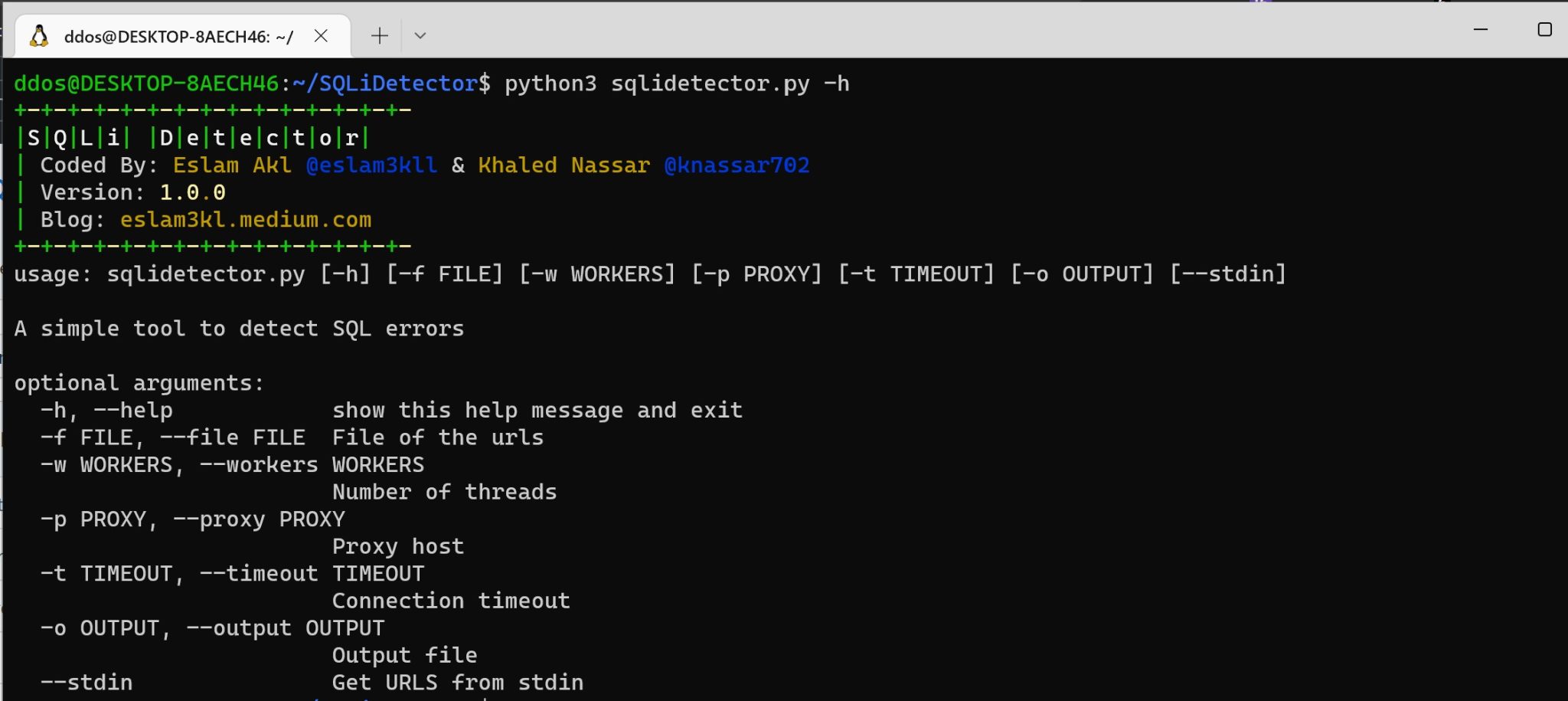
SQLiDetector: detect SQL injection Error based
SQLiDetector
Simple python script supported with BurpBouty profile that helps you to detect SQL injection “Error based” by sending multiple requests with 14 payloads and checking for 152 regex patterns for different databases.
