The United States Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning to federal agencies about the necessity of bolstering the security of Juniper devices within their networks. This advisory was prompted by the discovery of four critical vulnerabilities that are currently being exploited in remote code execution (RCE) attacks.
Tracked as CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, and CVE-2023-36847, these vulnerabilities were identified in the Juniper J-Web interface. Juniper Networks informed its clients of these flaws a week after the threat monitoring service ShadowServer recorded attempts to exploit them. Furthermore, the watchTowr Labs team has presented a proof-of-concept (PoC) exploit.
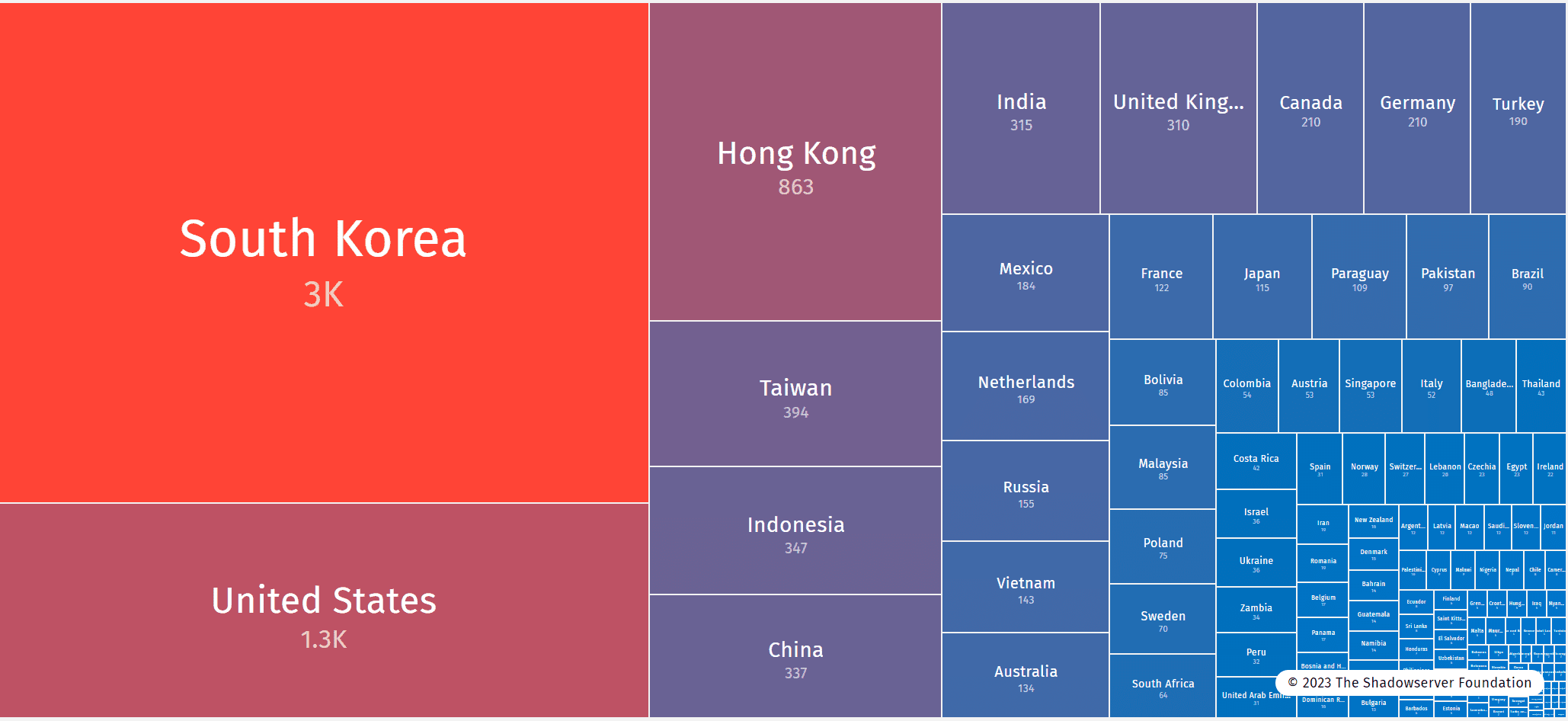
According to Shadowserver, more than 10,000 vulnerable Juniper devices, including the J-Web interface, are accessible online. A significant portion of these devices are located in South Korea (approximately 3,000) and the United States (around 1,300). This highlights the severity of the threat, as these devices play a crucial role in network infrastructure.

CISA has urged administrators to take immediate action by updating the JunOS operating system to the latest version or, at a minimum, restricting internet access to the J-Web interface. This measure aims to minimize the risks of attacks.
Additionally, CISA has included these Juniper vulnerabilities in its catalog of Known Exploited Vulnerabilities (KEV), marking them as significant risks to the federal enterprise and commonly used vectors for malicious attacks.
Federal civilian executive branch agencies are now mandated to secure Juniper devices in their networks by November 17. CISA also strongly recommends all organizations, including private companies, prioritize addressing these vulnerabilities with the utmost urgency.