
Unit 42 researchers have detected renewed activity from a notorious financially motivated threat actor known as Silent Skimmer. This cybercriminal group, first identified in 2023, had seemingly faded into the shadows. However, in May 2024, the group resurfaced with a targeted attack on payment infrastructures of a North American-based multinational organization, revealing new methods to harvest payment data from compromised servers.
According to Unit 42, the attackers exploited vulnerabilities in Telerik UI to establish an initial foothold on the organization’s servers, leveraging two notable vulnerabilities, CVE-2017-11317 and CVE-2019-18935. These flaws, both on the CISA’s Known Exploited Vulnerabilities Catalog, allow remote code execution on vulnerable versions of Telerik UI. Once inside, Silent Skimmer’s operatives executed several reconnaissance commands to map out the environment and establish persistence.
After breaching the initial defenses, Silent Skimmer executed a range of tactics to maintain control over compromised systems. The threat actor dropped multiple web shells across directories to enable ongoing access. Researchers observed that “the attacker uploaded multiple web shells, mainly to directories like C:\Users\Public\Music\ and C:\WebRoot\Health Checks\Default,” thus planting persistent access points within the system. The attackers then introduced PowerShell reverse shells and other tunneling tools, such as Fuso and FRP, to allow remote access through compromised servers even when hidden behind firewalls.
To evade detection, Silent Skimmer employed a complex technique known as mixed-mode assemblies, which involves embedding native C++ code within .NET binaries. “The threat actor used .NET binaries with native C++ code embedded by leveraging mixed mode assemblies,” making it challenging for standard analysis tools to detect the malicious payload, as these .NET tools often fail to analyze the unmanaged code within the binary.
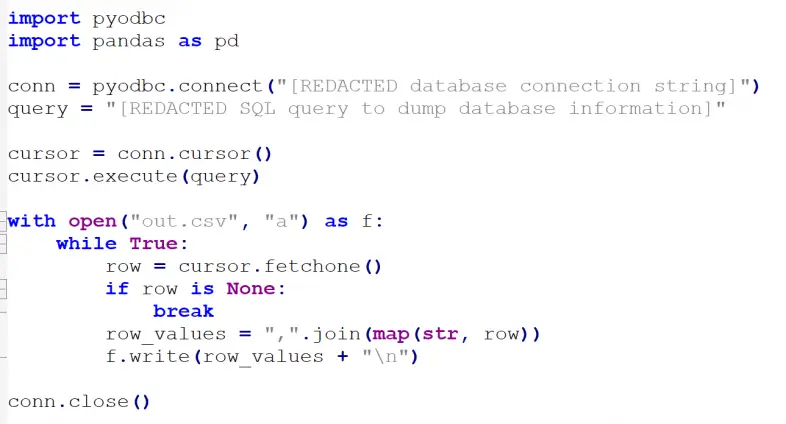
Furthermore, Silent Skimmer was observed to use compiled Python scripts to access the payment database directly. With these scripts, the attackers could log into the database using hardcoded credentials and exfiltrate payment information by exporting it to a CSV file. This shift marks a change from the group’s previous method, where they injected malicious code directly onto payment pages to skim data.
Unit 42 noted overlaps in tactics between this incident and previous campaigns. The research team pointed out that “a significant number of the TTPs we observed in our investigation align with the ones described in BlackBerry’s blog starting from the initial access vector, which is the exploitation of publicly facing web servers” highlighting the group’s consistent use of Telerik vulnerabilities and reverse shells. Additionally, Silent Skimmer leveraged GodPotato for privilege escalation, enabling deeper access within the compromised systems.
Unit 42 concludes that “this persistence underscores the need for organizations to stay vigilant and patch vulnerabilities promptly to defend against this enduring threat,” as Silent Skimmer’s updated tactics pose a severe risk to unprotected systems
Related Posts:
- Researcher Exposes WebSockets’ Role in Credit Card Skimming
- Cyberattack on Magento: Hackers Inject Skimmer, Card Data Stolen
- WooCommerce Skimmer Employs Stealthy Tactics to Pilfer Card Data
- PrestaShop Websites Under Attack: GTAG Websocket Skimmer Steals Credit Card Data