SQLi Query Tampering v1.3 releases
SQLi Query Tampering
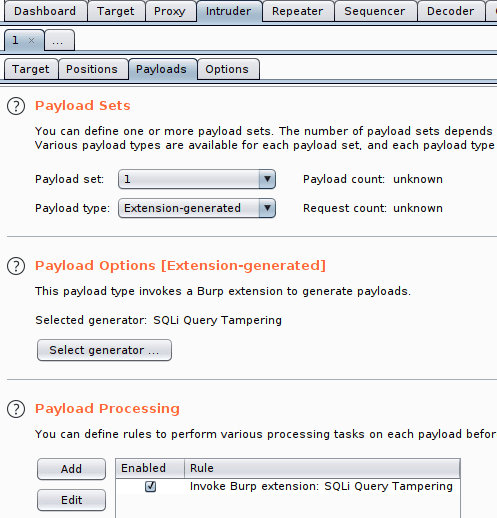
SQLi Query Tampering extends and adds custom Payload Generator/Processor in Burp Suite’s Intruder.
Advantages and Benefits
Sqlmap is a great automated tool for SQL vulnerabilities but it can be a little noisy when you perform pentesting or bug hunting! One of the cool parts of Sqlmap is Tampering. Tampering gives us some functions/techniques to evade filters and WAF’s.
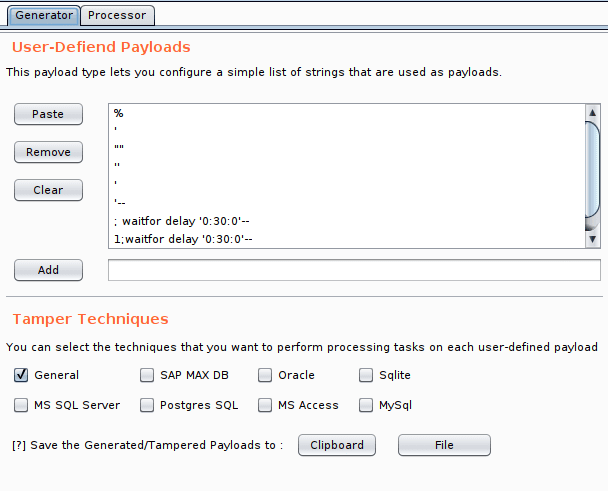
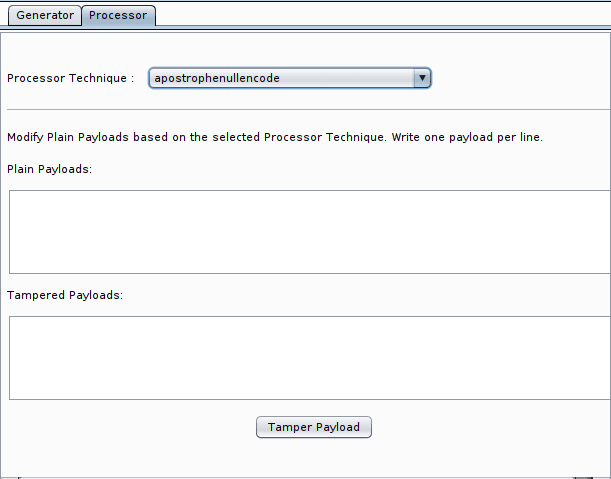
SQLi Query Tampering gives you the flexibility of manual testing with many powerful evasion techniques. This extension has two-part:
- Generator:
- Processor:
The list of Evasion Techniques:
apostrophemask, apostrophenullencode, appendnullbyte, between, bluecoat, chardoubleencode, charencode, charunicodeencode, charunicodeescape, commalesslimit, commalessmid, commentbeforeparentheses, concat2concatws, equaltolike, escapequotes, greatest, halfversionedmorekeywords, hex2char, htmlencode, ifnull2casewhenisnull, ifnull2ifisnull, informationschemacomment, least, lowercase, modsecurityversioned, modsecurityzeroversioned, multiplespaces, overlongutf8, overlongutf8more, percentage, plus2concat, plus2fnconcat, randomcase, randomcomments, sp_password, space2comment, space2dash, space2hash, space2morecomment, space2morehash, space2mssqlblank, space2mssqlhash, space2mysqlblank, space2mysqldash, space2plus, space2randomblank, symboliclogical, unionalltounion, unmagicquotes, uppercase, versionedkeywords, versionedmorekeywords, 0eunion, misunion, schemasplit, binary, dunion
Usage notes:
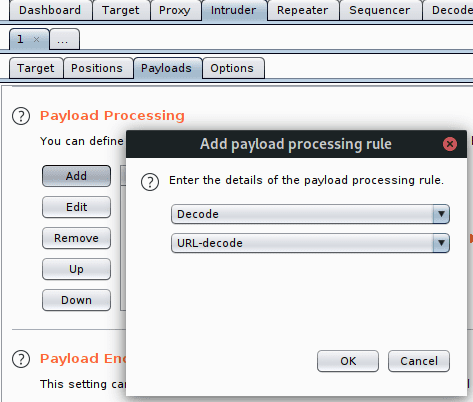
- All Tampered Queries (in Generator/Processor) returned in URL-Encoded
- You can add a decoding rule in Payload Processing section if you need URL-decoded payloads
Changelog v1.3
- Add Options tab:
- Payloads Directory
- Restore Defaults
- Fix some issues in UI and Tamper module
Download & Install
Copyright 2014 Context Information Security