ShowStopper: Anti-Debug tricks exploration tool
ShowStopper – Anti-Debug tricks exploration tool
The ShowStopper project is a tool to help malware researchers explore and test anti-debug techniques or verify debugger plugins or other solutions that clash with standard anti-debug methods.
With this tool, you can attach a debugger to its process and research the debugger’s behavior for the techniques you need (the virtual addresses of functions that apply to anti-debug techniques are printed to console) and compare them with their implementation. The tool includes a varied set of different techniques from multiple sources, including real-world malware and published documents and articles. The implemented techniques work for the latest Windows releases and for different modern debuggers.
Install
- Download the latest release and save the files not_suspicious.exe, ShowStopper.exe, and config.json to the same location.
- Run not_suspicious.exe from the command line
or
Double-click ShowStopper.exe.
How to use
Console application
The console application not_suspicious.exe has the following options:
To run the application, pass the path to a configuration file to it by using –config or -c options:
not_suspicious.exe --config <PATH_TO_JSON_CONFIGURATION>
To create a JSON configuration, see the corresponding section.
The option –auxiliary or -a lets you change the default behavior or the application and is usually used by the application itself or by the GUI.
The rest of the options allow you to manage how the application decides which techniques it will check and which it will not. By default, techniques that may crash debuggers or that need admin privilege are not executed. You can force the application to execute non-default techniques by specifying the corresponding options explicitly.
The following options are used:
| Option | Description |
|---|---|
| admin | Some techniques may work only with a certain privilege or in a process with a high integrity level. This means you must run the application with administrator privilege. |
| crash | These techniques not necessarily crash the debugger or the application itself. But after these techniques are applied, debugging is no longer possible. This option enables such techniques. The returns come back as “false” because the execution is no longer possible after they are applied. |
| trace | This option enables techniques that can succeed only if you trace through their code with a debugger. |
| break | These techniques usually check if there any breakpoints in the code. They may need to set a software, memory or hardware breakpoint either to a random or to a specific location. |
