Source: Seqrite Labs APT-Team
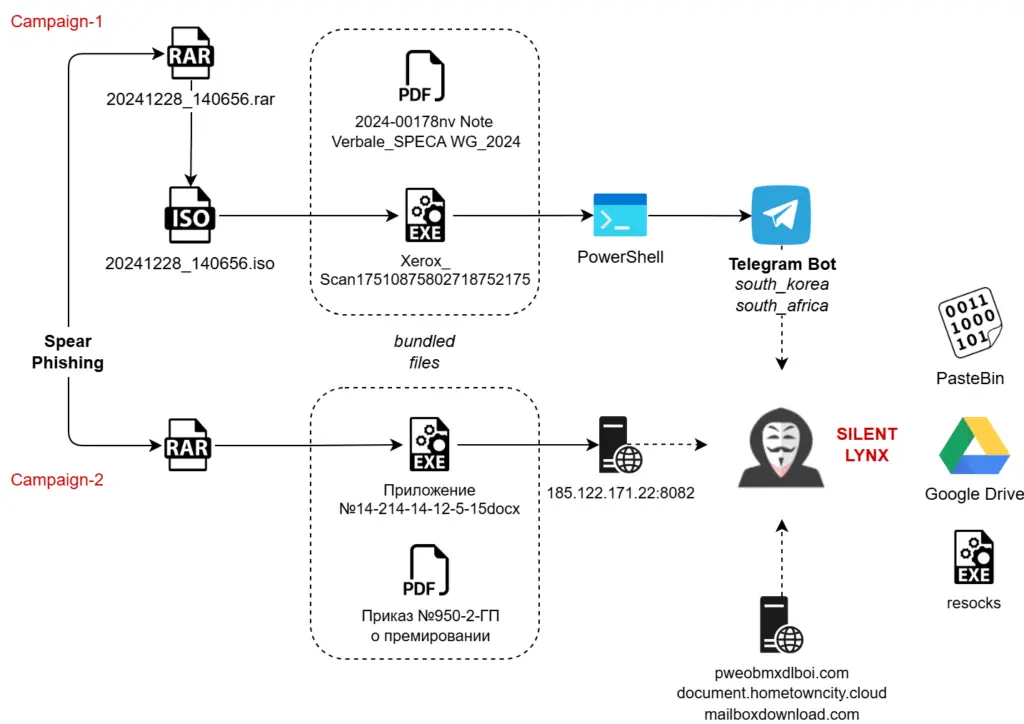
Seqrite Labs APT-Team has uncovered two sophisticated campaigns orchestrated by a newly identified threat group, Silent Lynx. This Kazakhstan-linked Advanced Persistent Threat (APT) group has been targeting government entities in Kyrgyzstan and neighboring nations, employing multi-stage attacks to gather intelligence on economic and diplomatic activities.
Silent Lynx has been observed targeting key entities, including embassies, government think tanks, and financial institutions, with a particular focus on nations involved in the Special Programme for the Economies of Central Asia (SPECA). Seqrite Labs reported, “This threat group has previously targeted entities around Eastern Europe and Central Asian government think tanks involved in economic decision making & banking sector.”
Their latest campaigns center on Kyrgyzstan, focusing on critical organizations such as the National Bank of the Kyrgyz Republic and the Ministry of Finance of Kyrgyzstan. The campaigns leverage spear-phishing emails as entry points, using decoy documents themed around United Nations events and government-issued employee bonuses to establish credibility.

The attack chain involves highly targeted phishing emails containing malicious RAR attachments. These attachments typically include either:
- Campaign 1: A malicious ISO file with a C++ loader and a decoy PDF.
- Campaign 2: A password-protected RAR file with a Golang-based reverse shell executable and a decoy MS Word document.
The decoy documents are meticulously crafted to appear authentic, such as an official invitation to the SPECA Working Group on Trade or a government order detailing employee bonuses. According to Seqrite Labs, “The document mimics legitimate communication from the United Nations Economic and Social Commission for Asia and the Pacific (ESCAP), leveraging the theme of “Leveraging Digitalization for Sustainable Supply Chains” to appear credible and relevant.”
Silent Lynx employs a blend of advanced techniques across different stages of their campaigns:
- Malicious Loaders: The ISO file in Campaign 1 contains a C++ binary with embedded Base64-encoded PowerShell commands. These commands enable unrestricted script execution using the ExecutionPolicy Bypass flag, creating a backdoor for further operations.
- PowerShell Bot: Once executed, the PowerShell script connects to a Telegram bot-based command-and-control (C&C) infrastructure. Functions such as Invoke-BotCmd and Invoke-BotDownload allow attackers to execute system commands and exfiltrate sensitive data. Seqrite Labs highlights that, “/cmd lets it execute system commands using the Invoke-BotCmd function, and /download triggers file uploads from the victim machine.”
- Golang Implants: Campaign 2 involves a Golang-based reverse shell that establishes persistence using the Windows Run registry key. The attackers further utilize commands like curl to download additional payloads from malicious domains such as hxxps://pweobmxdlboi.com.
The campaigns primarily aim to compromise diplomatic and governmental entities in Central Asia, with espionage as the primary objective. Sensitive files, including documents related to diplomatic operations between Kyrgyzstan and Turkmenistan, have been exfiltrated. One such document, “Turkmenistanyn Gyrgyz Respublikasyndaky Ilcihanasynyn meyilnamasy.docx,” suggests a focus on gathering intelligence on diplomatic plans.
Silent Lynx relies heavily on Telegram bots for C&C operations and data exfiltration. Seqrite Labs also uncovered overlaps with the Kazakhstan-based group YoroTrooper, as previously identified by Cisco Talos. Both groups exhibit similarities in their use of PowerShell tooling and their espionage-focused motivations. Seqrite Labs concludes with “medium” confidence that Silent Lynx originates from Kazakhstan and shares resources with YoroTrooper.
Related Posts:
- 20+ Victims and Counting: Lynx Ransomware’s Swift Rise
- Lynx Ransomware: The Evolution of INC Ransomware into a Potent Cyber Threat
- Silent Skimmer Reemerges: New Tactics Target Payment Gateways
- Operation Diplomatic Specter: Chinese State-Sponsored Cyber Espionage Campaign Targeting Governments Across Three Continents
- Google Ads Abused in Graphic Design Malvertising Attack