Diehard service – restarts itself | Image: F-Secure
Cybersecurity analysts from F-Secure undertook an in-depth examination of the Android spyware, SpyNote, uncovering its vast capabilities for gathering sensitive data.
SpyNote typically proliferates through smishing campaigns, during which malefactors persuade victims to follow an SMS link and install an application. Throughout its installation, SpyNote solicits access to call logs, the camera, SMS messages, and external storage, adeptly concealing its presence on the Android home screen and recent tasks pane to hinder detection.
The researchers asserted that the SpyNote malware can be activated through an external stimulus. Upon receiving a signal, the malicious application initiates its primary function.

What’s notable about SpyNote is that after acquiring permissions, it leverages them to autonomously grant itself extended rights. This includes audio and call recording, keypress logging, and capturing screen images via the MediaProjection API.
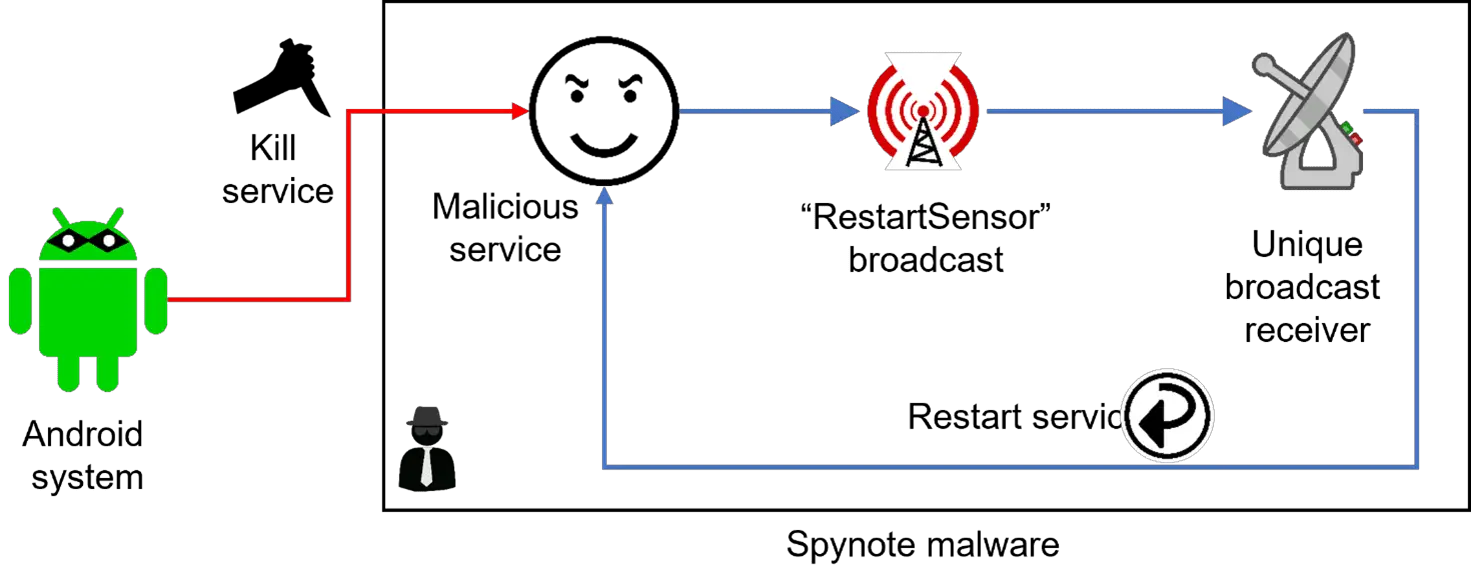
A more meticulous investigation into the malware unveiled the existence of so-called “diehard” services. These are designed to safeguard the application from termination attempts, whether by the victim or the operating system.
The SpyNote spyware ensures its resilience by registering a broadcast receiver, which automatically restarts the malware if termination attempts occur. Moreover, when a user tries to eradicate the malicious application via the settings menu, the menu spontaneously closes due to API utilization. The sole recourse left to address this issue is to perform a factory reset, resulting in the loss of all data on the device.