snare: Super Next generation Advanced Reactive honEypot
SNARE
Super Next-generation Advanced Reactive honEypot
It is a web application honeypot sensor attracting all sort of maliciousness from the Internet.

Getting started
- You need a Python3. We tested primarily with >=3.4
- This was tested with a recent Ubuntu based Linux.
Steps to setup
- Clone the repo:
git clone https://github.com/mushorg/snare.git && cd snare
- Install requirements:
pip3 install -r requirements.txt - Setup:
sudo python3 setup.py install - Clone a page:
sudo clone –target http://example.com - Run:
sudo snare --port 8080 --page-dir example.com
- Test: Visit http://localhost:8080/index.html
- (Optionally) Have your own tanner service running.
[Note: Cloner clones the whole website, to restrict to a desired depth of cloning add –max-depth parameter]
You obviously want to bind to 0.0.0.0 and port 80 when running in production.
Use
The command line parameters
Description
- page–dir – name of the folder to be served
- list–pages – list available pages
- host–ip – host ip to bind to, default: localhost
- index–page – file name of the index page, default: index.html
- port – port to listen on, default: 8080
- interface – interface to bind to
- debug – run web server in debug mode, default: False
- tanner – ip of the tanner service, default: tanner.mushmush.org
- skip–check-version – skip check for update
- slurp–enabled – enable nsq logging
- slurp–host – nsq logging host, default: slurp.mushmush.org
- slurp–auth – nsq logging auth, default: slurp
- config – snare config file, default: snare.cfg
- auto–update – auto update SNARE if new version available, default: True
- update–timeout – update SNARE every timeout (possible labels are: D – day, H– hours, M – minutes), default: 24H
- server–header – set server header, default: nginx
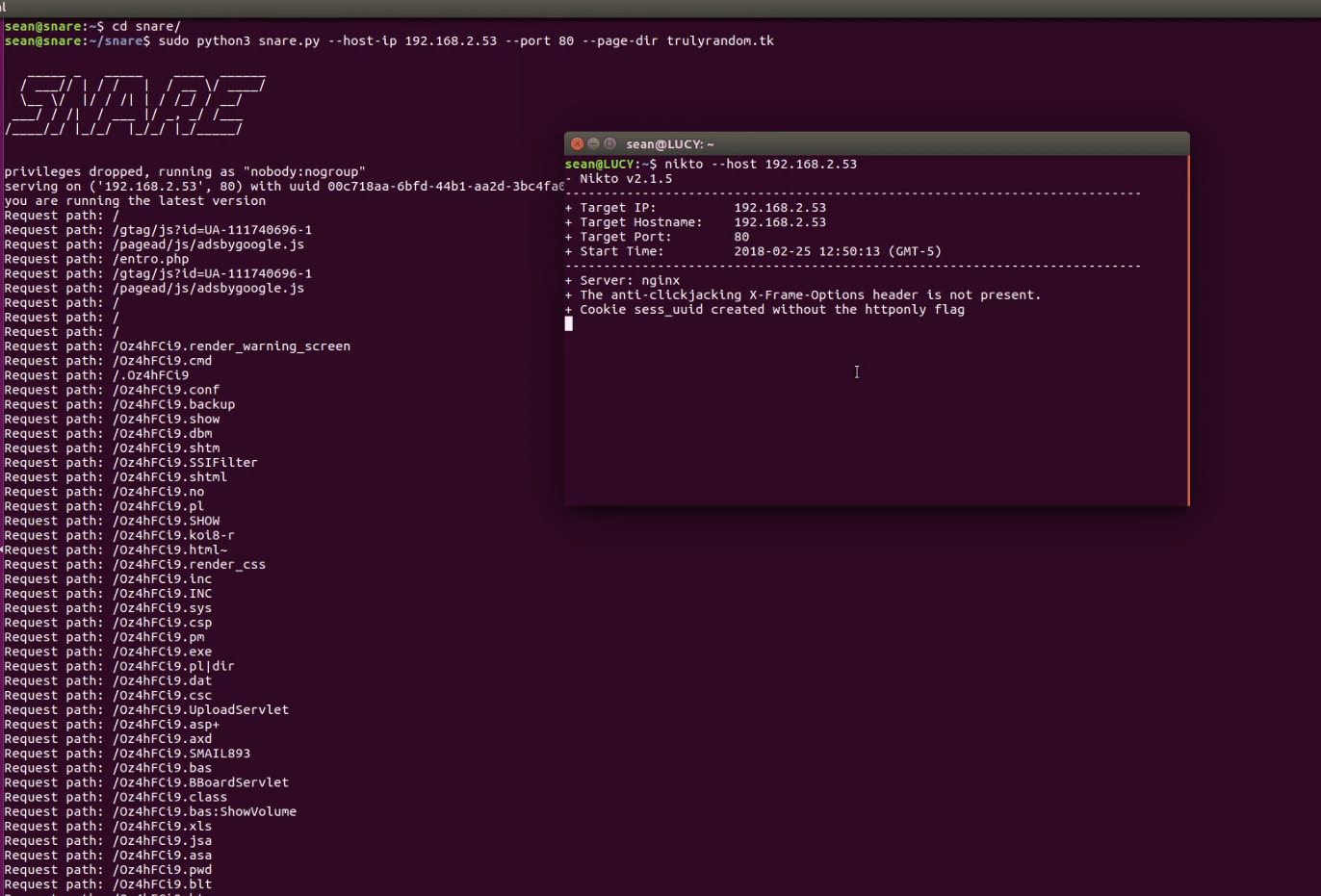
Demo
Copyright (C) ©2016, mushorg