| attach | This option usually must be used with the “–crash” option. It enables anti-attach options that may make the debugger terminate its execution after it attaches to the application process. We recommend waiting until the application checks all the options and stops waiting for a key to be pressed. Then you can attach to it with a debugger and the debugger will exit. |
After you run the application from a console, it prints the addresses of techniques it will check:
Press any button to continue the execution. Before you get to this point, you can attach to this process with a debugger and set a breakpoint to the technique (using printed addresses) that you want to explore:
Finally, when the execution is resumed and all techniques are checked, the following output appears:
A result of “false” means that the debugger is not detected by using this technique. A result of “true” means that the debugger is detected.
GUI application
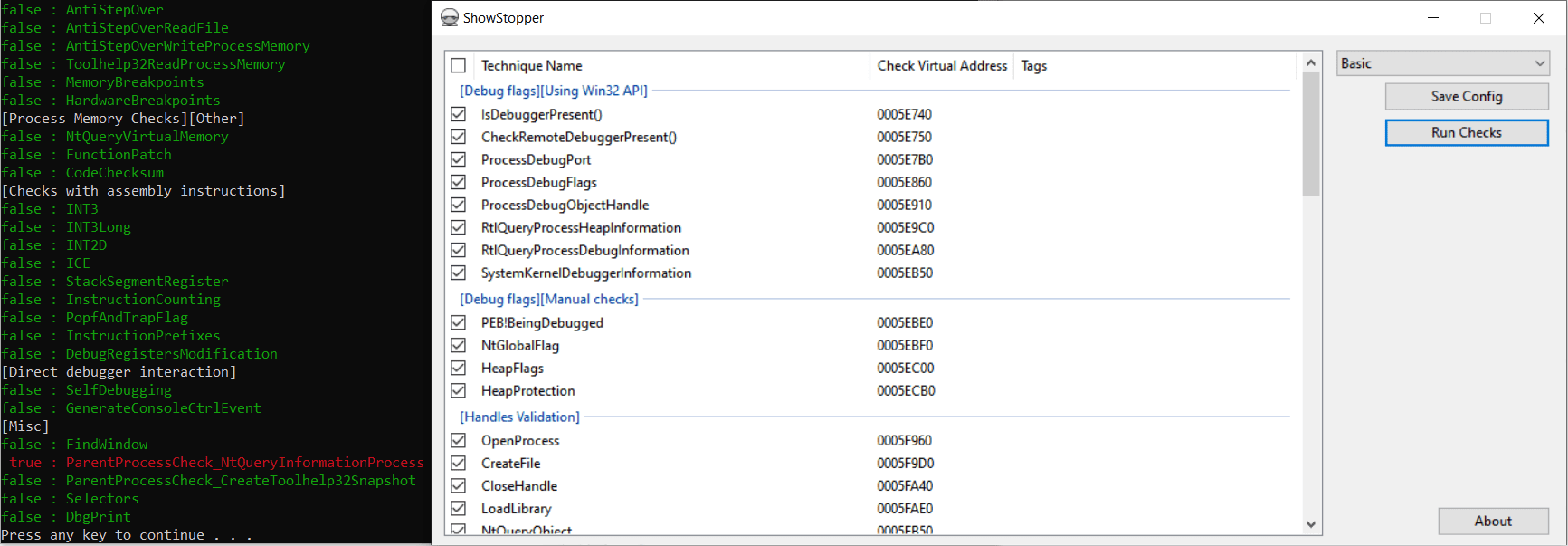
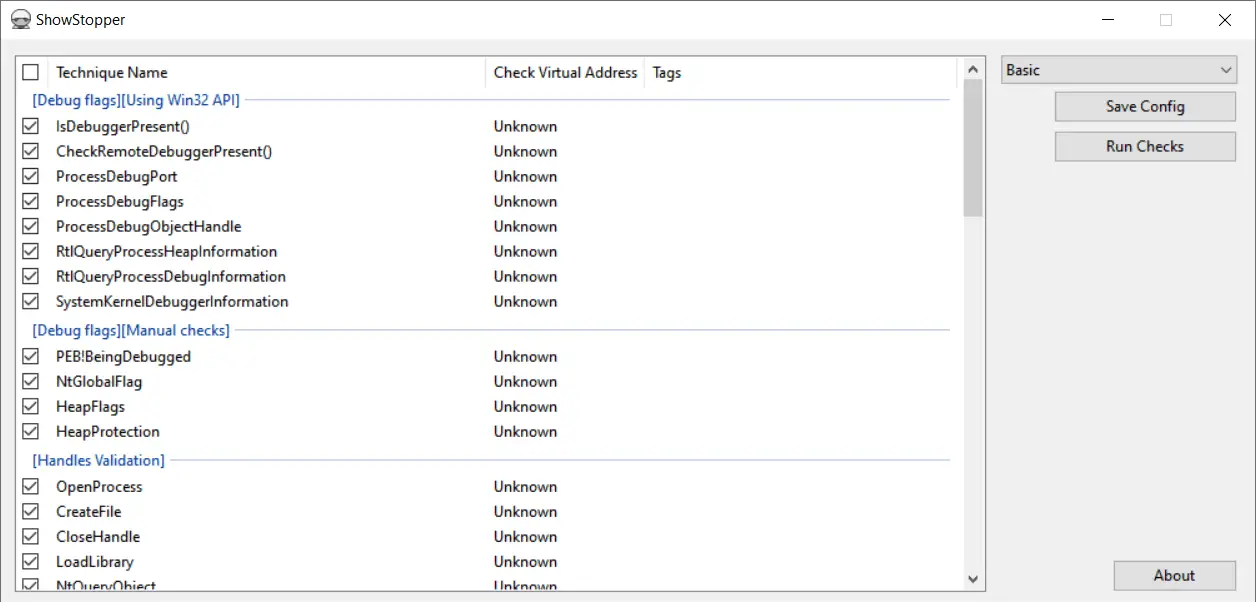
The GUI application ShowStopper.exe helps you manage which techniques you want to test and generates the configuration files.
In the application window, select techniques you want to test and execute them by clicking the Run Checks button.
To save the selected techniques in a configuration file, click the Save Config button.
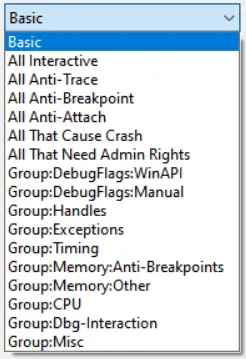
For your convenience, there is a list of options whose techniques can be selected at the same time.
Basic mode allows you to test the majority of anti-debug techniques that don’t require interaction with a debugger and high privilege.
All interactive mode enables only techniques that require setting a breakpoint, tracing their code, attaching to the process, etc.
The rest of the modes select techniques that work with certain command-line options (–trace, –break, etc.) and/or techniques of that specific group.
You can edit a technique’s parameters. To open the parameters editor window, double click on a technique in the table.
After running anti-debug checks, the GUI application passes the selected techniques to not_suspicious.exe using the –auxiliary option. The console application sends the GUI the virtual addresses of functions that apply the selected checks. You can attach a debugger to not_suspicious.exe while it is waiting for any key to be pressed, and set breakpoints to techniques you want to explore.
Copy addresses to the clipboard
You can copy a virtual address to the clipboard using right-click on the row with the corresponding technique.
Tutorial
Copyright (c) 2020 Check Point Software Technologies LTD.