StackRox Kubernetes Security Platform v4.1.1 releases
StackRox Kubernetes Security Platform
The StackRox Kubernetes Security Platform performs a risk analysis of the container environment, delivers visibility and runtime alerts, and provides recommendations to proactively improve security by hardening the environment. StackRox integrates with every stage of the container lifecycle: build, deploy, and runtime.
The StackRox Kubernetes Security platform is built on the foundation of the product formerly known as Prevent, which itself was called Mitigate and Apollo. You may find references to these previous names in the code or documentation.
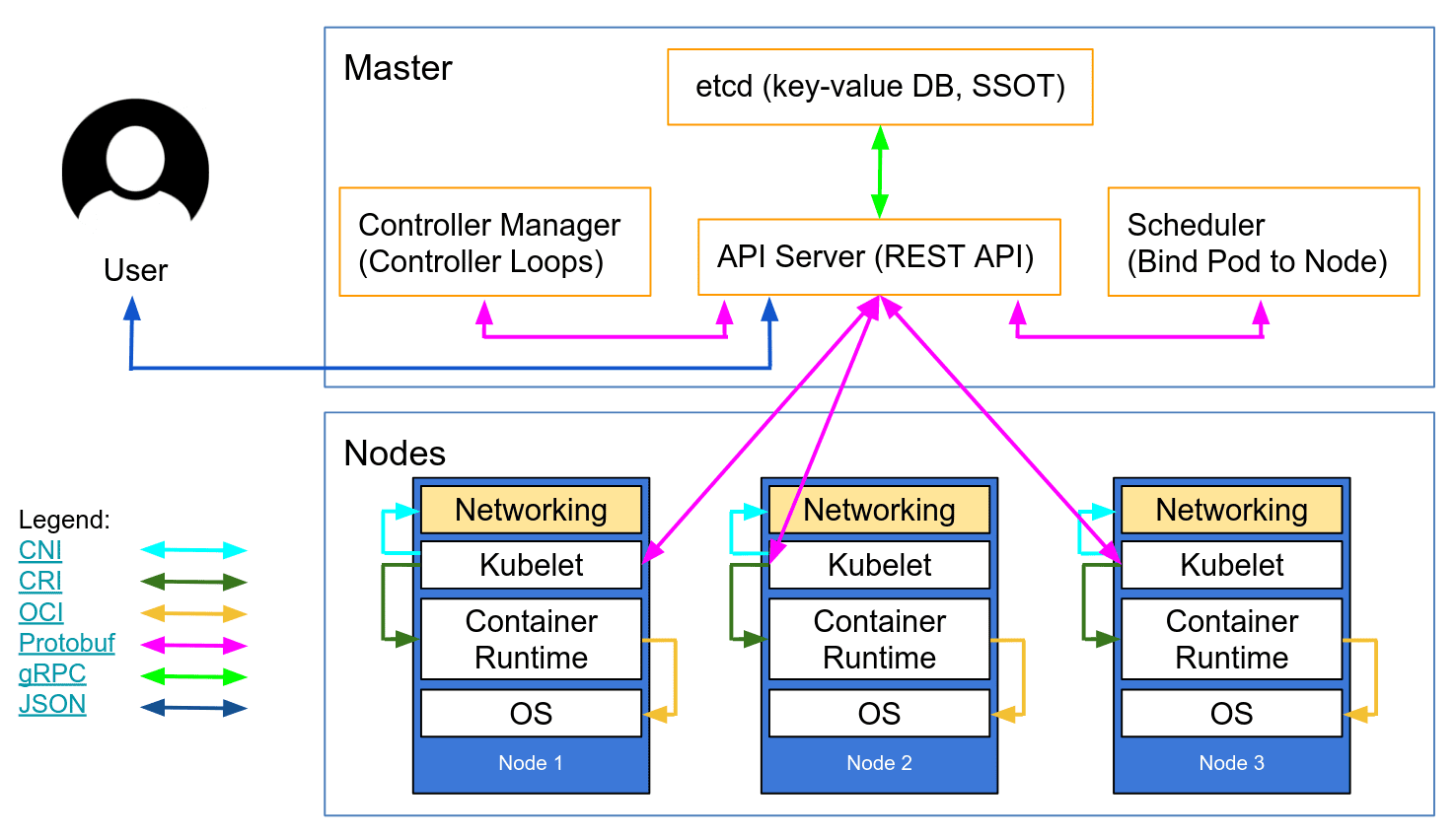
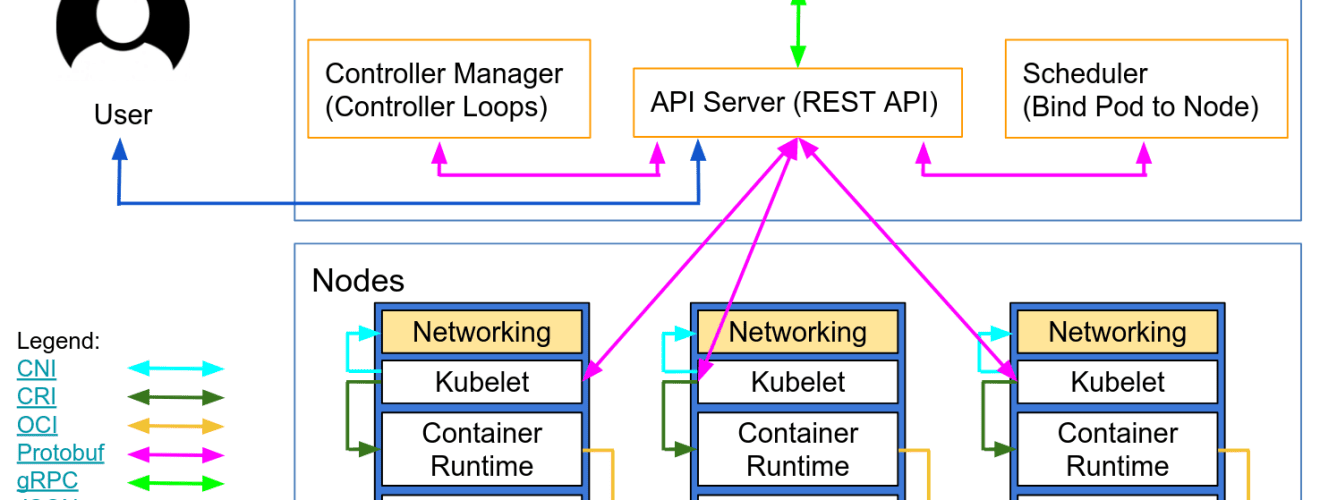
Dependencies and Recommendations for Running StackRox
The following information has been gathered to help with the installation and operation of the open source StackRox project. These recommendations were developed for the Red Hat Advanced Cluster Security for Kubernetes product and have not been tested with the upstream StackRox project.
Recommended Kubernetes Distributions
The Kubernetes Platforms that StackRox has been deployed onto with minimal issues are listed below.
- Red Hat OpenShift Dedicated (OSD)
- Azure Red Hat OpenShift (ARO)
- Red Hat OpenShift Service on AWS (ROSA)
- Amazon Elastic Kubernetes Service (EKS)
- Google Kubernetes Engine (GKE)
- Microsoft Azure Kubernetes Service (AKS)
If you deploy into a Kubernetes distribution other than the ones listed above you may encounter issues.
Recommended Operating Systems
StackRox is known to work on the recent versions of the following operating systems.
- Ubuntu
- Debian
- Red Hat Enterprise Linux (RHEL)
- CentOS
- Fedora CoreOS
- Flatcar Container Linux
- Google COS
- Amazon Linux
- Garden Linux
Recommended Web Browsers
The following table lists the browsers that can view the StackRox web user interface.
- Google Chrome 88.0 (64-bit)
- Microsoft Internet Explorer Edge
- Version 44 and later (Windows)
- Version 81 (Official Build) (64-bit)
- Safari on MacOS (Mojave) – Version 14.0
- Mozilla Firefox Version 82.0.2 (64-bit)
Changelog v4.1
Added Features
- Two new default permission sets
Vulnerability Management ConsumerandVulnerability Management Adminhave been added for vulnerability management.Vulnerability Management Consumerprovides read-only access to analyze vulnerabilities and initiate risk acceptance process.Vulnerability Management Adminprovides administrative access to analyze vulnerabilities, generate reports, and manage risk acceptance process.
