SpyNote RAT Evolves: Targets Your Cryptocurrency Wallet
Spynote is a Remote Access Trojan that originated in 2020. Since then, it has developed to be one of the most widespread families of malware for Android, with many samples, integration of other RATs (e.g. CypherRat), and a large family of over 10,000 samples. This malware has shown a particular interest in financial institutions since 2023, highlighting its evolving threat landscape.
Recently, FortiGuard Labs discovered a malicious sample masquerading as a legitimate cryptocurrency wallet. This sample included the SpyNote RAT, featuring new additions aimed at evading analysis and targeting cryptocurrencies specifically. One of the key tactics used by this malware is exploiting the Android Accessibility API, a feature intended to aid users with disabilities by automating UI actions. However, in the case of SpyNote, this capability is maliciously used to record device unlocking gestures and target popular crypto wallets.
The malware operates by recognizing when a legitimate crypto wallet app is in use and then displaying an overlay that appears to be part of the legitimate app. This overlay, a WebView encoded in Base64, presents a fake cryptocurrency transfer page, tricking victims into believing they are conducting transactions through their genuine wallet app. The malicious code further automates the transfer of cryptocurrency to the attackers’ wallet by filling out forms and executing transactions without the user’s consent, all facilitated through the Accessibility API.

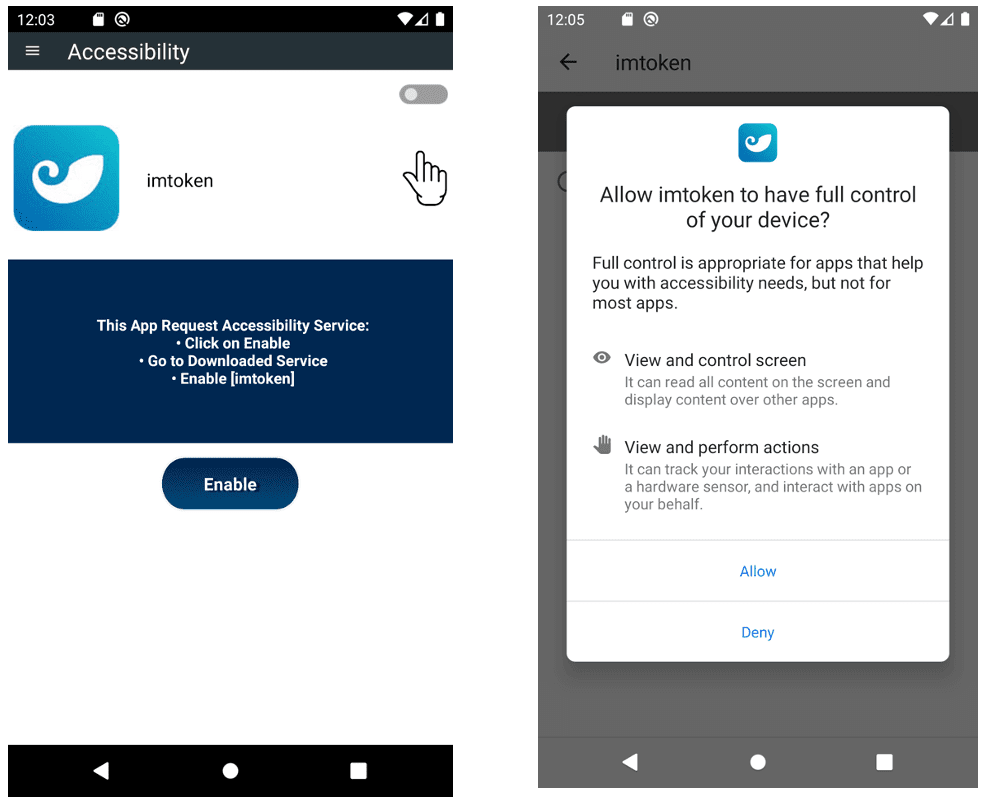
Android Spynote-Permission | Image: FortiGuard Labs
To gain the necessary permissions to exploit the Accessibility API, SpyNote RAT employs various lures to trick users into granting these rights. Users are reminded of the importance of being cautious when granting such permissions, especially to applications that should not typically require them. The Android OS does provide warnings about the risks of granting Accessibility API permissions, but once granted, the malware has virtually unrestricted access to the device’s functions and data.
Moreover, SpyNote incorporates simple yet effective anti-analysis techniques to hinder automated analysis tools, complicating efforts to dissect and understand the malware’s functionality. This includes malformation of the APK structure to cause errors with standard unzip tools, delaying detection and analysis.
This sample of Android/SpyNote demonstrates a shift in focus towards cryptocurrencies, showing malware authors are adapting their strategies to tap into the lucrative world of digital currency. The malware’s ability to initiate unauthorized cryptocurrency transfers underscores the advanced capabilities of modern Android malware, extending beyond simple credential theft.
This case highlights the continuous need for vigilance and the use of reliable security solutions to protect against sophisticated malware threats targeting Android devices.





