Siofra: DLL Hijacking Vulnerability Scanner and PE Infection Tool
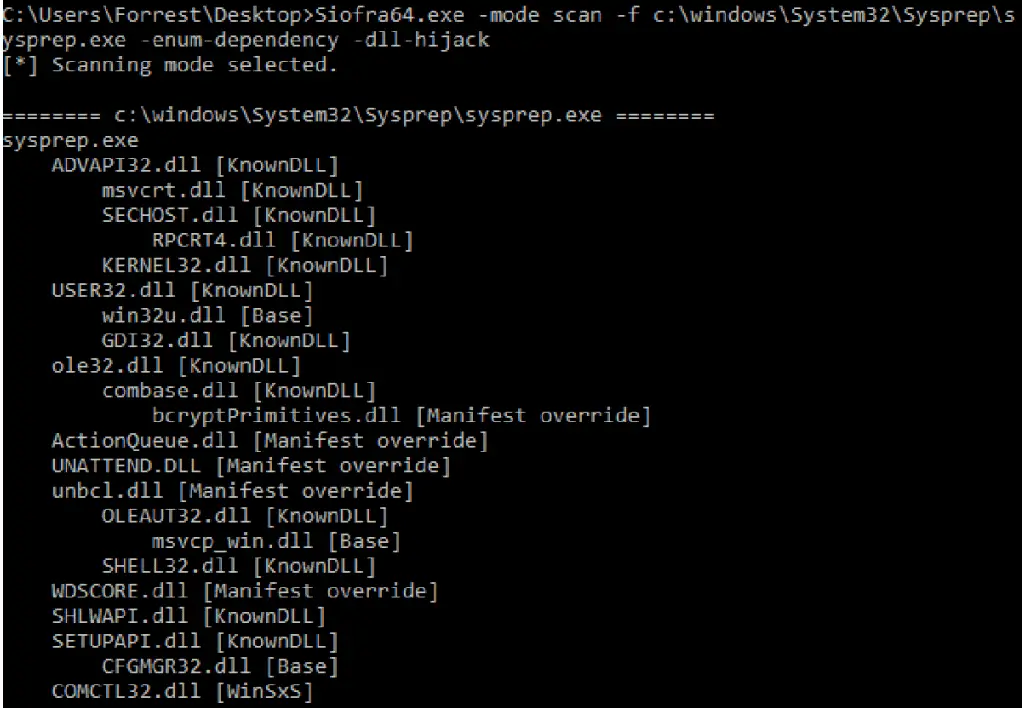
Siofra is a tool designed to identify and exploit DLL hijacking vulnerabilities in Windows programs. It is able to simulate the Windows loader in order to give visibility into all of the dependencies (and corresponding vulnerabilities) of a PE on disk, or alternatively an image file in memory corresponding to an active process. More significantly, the tool has the ability to easily generate DLLs to exploit these types of vulnerabilities via PE infection with dynamic shellcode creation. These infected DLLs retain the code (DllMain, exported functions) as well as the resources of a DLL to seamlessly preserve the functionality of the application loading them, while at the same time allowing the researcher to specify an executable payload to be either run as a separate processor loaded into the target as a module. Additionally, the tool contains automated methods of combining UAC auto-elevation criteria with the aforementioned functionality in order to scan for UAC bypass vulnerabilities.
Siofra was written to provide everything a security researcher would need in order to both identify and exploit DLL hijacking vulnerabilities within a single utility.
The capabilities of this tool can be divided into two categories (intended for the two stages of carrying out this genre of attack):
- Scanner mode, meant for identifying vulnerabilities in the desired target program (or set of programs) during the reconnaissance phase of an attack.
- Infection mode, meant for infecting legitimate copies of the vulnerable modules identified during the reconnaissance phase of an attack for payload delivery during the exploitation phase of an attack.
Download
git clone https://github.com/Cybereason/siofra.git
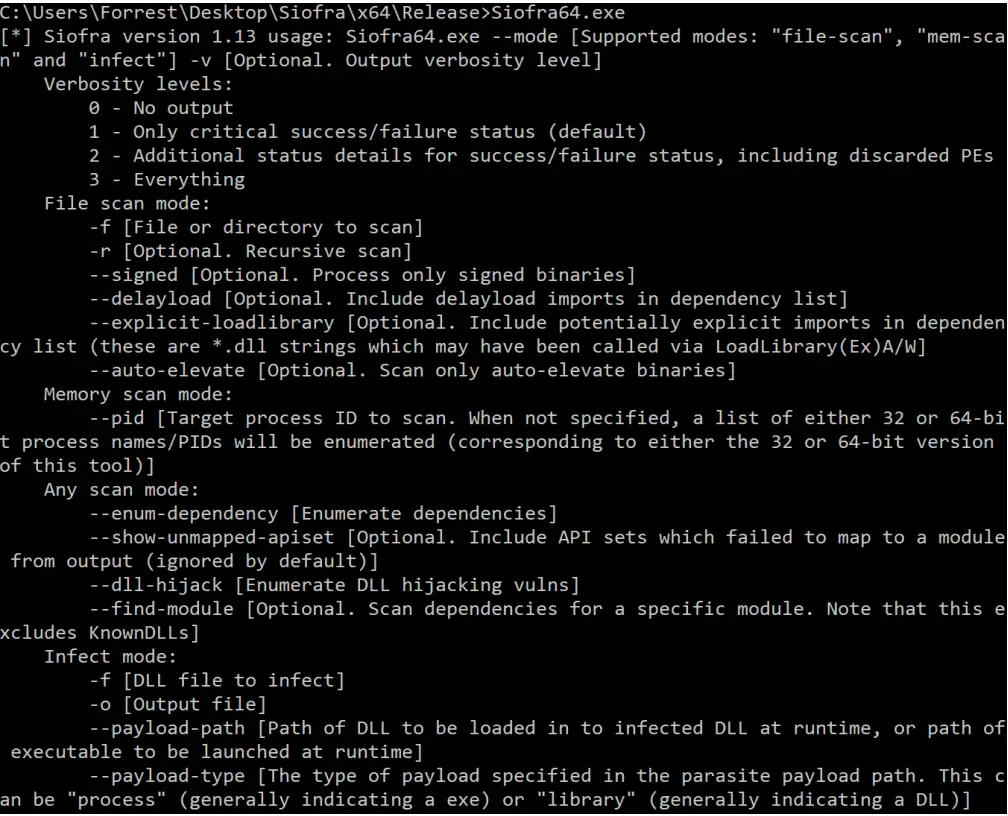
Use
Copyright (C) 2017 Cybereason
Source: https://github.com/Cybereason/





