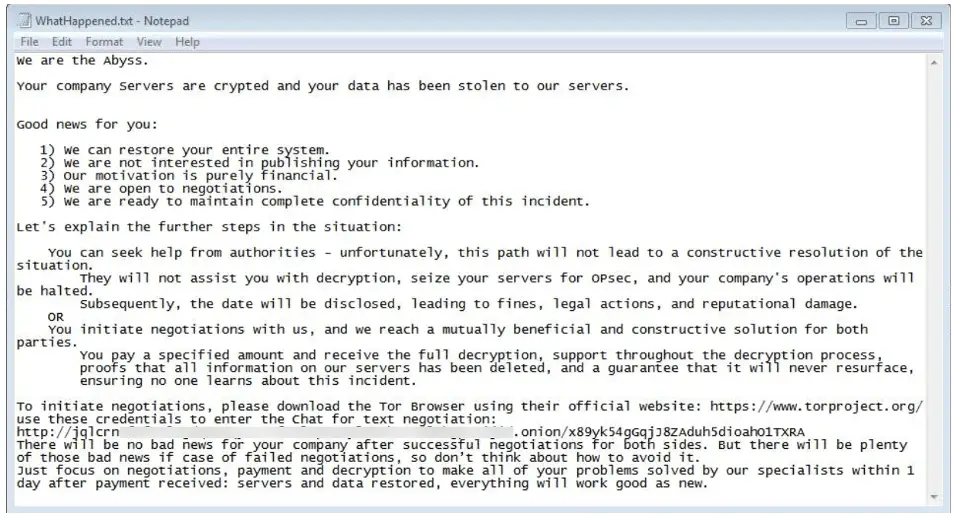
Ransom note dropped by the Abyss Locker ransomware version 1 for Windows
A security researcher averted significant financial losses for six companies that could have fallen victim to cyberattacks. Vangelis Stykas, the Chief Technical Officer of Atropos.ai, uncovered vulnerabilities within the infrastructure of several ransomware groups, allowing him to infiltrate the hackers’ systems and assist the companies.
Two organizations received decryption keys without having to pay the hackers, while four cryptocurrency firms were alerted to impending attacks before their files could be encrypted. These actions were made possible by simple yet critical errors in the hackers’ code.
Stykas conducted research aimed at identifying servers used by more than 100 groups specializing in extortion and data leaks. He discovered several critical vulnerabilities in the web interfaces utilized by at least three ransomware groups. These flaws allowed him to infiltrate the hackers’ internal systems and access valuable information about their operations.
One such flaw was the Everest group’s use of a default password to access their SQL databases. Another example was unsecured APIs, which exposed the targets of BlackCat’s attacks. In some cases, these errors revealed the IP addresses of the hackers’ servers, enabling the tracking of their real-world locations.
Stykas also exploited an IDOR vulnerability to gain access to all the messages in the Mallox group’s admin chat. These messages contained two decryption keys, which Stykas later provided to the affected companies. He also managed to identify several members of the group.
The affected entities included both small businesses and large cryptocurrency firms valued at over a billion dollars. Despite this, the companies have yet to publicly disclose information about the incidents, though Stykas did not rule out the possibility that their names may be revealed in the future.
Although attacks on ransomware sites can yield certain results, Stykas emphasizes that this is not the most effective way to combat cyber threats. Such operations may be useful for governments or large companies with substantial resources. For ordinary users, these attacks are more likely a waste of time.
Via: TechCrunch