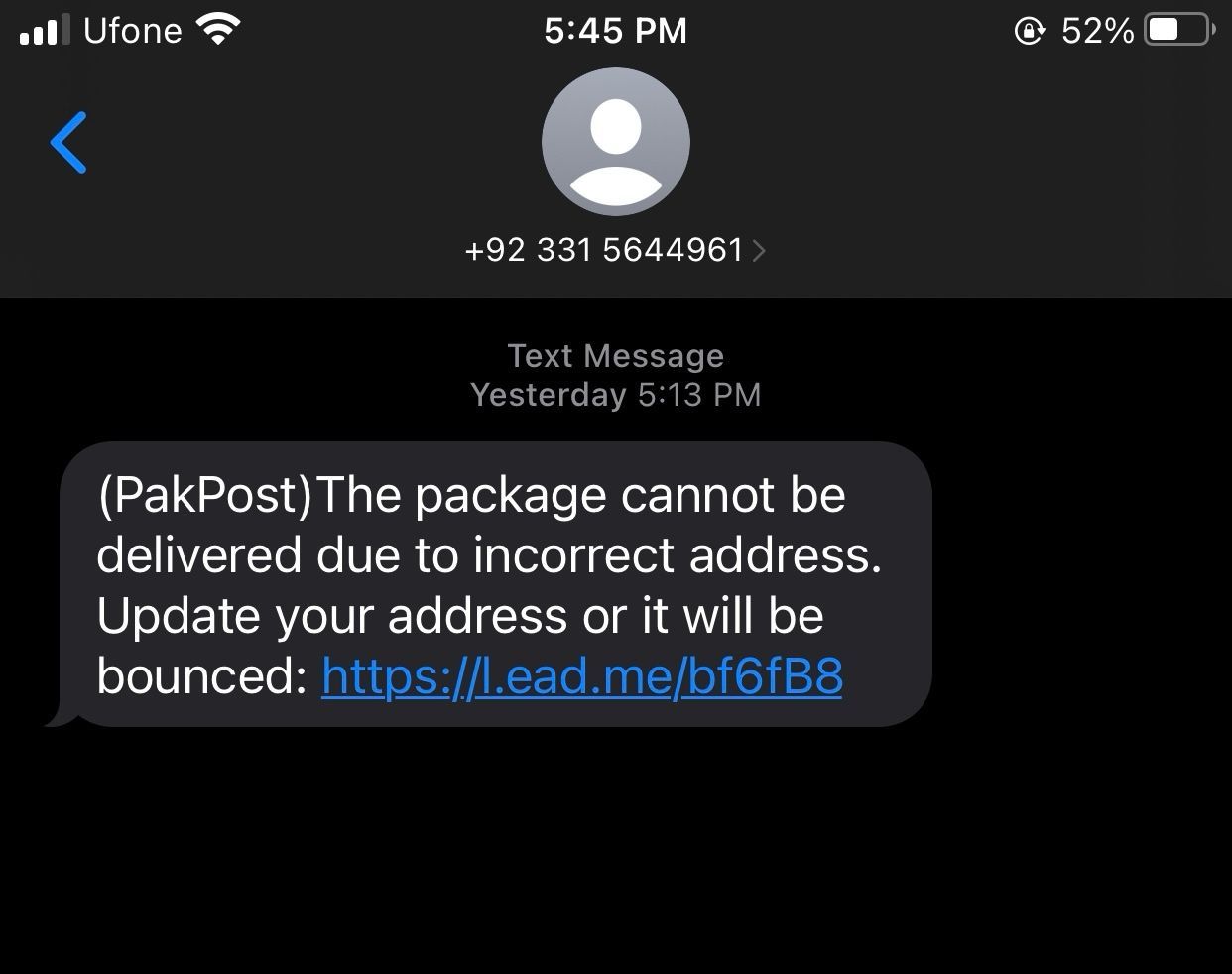
Cybersecurity firm Resecurity has disclosed a sophisticated smishing campaign targeting customers of major Pakistani mobile carriers. The threat actor group, dubbed “Smishing Triad,” is leveraging stolen personal data and impersonating Pakistan Post to conduct fraudulent activities on a massive scale.
