SMBSR: Lookup for interesting stuff in SMB shares
SMBSR – what is that?
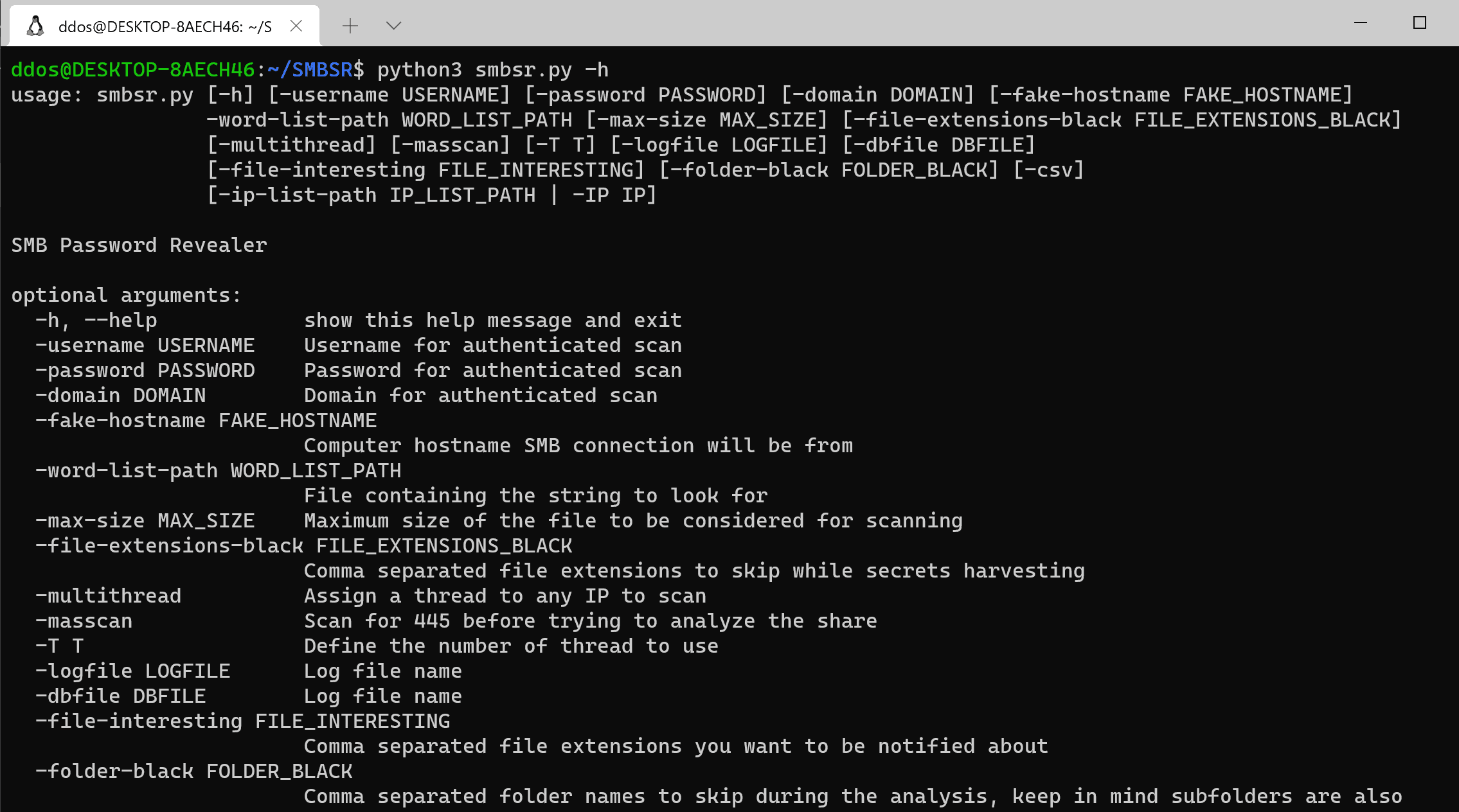
Well, SMBSR is a python script which given a CIDR/IP/IP_file/HOSTNAME(s) enumerates all the SMB services listening (445) among the targets and tries to authenticate against them; if the authentication succeeds then all the folders and subfolders are visited recursively in order to find secrets in files and … secret files. In order to scan the targets for SMB ports open the masscan module is used. SMBSR considers something interesting based on its:
- Content
- Exstension
- Name
The interesting keywords the tool should look for are defined via the command line as well as:
- File extension blacklist
- Folder blacklist (Watch out, also subfolders are gone)
- Number of Threads
- Should i masscan or not?
- Interesting file extensions (I guess something like ppk, kdbx, …)
- Maximum file size allowed to be checked (Believe me, too big might take some time)
- Should i export the results in two nice CSV files?
- Other common ones and required
Of course, everything is saved locally in an SQlite Database. The database contains one table for the “hopefully it’s a DA password” match, called smbsr containing the following columns:
- file
- share
- ip
- position
- matchedWith
- Creation Date
- Last Modified Date
- Last Accessed Date
And also another table for the interesting file list containing the following columns:
- file
- share
- ip
- Creation Date
- Last Modified Date
- Last Accessed Date
Install
git clone https://github.com/oldboy21/SMBSR.git
pip3 install -r requirements.txt
Use

Copyright (C) 2021 oldboy21
Source: https://github.com/oldboy21/





