The overall structure | Image: 360 Security Center
In a recent report, 360 Security Center revealed a new threat to Brazilian banking customers with the emergence of SolarSys, a Trojan framework designed to steal sensitive data while evading detection. The framework is active primarily in Brazil, a known hotspot for banking Trojans, and uses sophisticated evasion techniques and varied attack modules to compromise user security on multiple fronts.
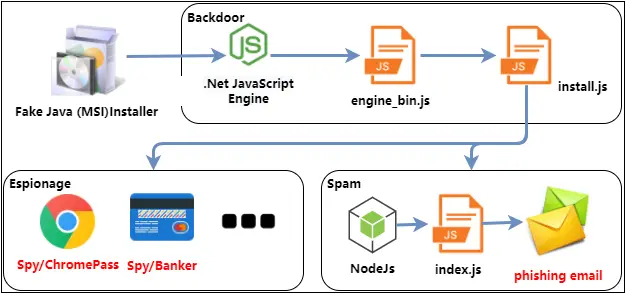
SolarSys operates through a multi-component structure that includes JavaScript backdoors, mail worms, and various spying modules. As 360 Security explains, “the SolarSys framework is mainly composed of JavaScript backdoors, mail worms and multiple spy modules,” with each component performing specialized tasks that allow the Trojan to bypass security barriers and capture valuable user data.
To maintain a resilient presence, SolarSys uses a Domain Generation Algorithm (DGA) to produce numerous dynamic domain names, which serve as its command-and-control (C&C) addresses. This mechanism enables attackers to switch domains rapidly when security vendors attempt to block access. “When security vendors block some of the domain names, hackers will quickly activate new domain names to ensure that the overall botnet will not be affected,” the report notes.
SolarSys initiates infection through fake MSI installers, which masquerade as legitimate applications such as Java and Microsoft HTML Help. Once executed, these files utilize InstallUtil to launch a malicious .NET dynamic library, uninstall.dll, which registers itself as a persistent backdoor on the infected system. From there, the malware can download and execute additional virus modules every 11 hours, enabling continuous access and updates to SolarSys’s capabilities.
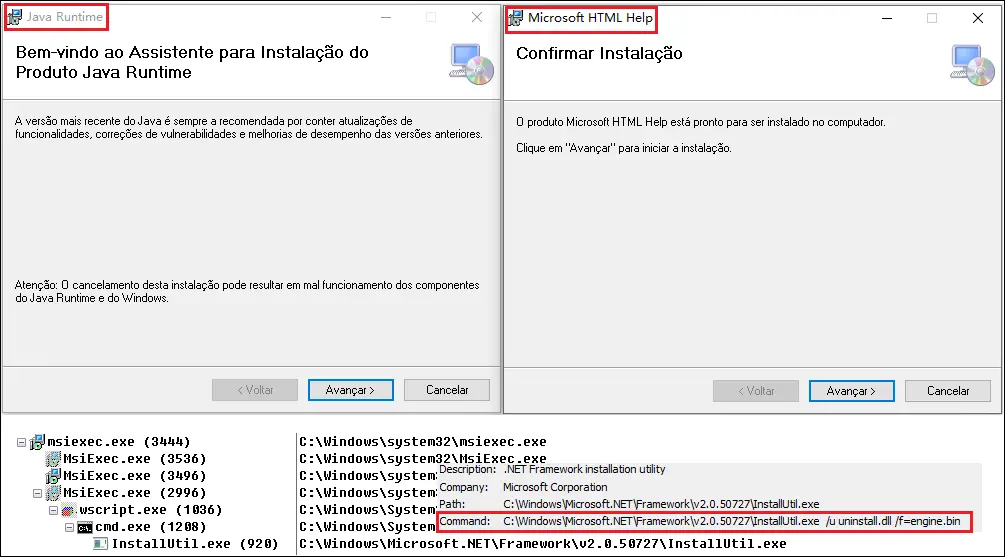
The backdoor’s persistence mechanism involves a JavaScript file, Install.js, which “downloads and executes the latest virus module execution every 11 hours,” ensuring SolarSys remains active on infected devices without raising user suspicion.
A unique feature of SolarSys is its mail worm module, which exploits the user’s contact list to propagate itself. By establishing a Node.js environment on infected machines, SolarSys simulates user clicks to send phishing emails directly to the victim’s contacts. The phishing emails contain an attachment designed to deliver further malware, employing template injection techniques to evade detection. Although researchers were unable to retrieve the specific template, they suspect SolarSys will continue updating its payloads through this channel.
SolarSys deploys multiple spying components to capture sensitive information, including a module aimed at extracting data from Google Chrome. This module captures account credentials, browsing history, and other user details. In addition, SolarSys includes a banking Trojan, which detects when users visit online banking websites and overlays a fake login interface. As the report explains, “the fake online banking login interface…trick[s] the user into entering various credentials,” which are then transmitted to the attackers’ servers.
The malware specifically targets numerous Brazilian banks, including Banco do Brasil, Bradesco, Itaú, Santander, and Sicoob, among others, making it a direct threat to the country’s financial sector.
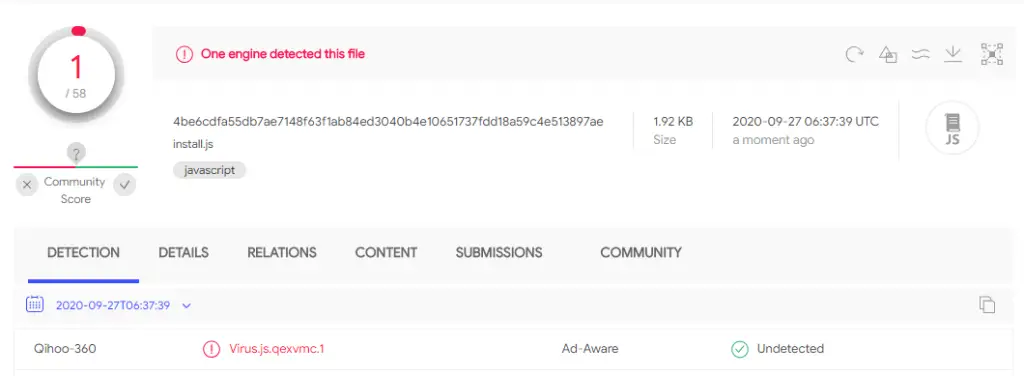
As of the report’s publication, SolarSys has proved challenging to detect, with 360 Security Center being the only vendor capable of identifying it on VirusTotal.
Related Posts:
- Attacker use DDoS attack to hit three major Dutch banks
- Pitfalls of developing mobile banking application
- Kaspersky Highlights Key Trends in Financial Cybersecurity for 2024
- Brazilian Banking Malware Targets Spain: An Emerging Cyber Threat Landscape