snallygaster v0.0.12 releases: scan for secret files on HTTP servers
snallygaster
Tool to scan for secret files on HTTP servers.
snallygaster is a tool that looks for files accessible on web servers that shouldn’t be public and can pose a security risk.
Typical examples include publicly accessible git repositories, backup files potentially containing passwords or database dumps. In addition, it contains a few checks for other security vulnerabilities.
As an introduction to these kinds of issues you may want to watch this talk:
An overview of tests provided by snallygaster:
| TEST | Type | Description |
| Default tests (These tests are enabled by default and usually output information that directly leads to potential vulnerabilities.) | lfm_php | This checks for Lazy File Manager, a one-file php script that allows arbitrary file operations. It is often placed on compromised webpages. |
| idea | Configuration file for JetBrains, can contain passwords. | |
| symphony_databases_yml | Database configuration file (databases.yml) used by older versions of Symphony. These aren’t supposed to be stored within the web root, but sometimes they are. | |
| rails_database_yml | Database configuration file (database.yml) used by Ruby on Rails. Misconfigurations can cause these to be readable. | |
| git_dir | When deploying web pages with a Git repository the .git directory may end up being publicly readable. This allows downloading the full repository. | |
| svn_dir | Identical to git_dir issue, just with Subversion instead of Git. | |
| cvs_dir | Identical to git_dir issue, just with CVS instead of Git. | |
| apache_server_status | Apache server-status pages. These can contain visitor URLs and IP addresses of visitors. | |
| Coredump | Crashing processes on Linux and other unix systems can leave a memory dump file named “core” that may leak information like passwords. | |
| sftp_config | Configuration file from the FTP client sublime FTP (sftp-config.json). It turns out sometimes people accidentally upload the configuration file of their FTP client, including credentials for their web space. | |
| wsftp_ini | Similar to sftp_config, but for WS_FTP. | |
| filezilla_xml | Similar to sftp_config, but for FileZilla. | |
| winscp_ini | Similar to sftp_config, but for WinSCP. | |
| ds_store | The Apple OS X file manager Finder creates these files. They may leak directory and file names. | |
| Backupfiles | Backup files and other leftovers from editors. Many editors create files with a ~ or .bak extension when overwriting a previous version. VIM creates swap files of the scheme .[filename].swp. On crashes EMACS creates #[filename]#. All of these are particularly problematic in combination with PHP, as a file that may contain secrets will end up on the webspace without a .php extension and thus won’t be parsed. | |
| Deadjoe | The editor JOE creates a file DEADJOE on crashes, which contains content of the currently edited files. Similar to backupfiles.
|
|
| sql_dump | This checks for common names of SQL database dumps. These can lead to massive database leaks. | |
| bitcoin_wallet | This scans for bitcoin wallets (wallet.dat) left on servers. While this is rare, obviously leaking those can come at a high cost. | |
| drupal_backup_migrate | The Drupal backup_migrate plugin stores backups of the CMS database in the web folder. Access is prevented with an Apache .htaccess file, but that does not work on other web servers. | |
| magento_config | Magento is a PHP web store that saves its config (including database credentials) in an XML file called “local.xml”. Access is prevented with an Apache .htaccess file, but that does not work on other web servers. | |
| Xaa | xaa files are the output of the “split” command line tool on Unix systems. It’s used to split large files. As large files often contain lots of data these may lead to large leaks (similar to sql_dump). | |
| Optionsbleed | A test for the Optionsbleed vulnerability, in which Apache corrupts the “Allow” header in a reply to an HTTP OPTIONS request. | |
| Privatekey | Checks for private keys, usually belonging to TLS/X.509 certificates. | |
| Sshkey | Similar to the privatekey check this looks for SSH private keys on web servers. | |
| Dotenv | This looks for Laravel “.env” files that may contain database credentials. | |
| Invalidsrc | This checks all src-references on a webpage’s HTML and looks for inaccessible references. These may indicate domain takeover vulnerabilities. This test produces warnings quite often, though many of them are harmless: References to deleted files or simply syntax errors in URLs. | |
| ilias_defaultpw | This checks installations of the Ilias e-learning software for the presence of a default username/password (root/homer). Ilias was involved in the 2018 hack of the German government, though it’s unclear what vulnerability was used. | |
| Cgiecho | The cgiecho tool is part of the unmaintained software cgiemail. It contains a vulnerability where it allows leaking arbitrary files from the web root if they contain any guessable string in square brackets (e.g. [‘password’]). | |
| phpunit_eval | Tests for a remote code execution vulnerability in a script shipped with older versions of phpunit that will simply pass the POST data to PHP’s eval. | |
| Axfr | Checks if name servers answer to AXFR zone transfer requests. These are usually never intended to be publicly accessible. | |
| Info tests (These tests are enabled with the “-i” parameter. They output information about a site that may be valuable for analysis, but does not directly indicate a security problem.) | drupal | Checks for the presence of the Drupal CMS and outputs the version. |
Changelog v0.0.12
-
Adds one more exception that the HTML parser could raise.
