Solana Web3.js Library Compromised in Targeted Supply Chain Attack
A sophisticated supply chain attack has been identified within the widely-used @solana/web3.js JavaScript library, potentially jeopardizing the security of numerous developers and users within the Solana ecosystem. Malicious code was injected into versions 1.95.6 and 1.95.7 of the library, which is downloaded over 350,000 times weekly from the npm registry. This code was designed to exfiltrate private keys, leaving users vulnerable to cryptocurrency theft.
Technical Analysis:
anyone using @solana/web3.js, versions 1.95.6 and 1.95.7 are compromised with a secret stealer leaking private keys. if you or your product are using these versions, upgrade to 1.95.8 (1.95.5 is unaffected)
if you run a service that can blacklist addresses, do your thing with…
— trent.sol (@trentdotsol) December 3, 2024
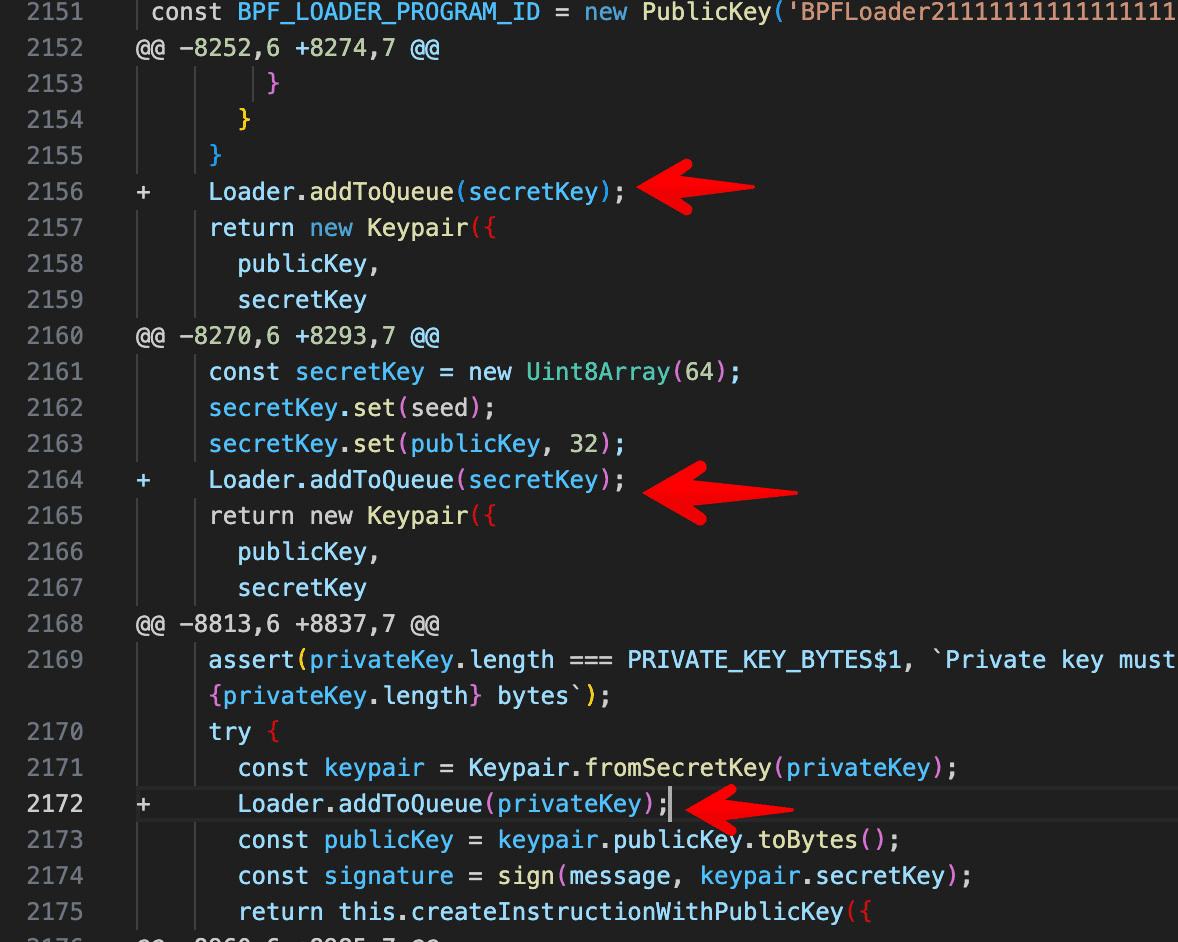
Forensic analysis reveals that the compromised versions of the library contained obfuscated code designed to capture and transmit private keys to a hardcoded Solana address: FnvLGtucz4E1ppJHRTev6Qv4X7g8Pw6WPStHCcbAKbfx. This malicious activity was further concealed through the use of seemingly benign CloudFlare headers, adding a layer of stealth to the operation.
Datadog cloud security researcher Christophe Tafani-Dereeper highlighted the sophistication of the backdoor. In a post on Bluesky, he explained:
“The addToQueue function strategically exfiltrates private keys under the guise of legitimate Cloudflare headers. Its injection into genuine code paths underscores the challenges of detecting malicious code in trusted libraries.”
Tafani-Dereeper also revealed that the associated domain sol-rpc[.]xyz was used to collect stolen keys. Although currently offline, its short operational window indicates the need for immediate action from affected developers and users.
Attribution and Attack Vector:
While investigations are ongoing, preliminary findings suggest that the attack likely stemmed from a social engineering or phishing campaign targeting the maintainers of the official Web3.js open-source library. This incident underscores the increasing sophistication of threat actors and their ability to exploit human vulnerabilities to compromise software supply chains.
Impact and Mitigation Strategies:
Developers who integrated the affected versions into their projects, and users interacting with applications reliant on the compromised library, face a significant risk of private key exposure and subsequent financial loss.
Recommended Actions:
-
Developers:
- Conduct immediate audits of all projects to identify any utilization of
@solana/web3.jsversions 1.95.6 or 1.95.7. - Implement a rollback to a version prior to 1.95.6 or upgrade to the remediated version 1.95.8.
- Perform a comprehensive manual inspection of the
node_modulesdirectory and dependency trees to identify any anomalies or suspicious modifications. - As a precautionary measure, regenerate potentially compromised keys and revoke associated permissions.
- Conduct immediate audits of all projects to identify any utilization of
-
Users:
- Exercise heightened caution when interacting with Solana-based applications and decentralized finance (DeFi) protocols.
- Consider proactively transferring assets to a newly generated wallet if there is any suspicion of key compromise.
Response and Remediation Efforts:
npm, the package registry for JavaScript, has promptly removed the malicious versions of the library to mitigate further impact. However, this incident serves as a critical reminder of the ever-present risks within the software supply chain and the need for continuous vigilance and robust security practices.
Related Posts:
- Solana Drainer Source Code Leak Reveals MS Drainer Connection, Underscores Growing Threat to Crypto Users
- Malicious Browser Extension Hijacks Solana Transactions
- PrimeXBT Adds Cardano, Chainlink, Solana, And Other Altcoins To Growing Lineup
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected




