Server-Side Request Forgery (SSRF) vulnerable Lab
Server-Side Request Forgery (SSRF) vulnerable Lab
This repository contains PHP codes which are vulnerable to Server-Side Request Forgery (SSRF) attacks.
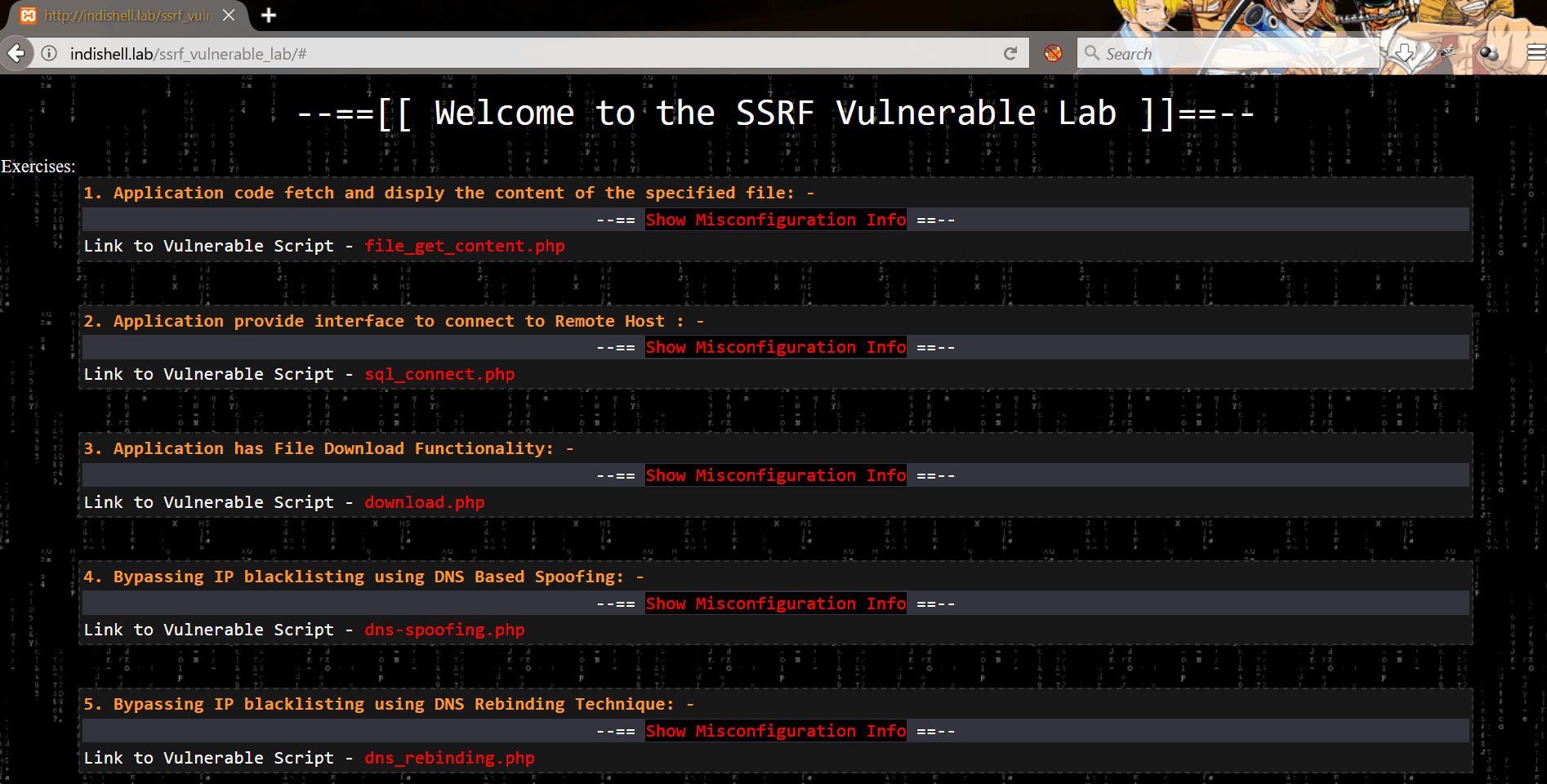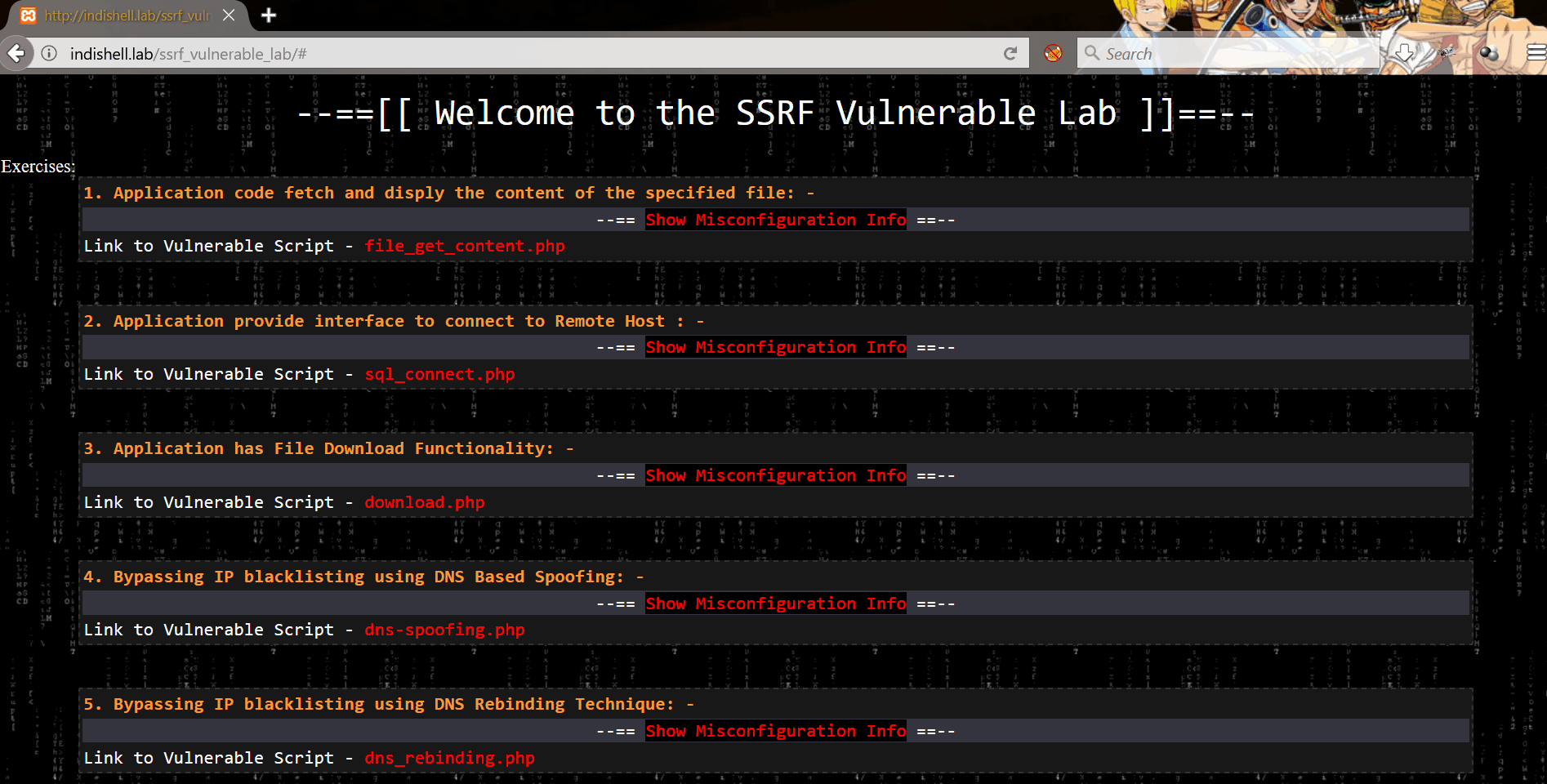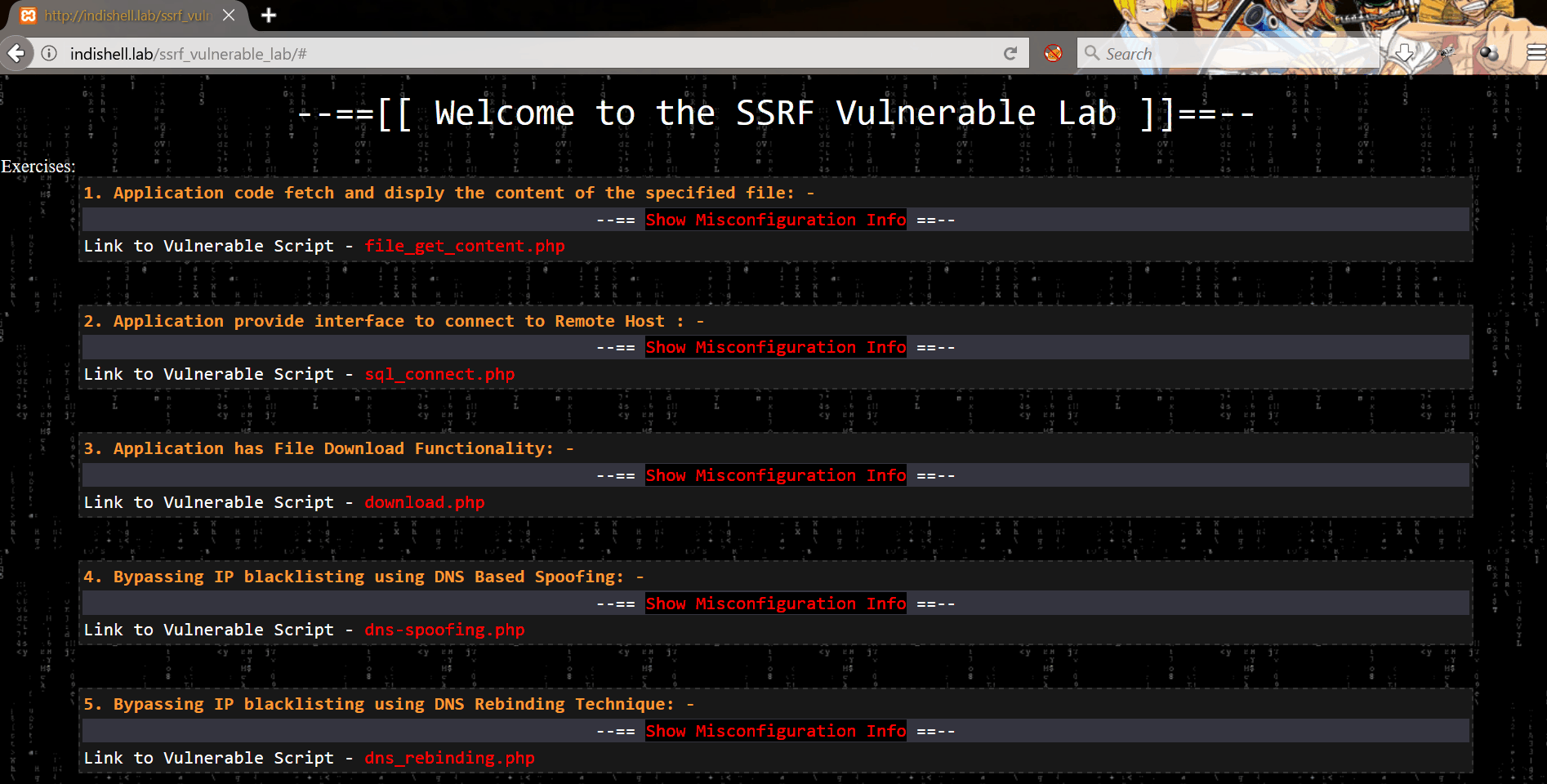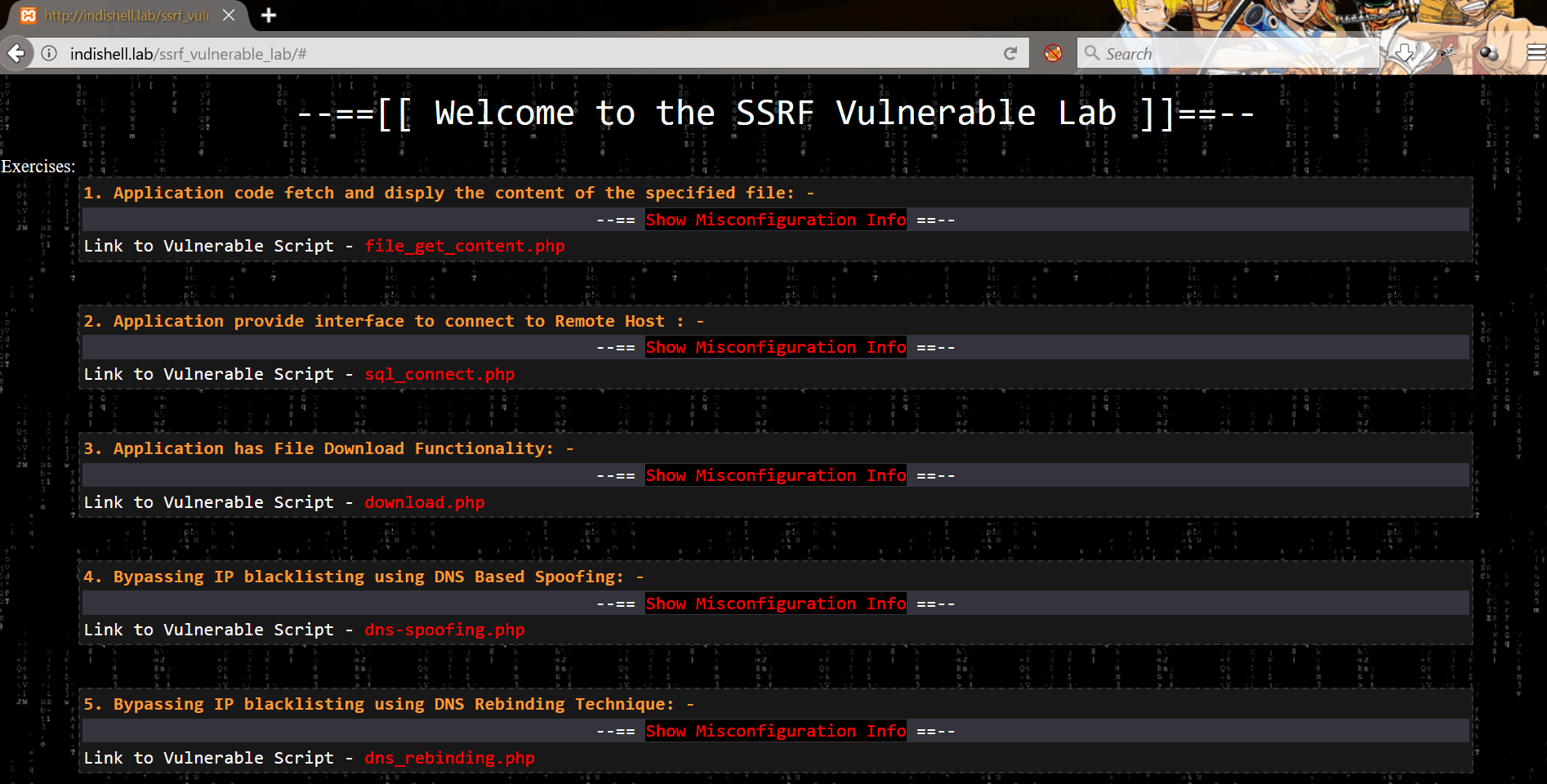
Vulnerable codes are meant to demonstrate SSRF for below mentioned 5 scenarios:
1. Application code fetch and display the content of the specified file
In a programming language, there are functions which can fetch the content of a locally saved file. These functions may be capable of fetching the content from remote URLs as well as local files (file_get_contents in PHP).
This functionality can be abused if application is not prepending any string to the user-supplied data to fetch the content from a file i.e application is not prepending and directory name or path to the user-supplied data.
