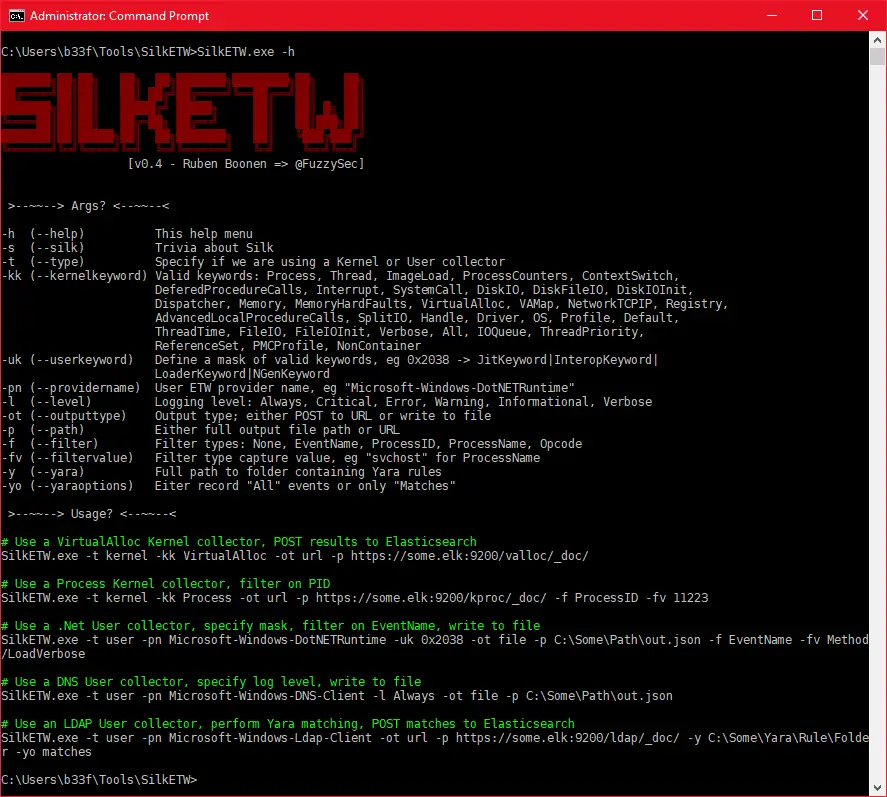
SilkETW
SilkETW is a flexible C# wrapper for Event Tracing for Windows (ETW), it is meant to abstract away the complexities of ETW and give people a simple interface to perform research and introspection. While SilkETW has obvious defensive (and offensive) applications it is primarily a research tool in its current state.

For easy consumption, output data is serialized to JSON. The JSON data can either be analyzed locally using PowerShell or shipped off to 3rd party infrastructure such as Elasticsearch.
Changelog v0.8
- * Bugfix: https://github.com/fireeye/SilkETW/issues/4
- * Bugfix: https://github.com/fireeye/SilkETW/issues/5
Usage
Filter data in PowerShell
You can import JSON output from SilkETW in PowerShell using the following simple function.
In the example below, we will collect process event data from the Kernel provider and use image loads to identify Mimikatz execution. We can collect the required data with the following command.
