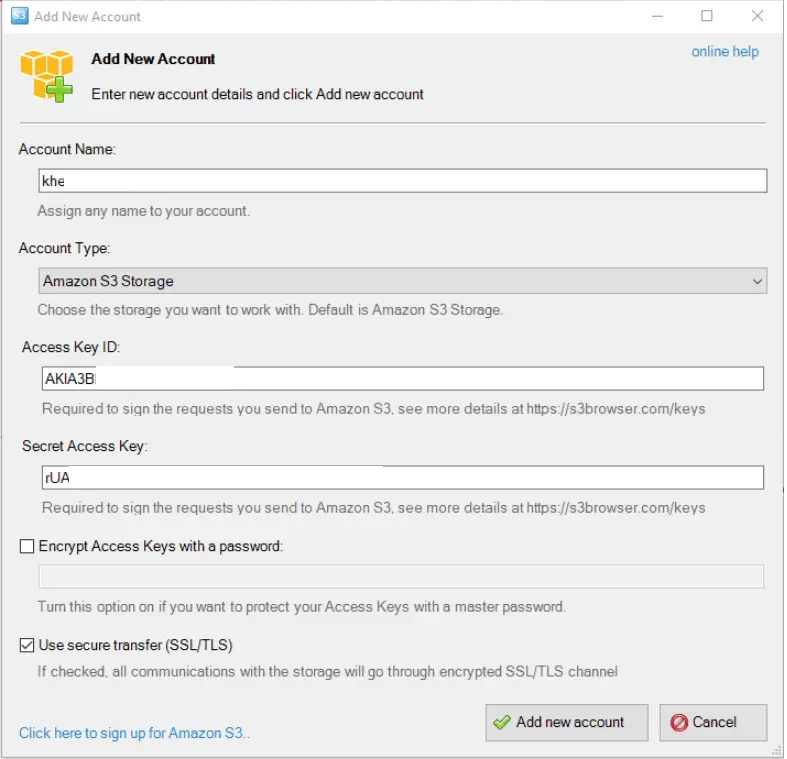
Cloud API Keys (Google, AWS)
Screenshots are taken from the cloud’s console or from a desktop client
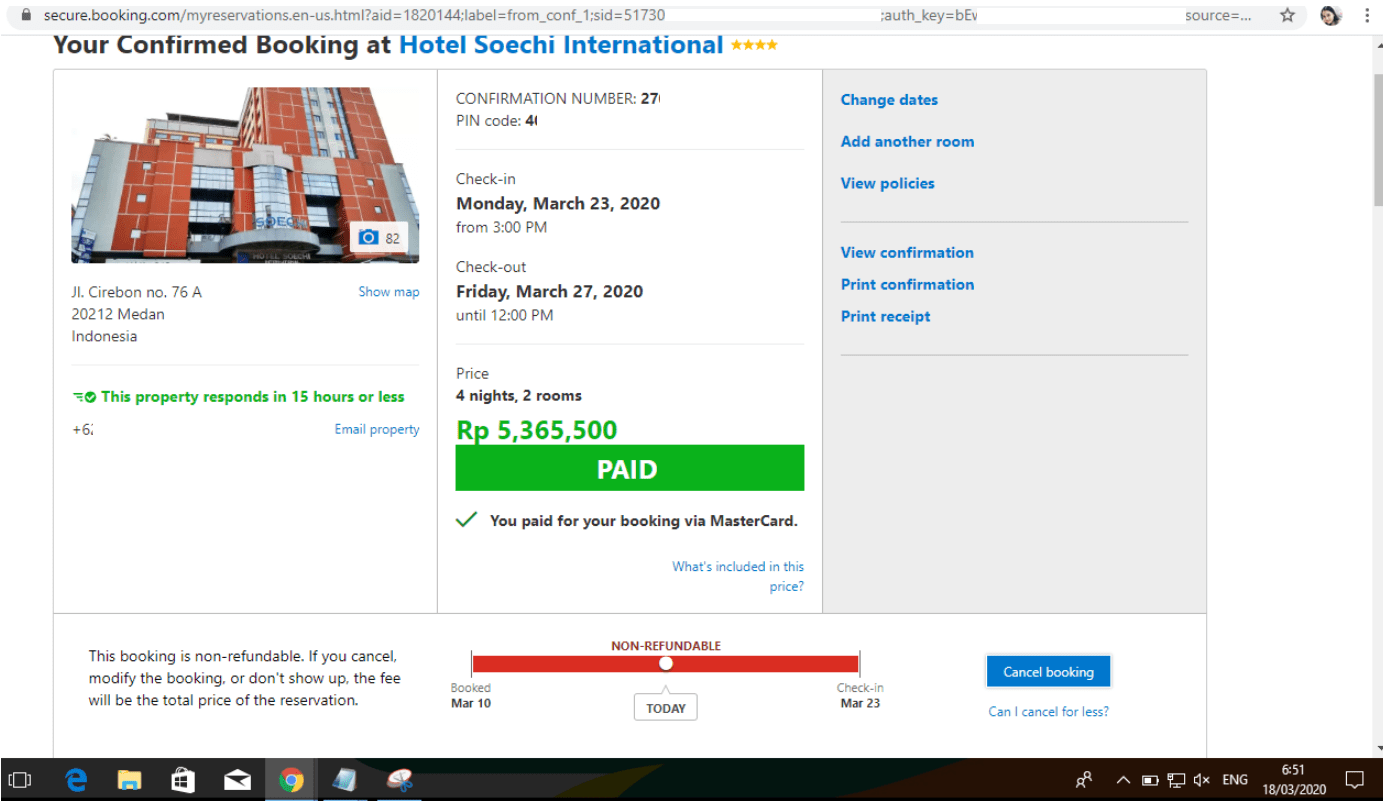
Session ID on the URL
We all know that it’s not good to pass the session ID with a GET request for different reasons. This is one of them.