- A default role
Network Graph Viewerhas been added that provides sufficient privileges to display network graphs. - A new command
roxctl central loginhas been added that allows to use a user’s token within roxctl instead of an API token or admin password. - ROX-15447: A new
DelegatedRegistryConfigAPI at/v1/delegatedregistryconfighas been added that provides dynamic configuration for local registry scanning (replacesROX_FORCE_LOCAL_IMAGE_SCANNING). - A new environment variable
ROX_DISABLE_SIGNATURE_FETCHINGhas been added to Central and Sensor which stops fetching image signatures in case the signature verification feature shall not be used.
You may set this in case there’s too much load on registries due to attempts to fetch image signatures.
Note that if the environment variable is set, no signatures will be fetched and thus the signature verification feature cannot be used. - ROX-16532: Resource limits and requests for the node-inventory container can now be configured via the operator.
- A new environment variable
ROX_SCAN_TIMEOUThas been added to Sensor which allows for customizing the image scan timeout used in Sensor initiated scans. - ROX-17365: A new environment variable
ROX_DELEGATED_SCANNING_DISABLEDhas been added that disables delegated scanning capabilities while leaving other local scanning capabilities intact. - ROX-16703: Helm setting
scanner.disable=falsenow valid for any secured cluster (instead of OpenShift only). This enables scanner slim to be installed in non-OCP secured clusters.
Removed Features
- ROX-14398: As announced in 3.74, the permission
Accessreplaces the deprecated permissionRole. - ROX-14398: As announced in 3.74, the
Scope Managersystem role and permission set will be removed. If existing product installations do have customer references to either theScope Managersystem role or theScope Managersystem permission set, then the referenced object will be adjusted to contain a description mentioning its deprecation. Furthermore, the objects will not be marked as system resources, and will not be supported anymore. - ROX-17031: env var
ROX_FORCE_LOCAL_IMAGE_SCANNINGhas been removed and replaced by theDelegatedRegistryConfigAPI. - ROX-13888: As announced in 3.74, the permission
WorkflowAdministrationreplaces the deprecated permissionsVulnerability ReportsandPolicy. - KernelModule collection has been removed, following deprecation in 4.0.
- Secured clusters configured to use KernelModule collection will automatically switch to EBPF
Deprecated Features
- Vulnerability Management 1.0 sections Image CVEs, Image Components, Images, Deployments, and Namespaces are deprecated and will be removed in the future. Once removed, use Vulnerability Management 2.0 for managing workload vulnerabilities.
- Custom Security Context Constraints (SCC) (e.g.:
stackrox-collector,stackrox-admission-control,stackrox-sensor) are deprecated and will be removed in the future.
Users should ensure that those SCCs are not being used by workloads other than Stackrox/RHACS. - The default permission set
Vulnerability Management Approveris deprecated and will be removed in a future release. Customers are advised to useVulnerability Management Adminpermission set instead. WhenVulnerability Management Approverpermission set is removed existing roles using it will be updated to useVulnerability Management Admin. - The default permission set
Vulnerability Management Requesteris deprecated and will be removed in a future release. Customers are advised to useVulnerability Management Consumerpermission set instead. WhenVulnerability Management Requesterpermission set is removed existing roles using it will be updated to useVulnerability Management Consumer. - The default permission set
Vulnerability Report Creatoris deprecated and will be removed in a future release. Customers are advised to useVulnerability Management Adminpermission set instead. WhenVulnerability Report Creatorpermission set is removed existing roles using it will be updated to useVulnerability Management Admin.
Technical Changes
- The Central PVC stackrox-db is no longer required after this upgrade. To obsolete existing PVC, please check the docs online.
- The output of
roxctl central whoaminow includes the username as well. - Helm setting
collector.nodeInventoryResourceshas been renamed tocollector.nodeScanningResources. - ROX-16959: Helm setting
admissionController.replicashas been added to configure admission controller replicas. - The k8s-istio.zip file inside of scanner-vuln-updates.zip (the file downloaded from https://install.stackrox.io/scanner/scanner-vuln-updates.zip for updating Scanner vulnerabilities in offline-mode)
is no longer needed. We will continue to populate it to support older versions of the product, but it will be ignored. - The time interval used to determine the frequency to scan orchestrator-level components (Kubernetes, OpenShift, Istio) is now configurable
via ROX_ORCHESTRATOR_VULN_SCAN_INTERVAL. - Image Integrations will now be synced with secured clusters that have local scanning enabled.
Install
Copyright (C) 2022 stackrox