spyre v1.2.5 releases: simple YARA-based IOC scanner
Spyre
Spyre is a simple host-based IOC scanner built around the YARA pattern matching engine and other scan modules. The main goal of this project is the easy operationalization of YARA rules and other indicators of compromise.
Users need to bring their own rule sets. The awesome-yara repository gives a good overview of free yara rule sets out there.
Spyre is intended to be used as an investigation tool by incident responders. It is not meant to evolve into any kind of endpoint protection service.
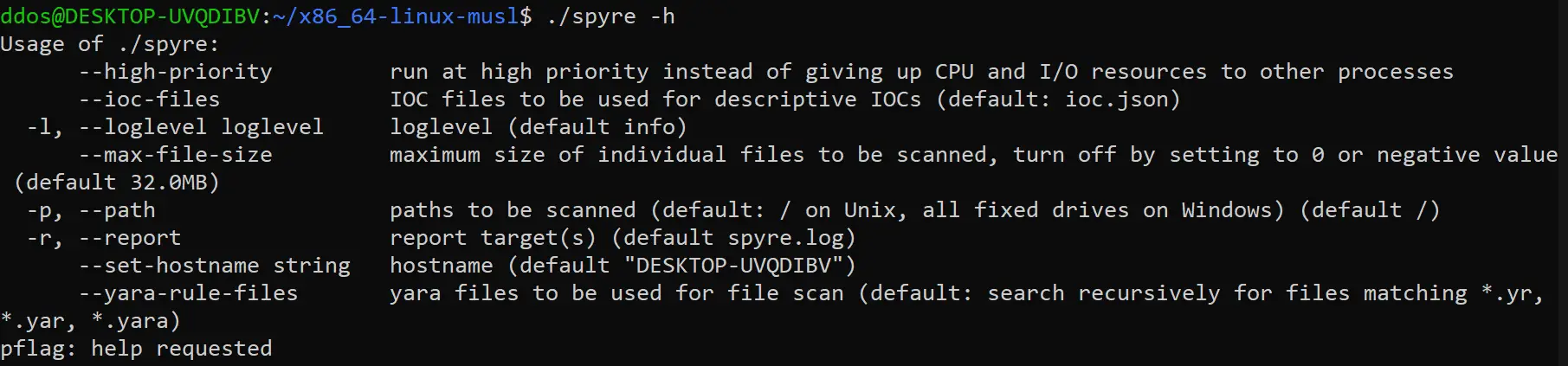
Using Spyre is easy:
- Add YARA signatures. Per default, filenames matching *.yr, *.yar, *.yara are recognized, see below how to change this behavior. The following options exist for providing rules files to Spyre (and will be tried in this order):
- Add the rule files to the ZIP file and append that file to the binary.
- Add the rule files to a ZIP file name $PROGRAM.zip: If the Spyre binary is called spyre or spyre.exe, use spyre.zip.
- Put the rule files into the same directory as the binary.
ZIP file contents may be encrypted using the password infected (AV industry standard) to prevent antivirus software from mistaking parts of the ruleset as malicious content and preventing the scan.
- Deploy, run the scanner
- Collect report
Download & Use
Copyright 2018-2020 DCSO Deutsche Cyber-Sicherheitsorganisation GmbH
Copyright 2021 Spyre Project Authors (see: AUTHORS.txt)