SilkETW.exe -t kernel -kk ImageLoad -ot file -p C:\Users\b33f\Desktop\mimikatz.json
With data in hand it is easy to sort, grep and filter for the properties we are interested in.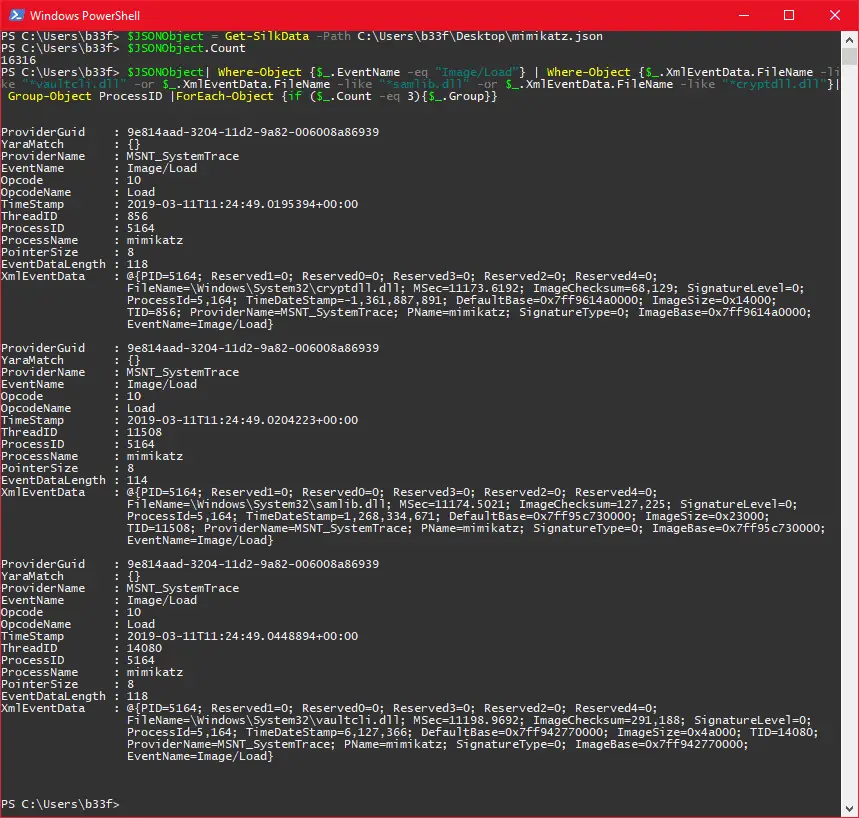
Yara
SilkETW includes Yara functionality to filter or tag event data. Again, this has obvious defensive capabilities but it can just as easily be used to augment your ETW research.
In this example, we will use the following Yara rule to detect Seatbelt execution in memory through Cobalt Strike’s execute-assembly.
We can start collecting .Net ETW data with the following command. The “-yo” option here indicates that we should only write Yara matches to disk!
SilkETW.exe -t user -pn Microsoft-Windows-DotNETRuntime -uk 0x2038 -l verbose -y C:\Users\b33f\Desktop\yara -yo matches -ot file -p C:\Users\b33f\Desktop\yara.json
We can see at runtime that our Yara rule was hit.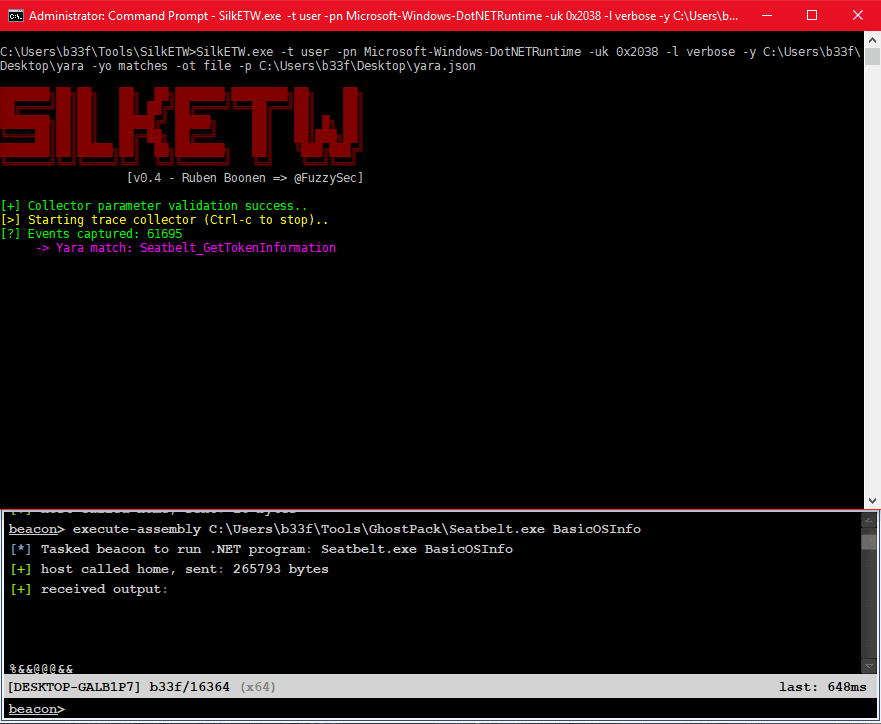
Note also that we are only capturing a subset of the “Microsoft-Windows-DotNETRuntime” events (0x2038), specifically: JitKeyword, InteropKeyword, LoaderKeyword and NGenKeyword.
Download
Copyright 2019 FireEye, Inc. Developed by Ruben Boonen