Open directory and snippet of file contents on the server | Image: Hunt
In a recent report, Hunt researchers uncovered a sophisticated phishing campaign suspected to be linked to North Korean threat actors, primarily targeting users of Naver, South Korea’s largest tech platform. The investigation also revealed an additional infrastructure cluster dedicated to spoofing Apple domains.
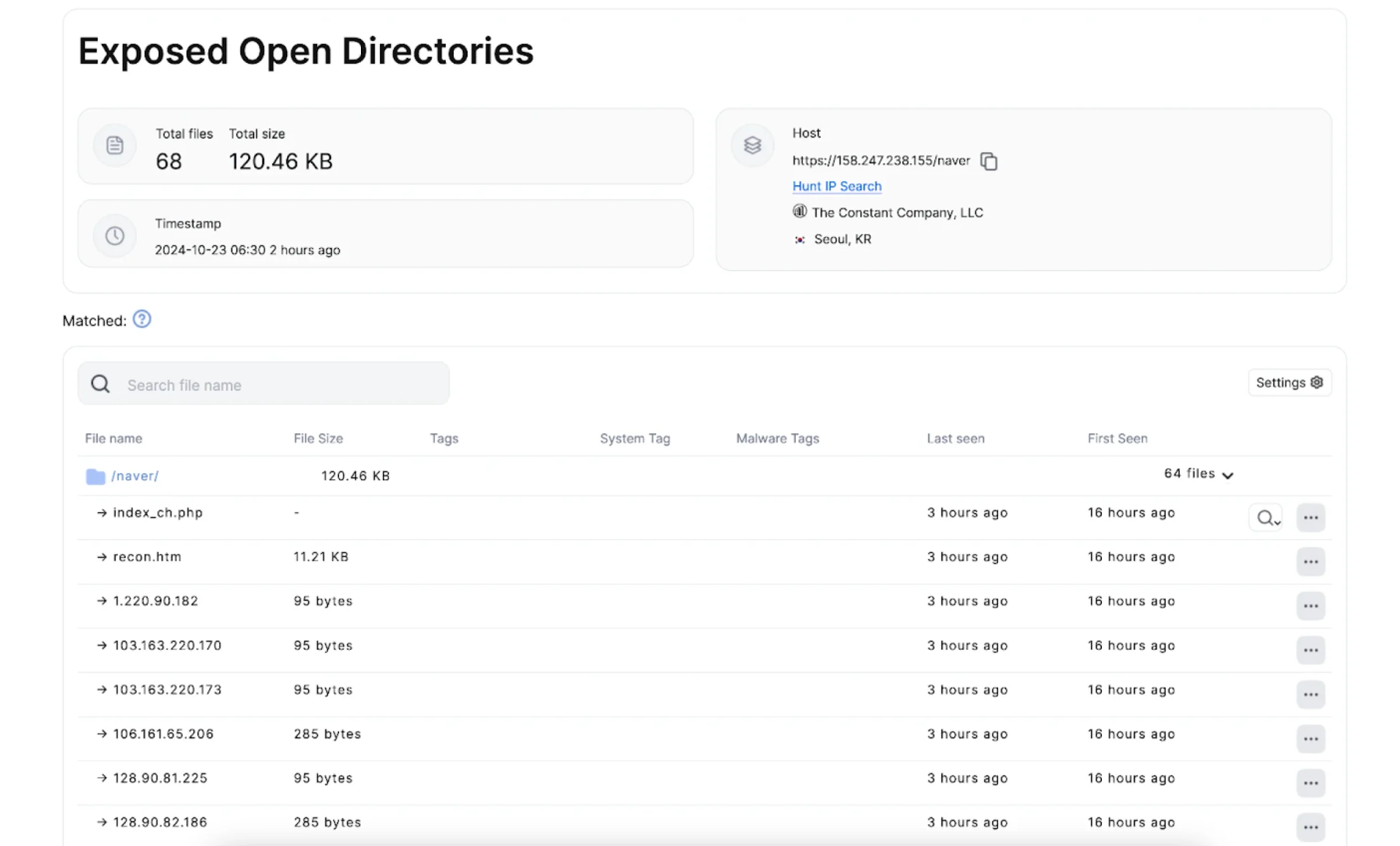
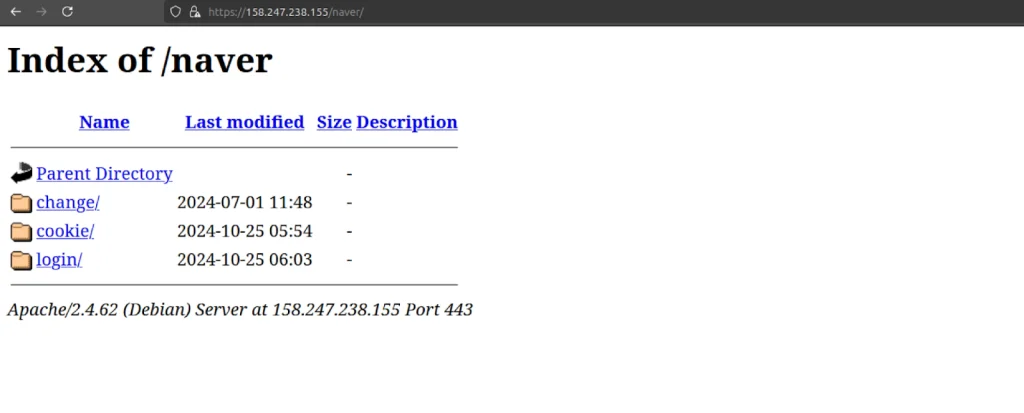
The investigation began with the discovery of a suspicious directory at https://158.247.238[.]155/naver, located on a server hosted by The Constant Company in Seoul. Researchers found the directory contained files with distinct names like “login,” “cookie,” and “change”—common indicators of credential-stealing campaigns. This setup aligns with methods frequently used by North Korean groups such as Lazarus and Kimsuky. “Each folder aligns with typical patterns seen in credential-stealing campaigns,” the report notes, a technique these actors often use to capture login credentials.
The files on the server included recon.htm, a page designed to mimic Naver’s “My Info” password change page, intended to prompt users to enter their credentials. Hunt’s analysis found that “above the username and password fields is a message (in Korean) that translates to: Deleting Cookies – You’ll need to verify your identity to block suspicious devices.” This prompt is likely meant to create a sense of urgency, pushing users to enter sensitive information.
Further examination of the server revealed it hosted more than 200 domains, many of which redirect to legitimate Naver pages to add an appearance of authenticity. According to Hunt’s telemetry, “the server administrators frequently updated or replaced TLS certificates issued by Let’s Encrypt,” a common tactic among threat actors seeking to lend legitimacy to their malicious infrastructure while keeping costs low.
During their probe, Hunt researchers also uncovered a separate cluster of domains and certificates spoofing Apple, hosted primarily on IP addresses within Iran. The certificates, including domains like ulta.appleplus[.]store and appleplus[.]shop, appear to be part of an effort to lure users into thinking they are interacting with legitimate Apple services. The report suggests, “This behavior highlights the importance of monitoring these shifting patterns closely to detect potential threats early and adapt defenses accordingly.”
Related Posts:
- North Korean Cyberattacks Persist: Developers Targeted via npm
- Expert: North Korean hackers harvest 11,000 Bitcoins in 2017