spectator: Regex based source code scanner
Spectator
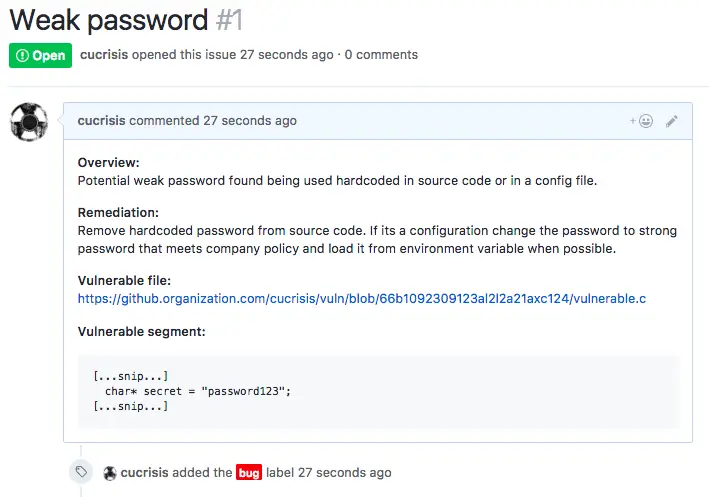
Regex based source code scanner that uses git enterprise search interface to find potential security vulnerability and automatically create issues in an affected repository.
Download
git clone https://github.com/cucrisis/spectator.git
Usage
Targets
Spectator hcs can read targets from a console as a string in the format type;target for instance if you want to scan all public repos of a specific user for instance ‘cucrisis’ then use user:cucrisis. If the target includes all repos in an organization then using something like user:cucrisis,org:private-org will do. Also, it can read a file where each line is type:target 😉 for those picky.
Server
Is the github enterprise server, default to out server look in the URL that’s it
Proxy
Proxy to use for connection for connection.
Output
Spectator hcs module can output everything to console in json format or it can create each finding as an issue directly on an affected repository.

Regex file
The following are supported entries for each regex.
title: the title of the vulnerability.
overview: Description of the vulnerability.
remediation: Remediation of the vulnerability.
locations: Where to search options file, path
languages: The language to search in javascript, python …etc
extensions: The file extension to search in java, ps1, py
patterns: The pattern to search for.
Environment Variables:
SPEC_HCS_TOKEN: Git access token
SPEC_LOG: Output log file, default to config/spectator.log
SPEC_CONFIG: regex file, defaults to config/common.regex.json
Copyright (C) 2017 cucrisis
Source: https://github.com/cucrisis/





