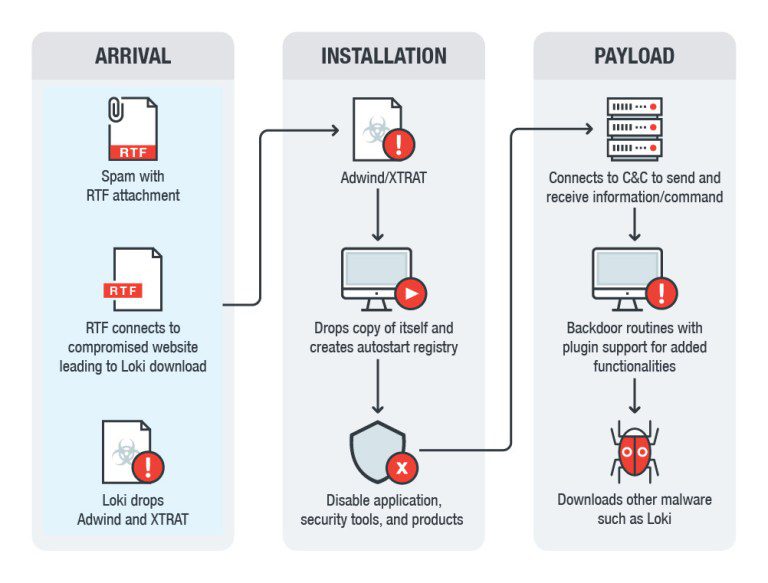
Recently, Trend Micro security experts posted a blog post saying they had discovered a spam campaign. Through this spam, hacking organizations can distribute XTRAT and DUNIHI backdoors and Loki malware bundled with the Adwind RAT. At present, experts detected a total of 5,535 cases of Adwind infection between January 1 and April 17, including the United States, Japan, and Australia.
This spam campaign was mainly used to distribute two campaigns, one of which is the XTRAT backdoor (aka “XtremeRAT”, BKDR_XTRAT.SMM) and the information theater Trojan Loki (TSPY_HPLOKI.SM1) to provide cross-platform remote access to Trojans. Adwind (detected by Trend Micro as JAVA_ADWIND.WIL). In another separate Adwind RAT spam campaign, researchers observed the use of VBScript with a backdoor that was tracked as DUNIHI.
Researchers said that both campaigns abuse legitimate free dynamic DNS servers hopto [.]org, and tried to increase the success rate of system infection through different backdoor programs. In other words, when one of the malwares is detected, other malicious software will continue to complete the infection.
The crook behind Adwind, XTRAT, and Loki use a weaponized RTF document to trigger the CVE-2017-11882 vulnerability to deliver the Adwind, XTRAT, and Loki packages.
Since 2013, Adwind has been able to run on all major operating systems (Windows, Linux, MacOSX, Android) and is known for its various backdoor features such as (but not limited to):
- Information theft
- File and Registry Management
- Remote Desktop
- Remote shell
- Process Management
- Upload, download and execute files
XTRAT has similar functions to Adwind, such as information theft, file and registry management, remote desktop and so on. It also has the following features:
- Screenshots desktop
- Recording via webcam or microphone
- upload and download files
- Registry operations (read, write and operate)
- Process operation (execution and termination)
- Service operations (stop, start, create and modify)
- A system that executes a remote shell and controls the victim
DUNIHI has the following backdoor features: execute files, update itself, uninstall itself, download files, upload files, enumerate drivers, enumerate files and folders, enumerate processes, execute shell commands, delete files and folders, terminate processes, Sleep.
To handle cross-platform threats like Adwind, experts recommend adopting multiple layers of security measures. IT administrators should regularly maintain and update networks and systems, and since Adwind’s two variants are sent by e-mail, they must ensure that The security of email gateways mitigates the threat of misuse of email as a system and network entry point.
Suggest Reading
XTRAT and DUNIHI Backdoors Bundled with Adwind in Spam Mails
Source: SecurityAffairs