SnailLoad (CVE-2024-39920): New Side-Channel Attack Exposes Your Web Activity
Security researchers from Graz University of Technology have unveiled a novel cybersecurity threat dubbed “SnailLoad” (CVE-2024-39920). This side-channel attack exploits a vulnerability in the Transmission Control Protocol (TCP), potentially allowing attackers to remotely monitor a user’s web activity, including visited websites and streamed videos.

How SnailLoad Works
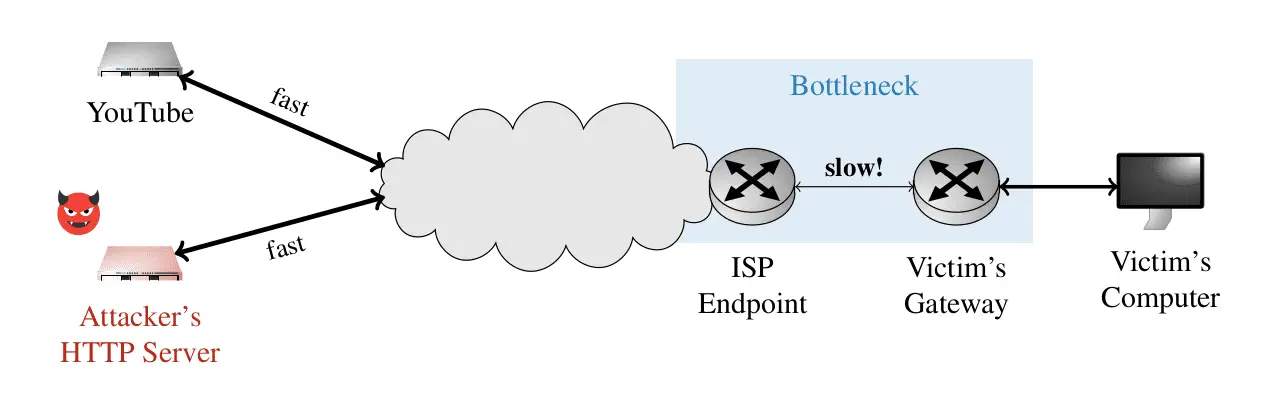
SnailLoad exploits a timing side channel within the TCP protocol, as specified in RFC 9293. This timing side channel enables remote attackers to deduce the content of a TCP connection from a client system to any server when that client system is simultaneously receiving TCP data at a slow rate from an attacker-controlled server. The attack operates by measuring round-trip times (RTTs) through TCP segments that provide an acknowledgment control bit and an acknowledgment number.
The critical aspect of CVE-2024-39920 is its ability to leverage the inherent bandwidth bottleneck present in all Internet connections. This bottleneck affects the latency of network packets, allowing an attacker to infer ongoing network activities, such as the websites a user visits or the videos they watch.
Are You at Risk?
The researchers believe most internet connections are susceptible to this attack, as it leverages common bandwidth bottlenecks present in home networks. However, the attack is currently unlikely to be exploited in the wild. In a user study, the researchers achieved varying levels of accuracy in identifying specific video content across different internet connections.
Mitigations
Addressing the root cause of SnailLoad is challenging, as it relies on fundamental differences in bandwidth between backbone networks and individual user connections. Disabling TCP ACKs, which are crucial for reliable data transmission, is not a viable solution. Further research is needed to develop effective mitigations.
Proof-of-Concept and Future Implications
The researchers have released a basic SnailLoad example server on GitHub, providing a proof-of-concept for the attack. This move underscores the need for the cybersecurity community to prioritize addressing such vulnerabilities and developing robust defenses.
What You Can Do
While there are no immediate fixes, staying informed about this emerging threat is essential. Be cautious of suspicious network activity and prioritize security best practices.