-
Some minor coding style fixes.
Installation
pip3 install snallygaster
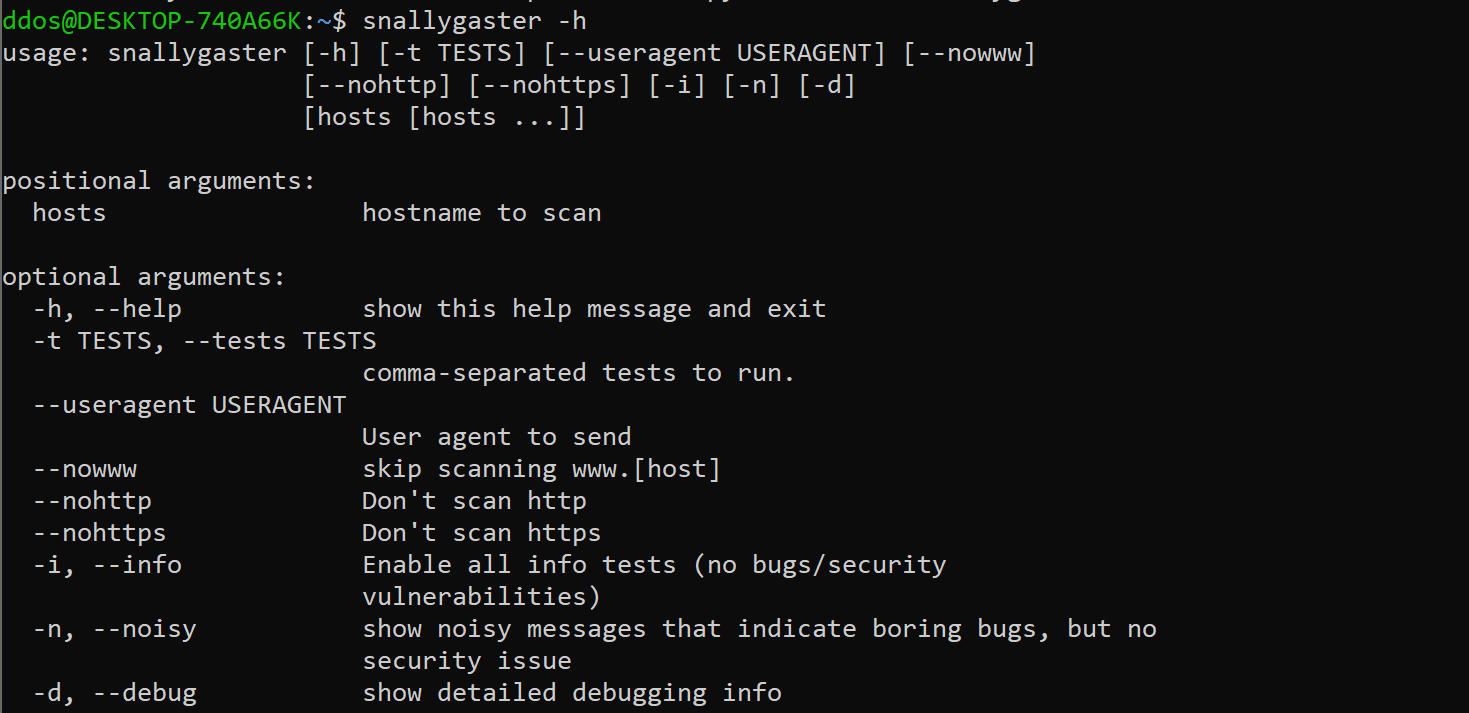
Use

Author: Hanno Böck.
Source: https://github.com/hannob/





