Image: TrustedSec
A new tool called Specula is transforming Microsoft Outlook from a productivity tool into a potent weapon for cybercriminals. Developed by TrustedSec, Specula allows attackers to remotely execute code on your system, turning your email client into a command-and-control (C2) hub for malicious activities.
Specula’s effectiveness lies in its exploitation of a known, yet patched, vulnerability (CVE-2017-11774). This vulnerability allows attackers to bypass Outlook’s security measures and create custom homepages within the application. By modifying specific registry keys, these malicious homepages can be used to trigger the execution of VBScript files, granting attackers unauthorized access and control over your system.
Even though Microsoft patched this vulnerability in 2017 and removed the interface for displaying custom Outlook homepages, attackers have found a way to circumvent these protections. By manipulating Windows registry values, they can still create and display these malicious pages, even on the latest versions of Office 365.
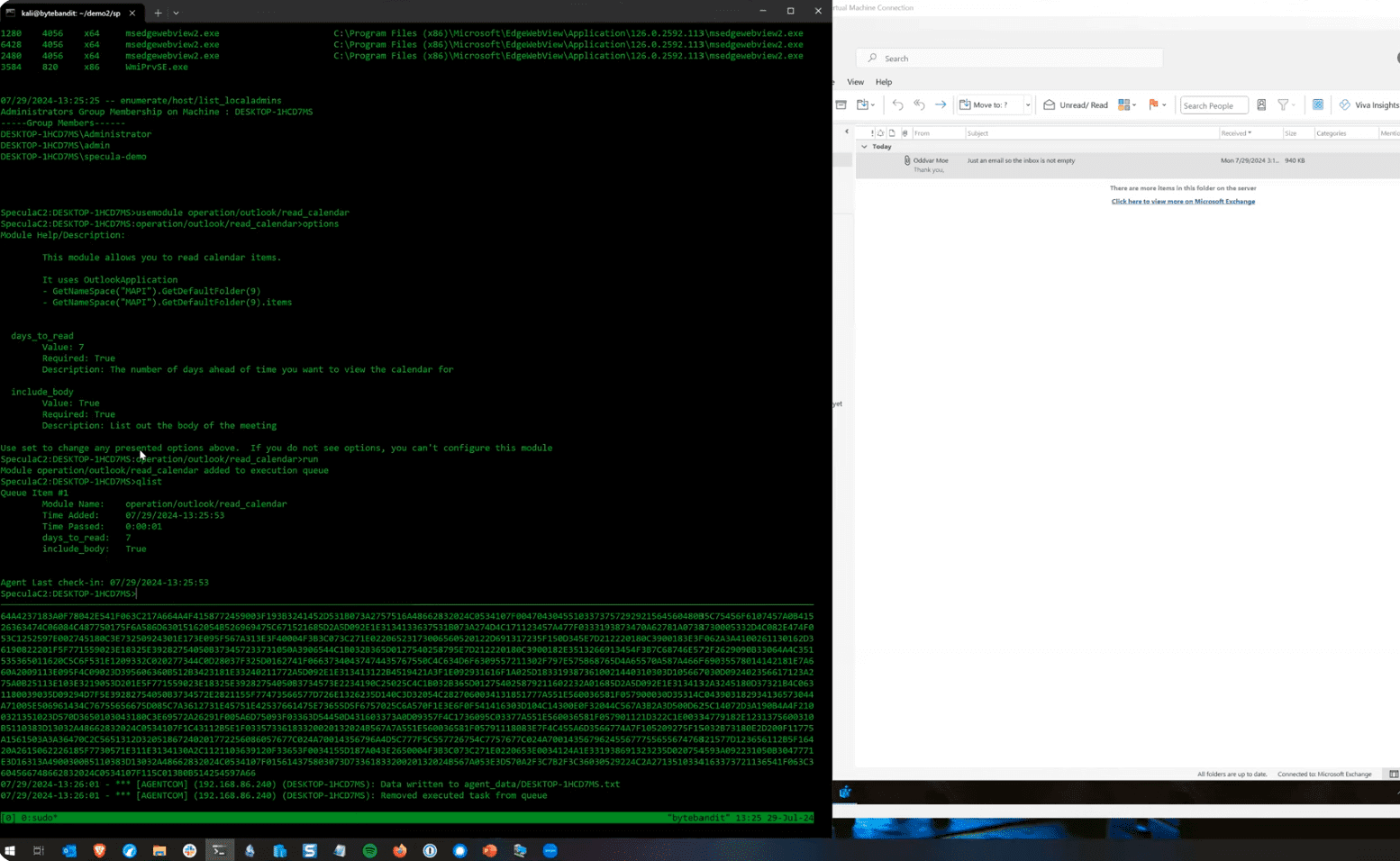
Specula functions within the context of Outlook, setting a custom homepage via registry keys that point to an external site controlled by the attackers. These keys can be found in the registry section “HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\WebView.”
Once a custom homepage is set, Outlook no longer displays your emails or calendar. Instead, it loads a malicious HTML page controlled by the attackers. This page can then execute VBScript or JScript, giving attackers the same privileges as running scripts directly on your system.
While the initial compromise requires some level of access to your device, once Specula is in place, it provides a persistent backdoor for attackers. They can use it to maintain access, move laterally within your network, and even spread to other systems. The fact that Specula operates within the trusted “outlook.exe” process makes it even more difficult to detect and stop.
Related Posts:
- India announces to use artificial intelligence to develop weapon systems
- Russian nuclear weapons scientists arrested for using supercomputer to mine Bitcoins
- Bad Outlook: Malicious Outlook Reader