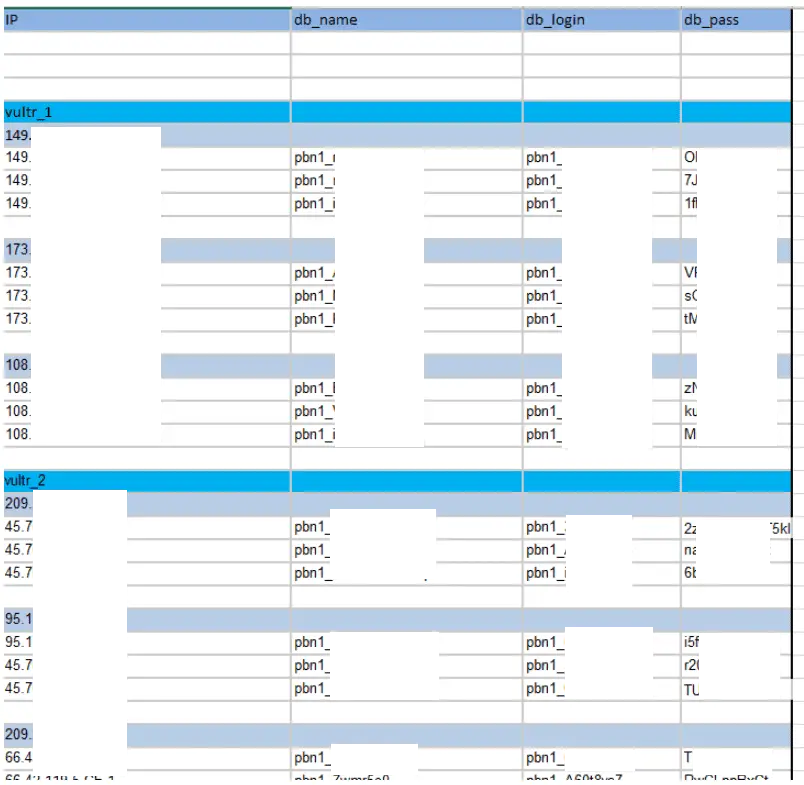
Credentials on Excel Sheets
Some people love to use Excel as a password manager.
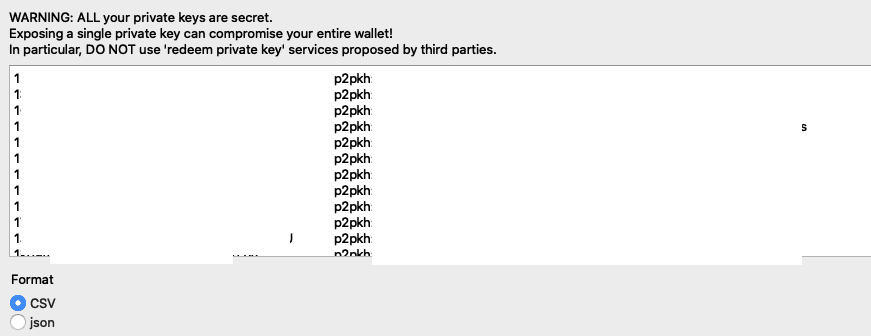
Bitcoin Private Keys (This is Terrible)
Bitcoin wallets allow you to export your private key so that you can import it somewhere else. But if you publish the screenshot of your private key, your whole wallet can be compromised.
Install & Use
Copyright (c) 2020, Utku Sen
All rights reserved.