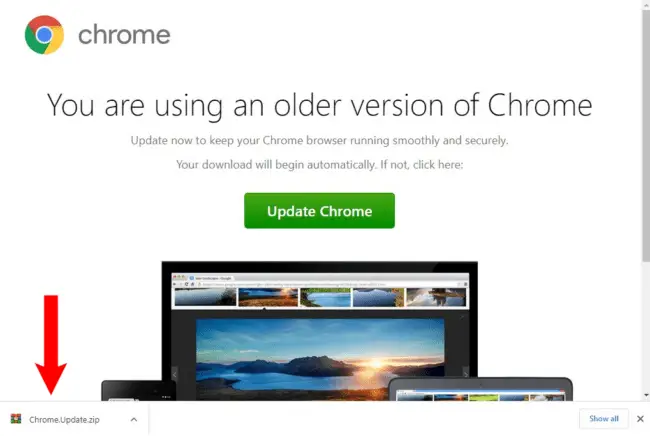
Example of a SocGholish fake Chrome browser update used to serve malicious downloads
SocGholish, a sophisticated JavaScript malware framework, has been a persistent threat since its emergence in 2017. Designed to deceive users into downloading and executing malicious files under the guise of critical browser updates, SocGholish has evolved into a formidable tool for cybercriminals. Recently, RIANNA MACLEOD, Sucuri’s Marketing Manager, highlighted the significant risks associated with this malware in a comprehensive report.

SocGholish’s primary objective is to trick users into downloading malware by displaying fake browser update notifications. Once executed, these files deploy a variety of malicious payloads, including Remote Access Trojans (RATs) and infostealers, leading to severe security breaches and financial losses.
The implications of SocGholish extend far beyond individual infections. It has been linked to several high-profile cyberattacks, including:
- SolarWinds Attack: PRODAFT has connected SocGholish to this significant supply chain breach, which affected numerous organizations, including government agencies and Fortune 500 companies.
- EvilCorp Ransomware: Microsoft has identified SocGholish as a loader for other malware types used by the notorious ransomware group EvilCorp.
These connections underscore the critical role SocGholish plays in broader, coordinated cybercrime activities.
SocGholish employs several deceptive tactics to achieve its malicious goals:
- Fake Browser Updates: The malware displays convincing fake browser update prompts on compromised websites. These prompts mimic legitimate update notifications from popular browsers like Chrome, Firefox, and Edge, urging users to download and execute a file manually.
- Malicious Downloads: The downloaded files, often in .zip or .js format, appear harmless but are laden with malware. Execution of these files allows SocGholish to collect environment information and communicate with a Command & Control (C2) server to deploy secondary malware.
- Deployment of Secondary Malware: Once executed, SocGholish can deploy various types of secondary malware, including RATs, information stealers, and Cobalt Strike beacons. These can lead to further exploitation and lateral movement within a network, setting the stage for more severe attacks like ransomware.
SocGholish uses advanced techniques to distribute its malicious payloads:
- Domain Shadowing: By compromising legitimate domains and adding subdomains pointing to malicious servers, SocGholish evades detection and ensures persistent distribution of malware.
- WordPress Plugins: Attackers bundle malware into legitimate-looking plugins, using compromised WordPress admin credentials to upload and activate these plugins on victim sites. Once activated, these plugins serve SocGholish payloads, further compromising the website and its visitors.
SocGholish operators run affiliate programs encouraging third-party hacker groups to load SocGholish scripts onto infected sites. Some prevalent examples include:
- NDSW/NDSX Injections: This variant injects obfuscated JavaScript into compromised websites, making it difficult to detect and remove.
- Khutmhpx Injections: Named after a variable used in its injections, this variant is often found in multiple instances on infected web pages, further complicating detection and remediation.
SocGholish continues to pose a significant threat to individuals and organizations alike. By understanding its operation and implementing robust security measures, we can mitigate its impact and protect our digital environments.