Infection chain abuse SFX RAR as the initial attack vector
A newly identified espionage group dubbed “SneakyChef” has been targeting government agencies in Europe, the Middle East, Asia, and Africa, according to Cisco Talos. The threat actor employs a variety of tactics, including the use of SugarGh0st and SpiceRAT malware, alongside decoy documents disguised as official government communications.
Cisco Talos identified the SneakyChef group after observing a series of cyberattacks using the SugarGh0st RAT to target users in Uzbekistan and South Korea. Over time, the group’s activities broadened, prompting the creation of a detailed actor profile. Talos assesses with medium confidence that SneakyChef operators are likely Chinese-speaking, based on their language preferences, usage of Gh0st RAT variants, and specific target selection, which includes various Ministries of Foreign Affairs and other government entities.
The campaign has targeted a wide range of government agencies across EMEA and Asia, including:
- Ministry of Foreign Affairs, Fisheries and Marine Resources, and Agriculture and Forestry of Angola
- Ministry of Foreign Affairs of Turkmenistan, Kazakhstan, and India
- Embassy of the Kingdom of Saudi Arabia in Abu Dhabi
- Ministry of Foreign Affairs of Latvia
The decoy documents used in these attacks are typically scanned documents of government agencies not readily available on the internet. These documents often contain lures related to government and research conference themes.
SneakyChef has employed various decoy documents to target specific regions:
- Southern Africa: Documents impersonating the Ministry of Foreign Affairs of Angola, including circulars about debt conciliation meetings and legal decrees.
