Hackers can use sound waves to interfere with the normal operation of the hard disk drive (HDD), resulting in a temporary or permanent denial of status (DoS). Can be used to block closed-circuit television (CCTV) recording video clips, or to stop the computer that is handling critical operations.
The basic principle of this attack is to introduce the vibration frequency of the sound waves into the data storage disk of the hard disk. If the frequencies are the same, the resonance effect will be produced, which may cause the HDD to work abnormally, stop working and even physically damage the data.
Using sound waves to break a hard drive was not a fresh idea. As early as 2008, Brandon Gregg, chief technology officer of Joyent, a cloud computing company in the United States, showed how the public could use the sound to cause hard disk read/write errors.
Earlier this year, an Argentine researcher demonstrated how he temporarily halted the operating system’s command response by playing 130Hz audio.
The new achievements highlight the practicality of the HDD acoustic attacks
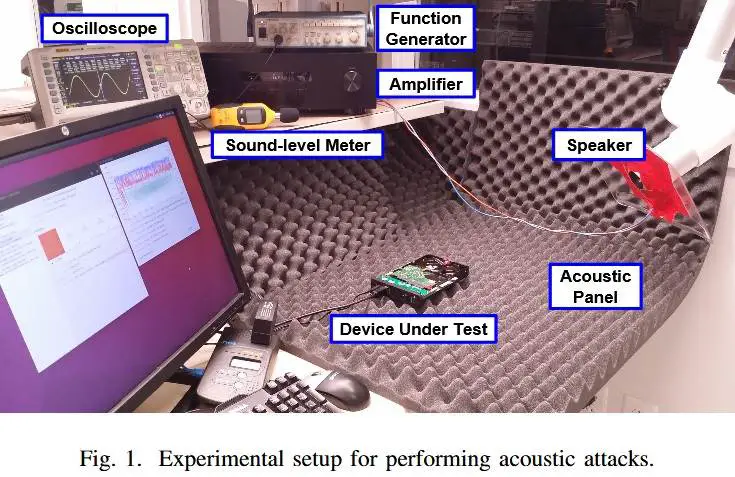
Last week, scientists at Princeton University and Purdue University in the United States published new research that expanded the results of previous studies and included more practical test results.
The team used specially crafted test equipment to blast the drive from different angles and record the results to determine the sonic frequency, attack time, distance from the drive, and the angle at which the drive was stopped.
The test subjects included four models of Western Digital hard disk drives and the test results confirmed that the team’s attack was a complete success.
The team said attackers can transmit acoustic waves of specific frequencies by using external speakers or by using loudspeakers near the target.
An attacker can use a variety of means to achieve its goals, for example, 1. Invade the target device with a remote attacker to launch some audio playing software (such as remotely controlling multimedia software in a vehicle or personal device); 2. Induce victim to play attached to Email or web pages; and 3, embed similar malicious audio files in widely distributed multimedia such as television commercials.
A variety of devices were attack tested
The team conducted sonic attacks on a variety of devices during the test, including digital video recorders (DVRs) and desktop computers running Windows 10, Ubuntu 16, and Fedora 27.
In tests against the DVR, a pop-up warning window appears on the monitor screen stating “Lost!” Only after about 230 seconds of sound emission.
The team played the recorded video and found that the video was silent, which meant that the recording function of the DVR was blocked. After the DVR reboots, all functions are back to normal, but this means that real-time monitoring is interrupted during this period.
The second test targeted desktop computers running various operating systems, and researchers played 9.1 kHz of audio 25 cm from the airflow openings in the chassis.
This led to these computers appeared a variety of applause and even blue screen of death. After playing for a long period of time, it can cause the underlying operating system of the computer to crash.
Protection against sonic attacks is needed
While most of these attacks rely on playing specially crafted audio files from close range, the team does not see this as a problem. They said: “The use of more powerful sound sources can increase the range of attacks accordingly.”
The team said hard disks play an important role in computer systems. It is loaded with the most important software components (such as the operating system) and a variety of sensitive data (such as monitoring images), it will be to attract a large number of attackers.
It is worth emphasizing that the successful implementation of sonic attacks does require a great deal of specialized equipment as well as meeting a variety of criteria. But for some large hacker organizations, such as state-backed hacking organizations, it is very practical for the invasion or forensics of some key systems.
Source: bleepingcomputer