Infection chain
Recently, eSentire’s Threat Response Unit (TRU) has uncovered a new campaign by the SolarMarker threat group, which involves the impersonation of the global employment website Indeed. This latest attack utilizes a team-building-themed lure to trick users into downloading malicious software.
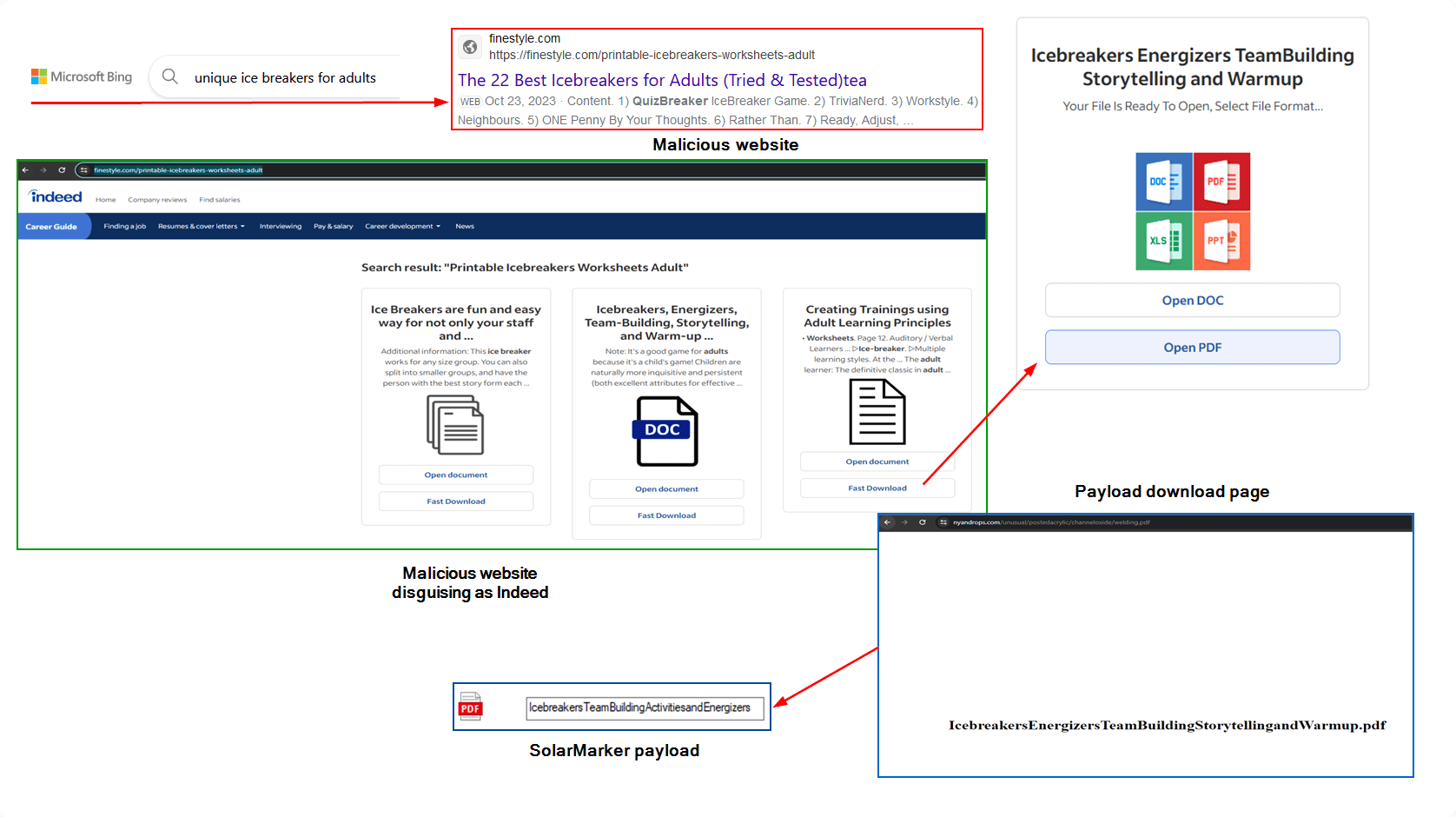
The infection began when a user, searching for workplace team-building ideas on Bing, was redirected to a malicious site mimicking Indeed. This deceptive site persuaded the user to download what appeared to be a legitimate document, which in reality initiated the download of the SolarMarker payload. The attack then escalated as additional malicious components, including StellarInjector and SolarPhantom, were deployed.
SolarMarker’s initial payload was cleverly hidden within the resource section of the file and encrypted with the AES encryption algorithm. Upon execution, a fake error message was displayed, masking the malware’s true activities. The backdoor connection was then established with the threat actor’s server, allowing for the delivery of the StellarInjector payload. This payload was responsible for injecting SolarPhantom into the SearchIndexer.exe process.
SolarPhantom, a powerful component of this campaign, includes info-stealing and hidden virtual network computing (hVNC) capabilities. It stages browsing data within a folder in the %TEMP% directory, named with a 10-digit value such as “3619417678.” The filename generation process involves a complex XOR operation with the user’s browser profile path and other data.
To lend legitimacy to their malware, SolarMarker used two different digital certificates for the initial payload:
- Ameri Mode Inc. (Issuer: DigiCert)
- SMART AC VIET NAM TM & DV JOINT STOCK COMPANY (Issuer: GlobalSign)
These certificates help the malware bypass security checks and appear trustworthy to unsuspecting users.
This incident underscores the need for heightened vigilance when interacting with online content, even from seemingly trusted sources. Organizations and individuals are urged to implement robust security measures, including regular software updates and employee awareness training, to mitigate the risk of falling victim to such attacks.
For a detailed technical analysis and indicators of compromise, please refer to eSentire’s official report.