Image Credit: 3xp0rt
Recently, a cybersecurity researcher known by the alias “3xp0rt” discovered that the full source code of the inaugural version of the HelloKitty ransomware has been unveiled on cybercrime forums. The individual responsible for this disclosure professed the development of a novel and considerably more potent encryption tool. The creator, identified pseudonymously as “kapuchin0” online, also garners the epithet “Gookee.”

Previously associated with deceptive undertakings, Gookee had, in 2020, proffered access to Sony Network Japan, attempting to vend malicious software source codes and even tendered his own RaaS (Ransomware as a Service) christened “Gooke Ransomware.”
Evidently, kapuchin0/Gookee, the principal developer of the HelloKitty encryptor, is currently orchestrating a new offering which, by his assertion, promises to be considerably more intriguing than the once-viral Lockbit.
The disseminated file, hellokitty.zip, encompasses a ready-made Microsoft Visual Studio solution tailored for the creation of the HelloKitty encryptor and decryptor, along with the NTRUEncrypt library employed by this malware variant for encrypting files.
The contents of this archive have been corroborated by ransomware connoisseur Michael Gillespie as the veritable HelloKitty source code employed in the 2020 campaign.
While the public dissemination of ransomware source code might ostensibly benefit security research, its ramifications are predominantly detrimental. Typically, cyber felons swiftly adapt open-source code to their objectives, spawning numerous derivatives from a singular malicious software, thereby commencing their own nefarious operations.
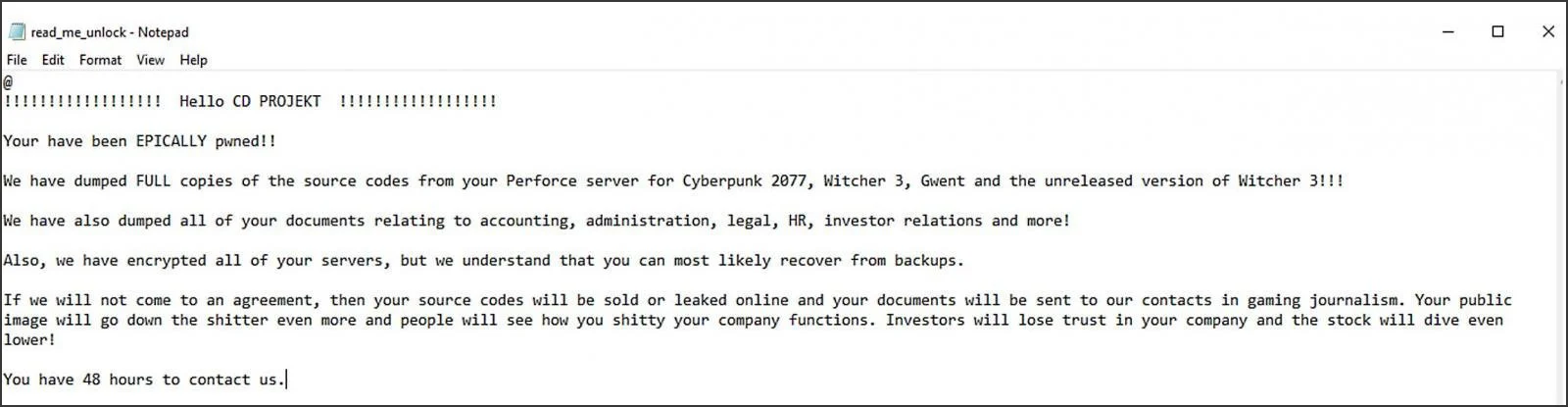
Since November 2020, the HelloKitty campaign has been active, gaining notoriety for its assaults on corporate networks, data pilfering, and system encryption. The most illustrious attack leveraging this ransomware transpired in February 2021 against the Polish firm CD Projekt Red, where the assailants openly proclaimed their expropriation of various studio game source codes.
On a related note, the HelloKitty ransomware and its derivatives have occasionally been operational under alternative nomenclatures, including DeathRansom, Fivehands, and possibly Abyss Locker.
In late October 2021, the Federal Bureau of Investigation (FBI) even disseminated a comprehensive list of compromise indicators, intended to aid cybersecurity professionals in detecting HelloKitty. However, with the inexorable march of time, such data may now be obsolete.