- Central Asia: Documents related to meetings and government priorities, targeting Turkmenistan and Kazakhstan.
- Middle East: Official circulars regarding public holidays, targeting Saudi Arabia.
- Southern Asia: Indian government documents, including passport applications and Indo-U.S. relations.
- Europe: Documents related to ambassador announcements, targeting Latvia.
Additionally, the group used decoys from conference invitations and abstracts to lure victims in other regions.
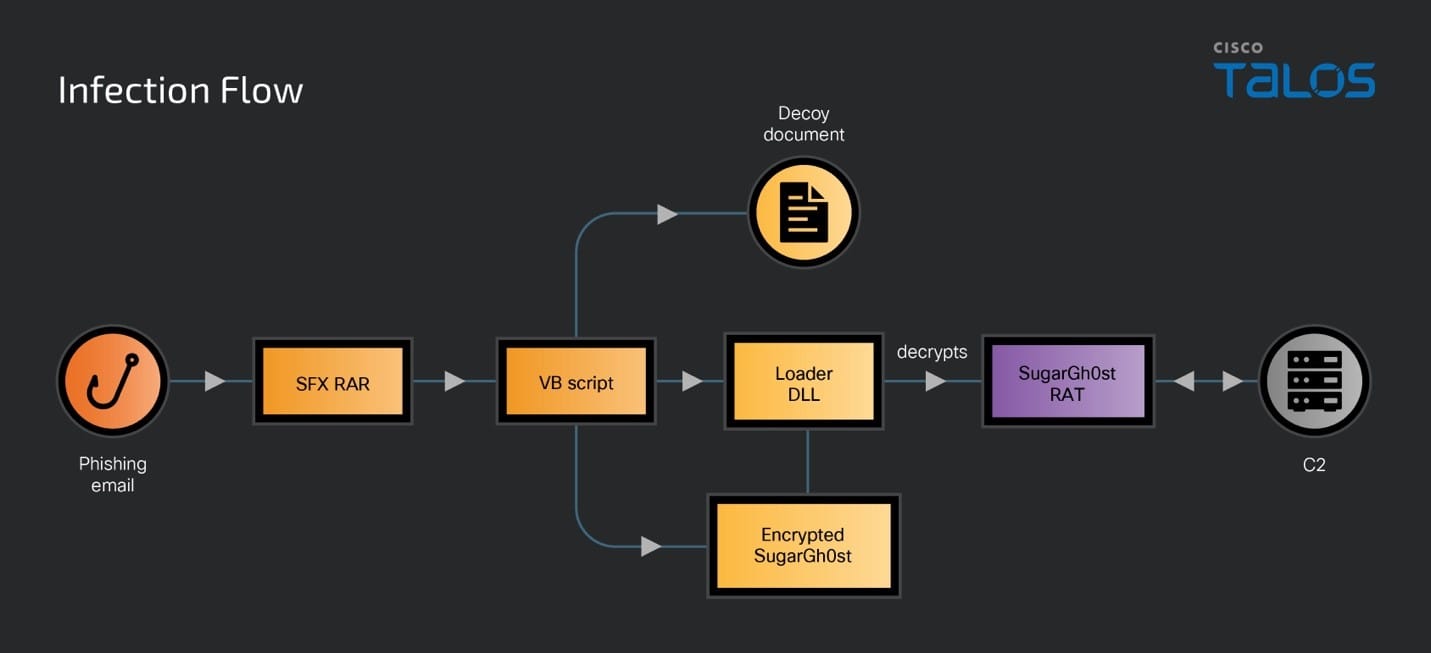
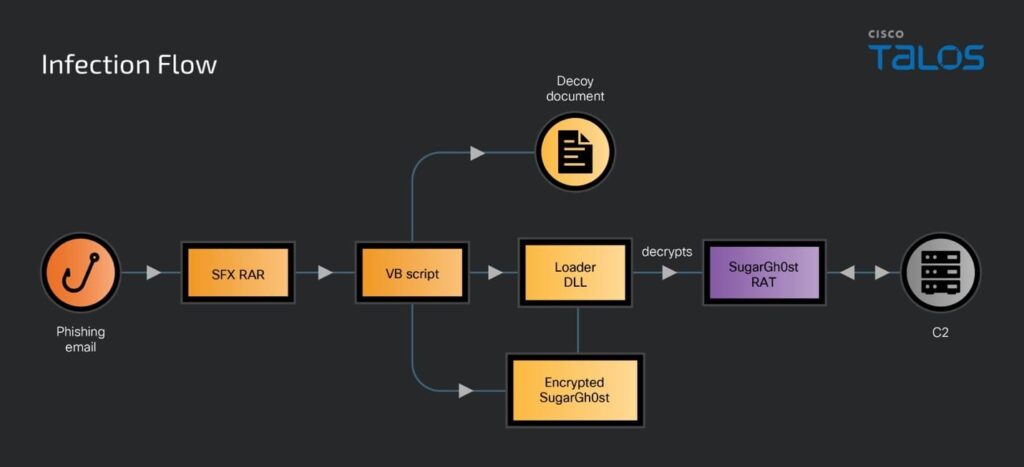
The SneakyChef campaign has evolved its infection techniques over time. Initially, the group used malicious RAR files with LNK files delivered via phishing emails. In the latest campaign, SneakyChef has adopted a new method using SFX RAR files. When executed, these files drop a decoy document, DLL loader, encrypted SugarGh0st, and a malicious VB script into the victim’s temporary folder. The VB script establishes persistence by modifying the registry key UserInitMprLogonScript, ensuring the malware executes when the user logs in.
This technique is consistent with previous attacks reported by the Kazakhstan government and other authorities.
Despite Talos’ initial disclosure in November 2023, SneakyChef continues to use known C2 domains and has also deployed new ones. The primary C2 domain, account[.]drive-google-com[.]tk, remains active, with new queries observed until mid-May. A new domain, account[.]gommask[.]online, has also been reported, with activities traced back to March 2024.
Organizations are advised to update their security protocols, conduct regular threat assessments, and remain aware of the latest threat actor profiles and techniques. For detailed analysis and further information, read the full Cisco Talos report on SneakyChef and the SugarGh0st campaign.