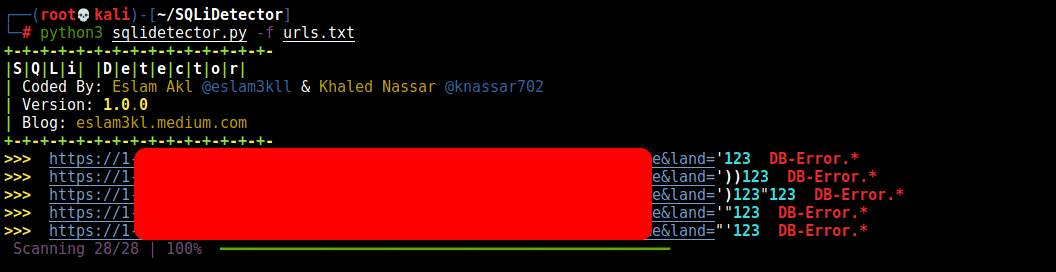
The main idea for the tool is scanning for Error Based SQL Injection by using different payloads like
‘123
”123
`123
“)123
“))123
`)123
`))123
‘))123
‘)123″123
[]123
“”123
‘”123
“‘123
\123
And match for 152 error regex patterns for different databases.
How does it work?
It’s very simple, just organize your steps as follows
- Use your subdomain grabber script or tools.
- Pass all collected subdomains to httpx or httprobe to get only live subs.
- Use your links and URLs tools to grab all waybackurls like waybackurls, gau, gauplus, etc.
- Use URO tool to filter them and reduce the noise.
- Grep to get all the links that contain parameters only. You can use Grep or GF tool.
- Pass the final URLs file to the tool, and it will test them.
The final schema of URLs that you will pass to the tool must be like this one
https://aykalam.com?x=test&y=fortest
http://test.com?parameter=ayhaga
Download
git clone https://github.com/eslam3kl/SQLiDetector.git
cd SQLiDetector
pip3 install -r requirements.txt
Use

BurpBounty Module
I’ve created a burpbounty profile that uses the same payloads add injecting them at multiple positions like
- Parameter name
- Parameter value
- Headers
- Paths
I think it’s more effective and will be helpful for POST requests that you can’t test them using the Python script.
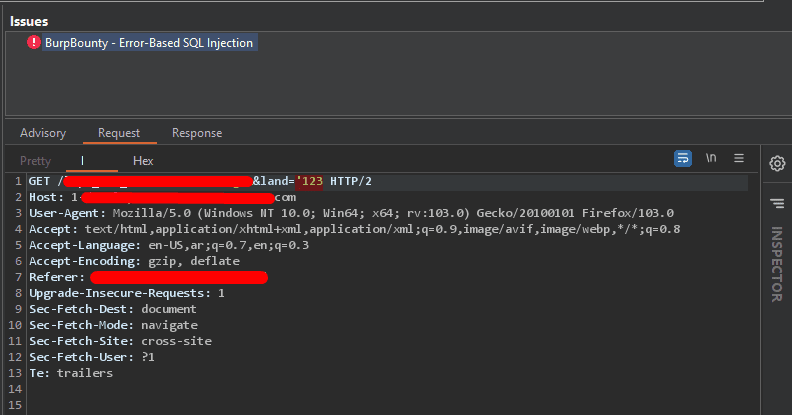
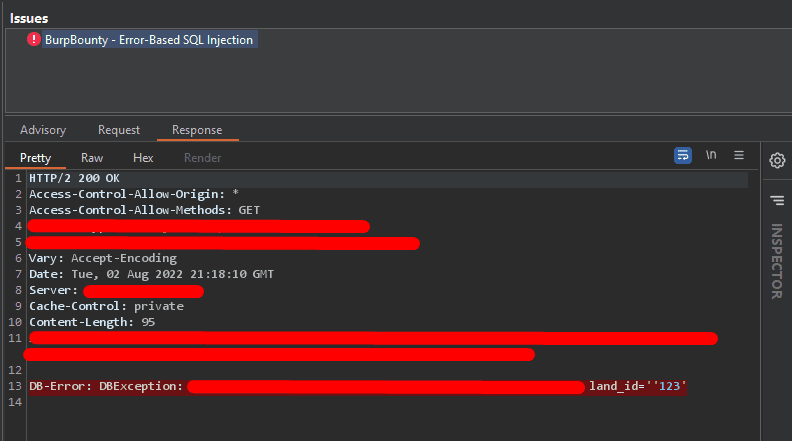
How does it test the parameter?
What’s the difference between this tool and any other one? If we have a link like this one https://example.com?file=aykalam&username=eslam3kl so we have 2 parameters. It creates 2 possible vulnerable URLs.
- It will work for every payload like the followinghttps://example.com?file=123’&username=eslam3kl
https://example.com?file=aykalam&username=123′
- It will send a request for every link and check if one of the patterns is existing using regex.
- For any vulnerable link, it will save it in a separate file for every process.
Source: https://github.com/eslam3kl/





