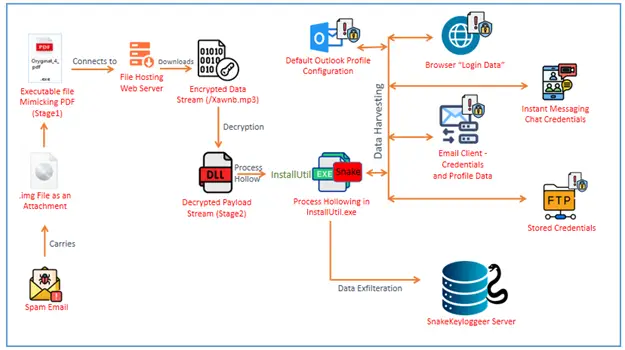
Attack Chain of SnakeKeylogger | Image: Seqrite Labs
A new report from Seqrite Labs details a malicious campaign employing SnakeKeylogger, an info-stealing malware known for its advanced techniques and ability to evade detection. The report highlights SnakeKeylogger’s multi-stage infection chain and stealthy in-memory execution, designed to harvest sensitive data from unsuspecting victims.
The infection vector is as deceptive as it is effective. Victims receive malicious spam emails containing .img attachments, which, when opened, mount a virtual drive:
“The file inside this .img is an executable file (Stage1), masquerading as a PDF document with a file Icon and name carefully chosen to resemble an important PDF document.”
This initial executable (Stage1) functions as both a downloader and loader. Upon execution, it reaches out to a remote Apache server to fetch what appears to be a media file—typically a .mp3. But beneath the surface lies something more insidious.
Instead of a media stream, the malware retrieves an encoded payload that is dynamically decrypted in memory:
“At first glance looking at the URL, it appears to be fetching a simple media file (*.mp3)… However, closer inspection reveals that this is not a media file but rather a disguised encoded payload.”
Using a simple decryption routine—subtracting 3 from each byte—the downloader reconstructs a secondary payload (Stage2), a highly obfuscated .NET-based DLL. This DLL is injected into legitimate system processes via process hollowing, specifically targeting InstallUtil.exe.
“InstallUtil.exe is a legitimate Windows utility… Process hollowing is a sophisticated technique where a new process is spawned… and malicious code is written into the hollowed space.”
Once injected, SnakeKeylogger activates its core capabilities—stealing credentials and system data. The malware is programmed to extract Wi-Fi configuration data, browser-stored credentials, email account settings, and more.
SnakeKeylogger digs deep into systems, targeting a vast number of applications including:
- Browsers like Chrome, Edge, Firefox, Brave, Opera, and even niche variants like Citrio, Torch, and Kinza.
- Email clients such as Outlook, Thunderbird, and Postbox.
- FTP clients like FileZilla.
- Chat apps such as Pidgin.
The malware campaign appears to be part of a larger Malware-as-a-Service (MaaS) operation. The Apache server at 103.72.56.30 hosts a directory named /PHANTOM/, which the attackers frequently update with new payloads:
“Attackers regularly upload and rotate files… allowing attackers to update their payloads while maintaining a stable infrastructure.”
This strategy ensures longevity and adaptability—enabling attackers to evolve faster than defenders can react.
SnakeKeylogger is not just another info-stealer—it’s a modular, evasive, and actively maintained threat that adapts to modern security defenses. Its campaign highlights the increasing sophistication of malware distribution tactics and the importance of layered defense strategies.
As Prashil Moon concludes in his report, “Attackers are actively maintaining and updating encrypted malicious payloads… a tactic commonly used in Malware-as-a-Service operations.”