Malicious Tactics
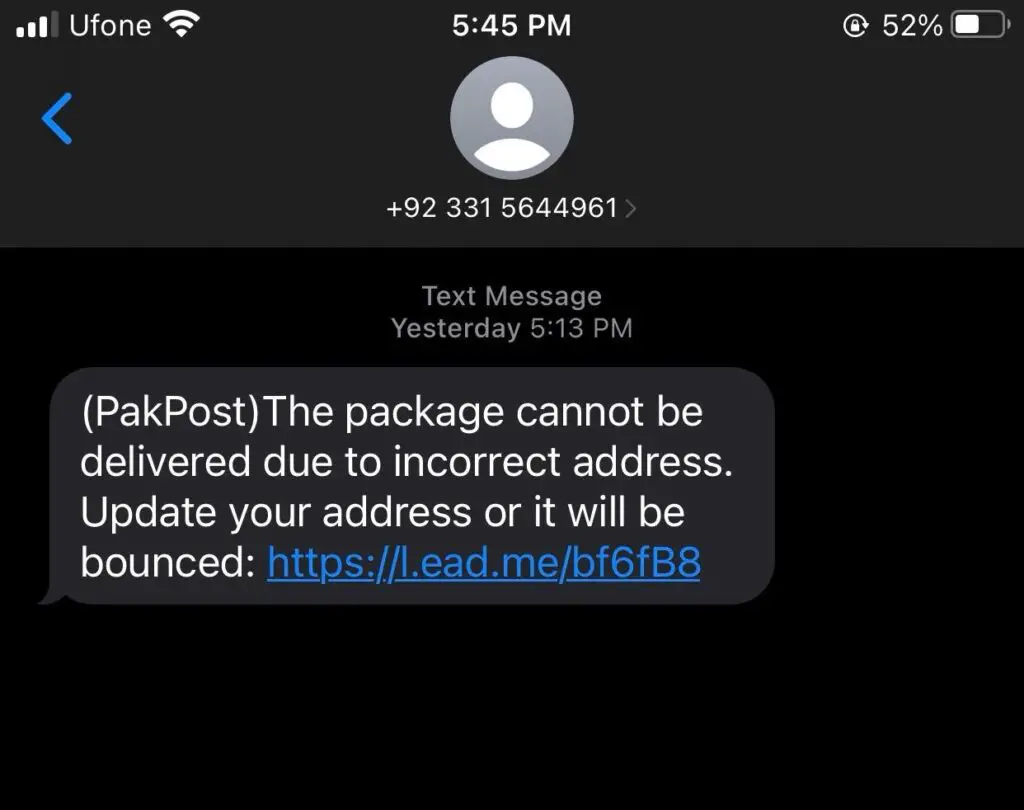
Resecurity estimates that the Smishing Triad is sending between 50,000 and 100,000 malicious SMS and iMessage messages daily. The messages, which appear to be from Pakistan Post or mobile carriers like Jazz/Warid, Zong, Telenor Pakistan, and Ufone, contain phishing links leading to fake payment forms. Unsuspecting victims are then tricked into providing their credit card information, which is subsequently used for fraudulent purposes.
The widespread nature of this campaign is attributed to the exploitation of stolen databases containing sensitive personal information, including phone numbers. These databases, likely acquired from recent data breaches in Pakistan, are processed using automation tools to facilitate targeted attacks.
Modus Operandi
The group utilizes various tactics to evade detection, including URL shortening services and QR codes. They also use local phone numbers to appear more legitimate. Some messages require victims to reply, allowing the attackers to verify active numbers for further targeting.
Previous Activity
This isn’t the Smishing Triad’s first campaign. Resecurity has linked the group to similar attacks targeting Correos, the Spanish postal service, in the past. Evidence suggests the group is still targeting European victims as well.
Mitigation Measures
Resecurity urges Pakistani telecom operators to bolster their fraud detection systems and proactively block these malicious messages. They also recommend that users remain vigilant and follow these tips to protect themselves:
- Be skeptical of unsolicited messages: Verify the source before clicking any links or providing personal information.
- Don’t respond: Ignoring suspicious texts is the simplest defense.
- Report suspicious activity: Alert your mobile carrier of any smishing attempts.