See-SURF: Python based scanner to find potential SSRF parameters
See-SURF
A Python-based scanner to find potential SSRF parameters in a web application.
Motivation
SSRF being one of the critical vulnerabilities out there in the web, I see there was no tool which would automate finding potentially vulnerable parameters. See-SURF can be added to your arsenal for recon while doing bug hunting/web security testing.
Features
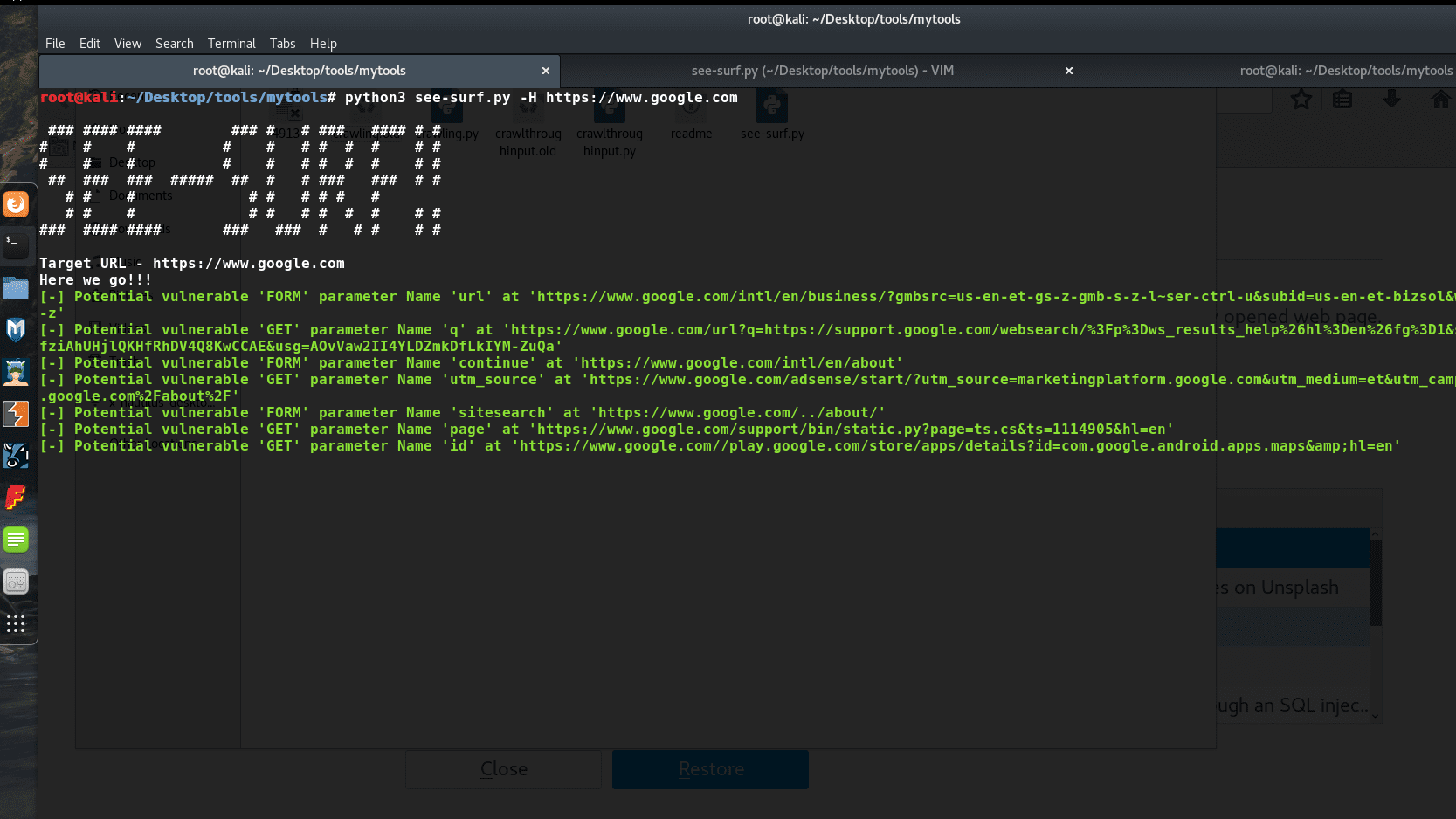
- Matches any GET URL Parameters containing keyword web/url (MORE TO BE ADDED).
Example google.com/url=https://yahoo.com
Also,
checks the parameter values for any URL or IP address passed.
Example: google.com/q=https://yahoo.com - Matches any POST request INPUT params with “Name” attribute containing keyword web/url(MORE TO BE ADDED)
Also,
matches Values and Placeholder attribute containing a URL pattern.
Example:
<input type=”text” name=”url” value=”https://google.com” placeholder=”https://msn.com”> - Multiple conditions to cut down false positives, as crawling pulls up a lot of stuff. Only the same domain is crawled for now.
- By default, normal mode is On, with the verbose switch you would see the same vulnerable param in different endpoints. The same parameter may not be sanitized at all places. But verbose mode generates a lot of noise.
Example:
https://google.com/abc/1/urlToConnect=https://yahoo.com>
https://google.com/123/urlToConnect=https://yahoo.com - Supply cookies for an authenticated scanning.
- Comments on almost every logic so people who would like to contribute can understand easily.
- Makes an external request with the vulnerable parameter to confirm the possibility of SSRF
Installation
git clone https://github.com/In3tinct/See-SURF.git
cd See-SURF/
pip3 install BeautifulSoup4
pip3 install requests
Use
[-] This would run with default threads=10, no cookies/session and NO verbose mode
python3 see-surf.py -H https://www.google.com
[-] Space separate Cookies can be supplied for an authenticated session crawling
python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2
[-] Supplying no. of threads and verbose mode (VERBOSE MODE IS NOT RECOMMENDED IF YOU DON’T WANT TO SPEND LONGER TIME BUT THE POSSIBILITY OF BUG FINDING INCREASES)
python3 see-surf.py -H https://www.google.com -c cookie_name1=value1 cookie_name2=value2 -t 20 -v
By default, normal mode is On, with the verbose switch you would see the same potential vulnerable param in different endpoints. (the Same parameter may not be sanitized at all places. But verbose mode generates a lot of noise.)
Example:
https://google.com/abc/1/urlToConnect=https://yahoo.com
https://google.com/123/urlToConnect=https://yahoo.com
Tutorial
Copyright (C) 2019 In3tinct