In this case, application data fetching function process the schemes like “http://” or “file://”. When the user will specify the remote URL in place of file name like “http://localhost”, data fetching function extract the data from the specified URL.
If an application is prepending any data string (for example any directory name) to user data, in that case, “http://” or “file://” scheme won’t work and SSRF vulnerability exploitation is not possible.
Guide to Exploitation of Scenario 1
2. The application provides an interface to connect to Remote Host
The web application has interface allow a user to specify any IP with any port. Here application may have functionality like, it tries to connect to service like “MySQL”, “LDAP” etc.
The application expects a user to specify the remote server hostname/IP, username and password in input fields. The application tries to connect to the remote server over a specified port. Here, the application tries to communicate to remote service listening on a specific port. When vulnerable code has the functionality to connect to a server like MySQL and user-specified the SMB port, the vulnerable application will try to communicate to SMB service using MySQL server service packets. Now, a port is open, but services are not able to communicate due to a difference in way of communication.
This behavior can be exploited to perform internal network scanning not just to enumerate IPs but Ports as well on those live IPs.
Guide to Exploitation of Scenario 2
3. Application has File Download Functionality
In this case, an attacker can exploit this functionality to perform IP scanning inside the network where an application server is hosted. The function which performs the task of downloading a file from a server, can download file not just from a local server but also from SMB path as well. This is something which can help an attacker to figure out the windows based machines in the network.
Web application hosted on Windows OS will process the SMB path as well if file download functionality is processing user input without prepending any data.
Guide to Exploitation of Scenario 3
4. Bypassing IP blacklisting using DNS Based Spoofing
The script has functionality which allows a user to fetch data from remote URL. User needs to specify the remote URL with any IP or domain name.
The script performs to check if a user has specified the input as “localhost”, “Internal IPs” or “Reserved IPs”. If domain/IP specified by a user is blacklisted, the script will not fetch the content and stop processing.
Guide to Exploitation of Scenario 4
5. Bypassing IP blacklisting using DNS Rebinding Technique
Application has implemented blacklisting of not just internal and private range IPs but also resolve the user-supplied domain to its IP and again perform check if resolved is blacklisted or not.
In this case, DNS based spoofing trick will also not work to access the content hosted on internal/Reserved IP. Application code performs domain resolution to its IP and again perform blacklisted IP check for the resolved IP.
Guide to Exploitation of Scenario 5
6. SSRF in HTML to PDF generator script
This the scenrio of the web app which is using HTML to PDF generator script and passing untrusted user supplied data to HTML file which is processed by HTML to PDF generator.
Guide to Exploitation of Scenario 6