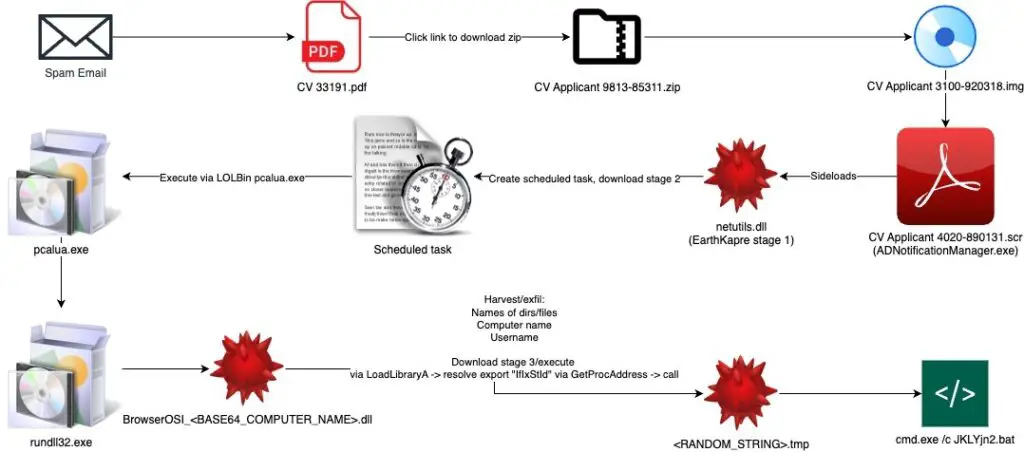
EarthKapre/RedCurl Attack Chain | Source: TRU
Researchers at eSentire Threat Response Unit (TRU) uncovered a sophisticated cyber espionage campaign by RedCurl/EarthKapre, a threat group notorious for targeting private-sector organizations. This latest attack chain showcases the group’s ability to weaponize legitimate tools, leveraging DLL sideloading techniques and cloud-based infrastructure to stealthily infiltrate networks and exfiltrate sensitive data.
The attack begins with a seemingly benign job application. Victims receive a spam email containing an Indeed-themed PDF attachment that lures them into downloading a ZIP archive. Inside this archive lies an ISO image file, mimicking a job applicant’s CV.
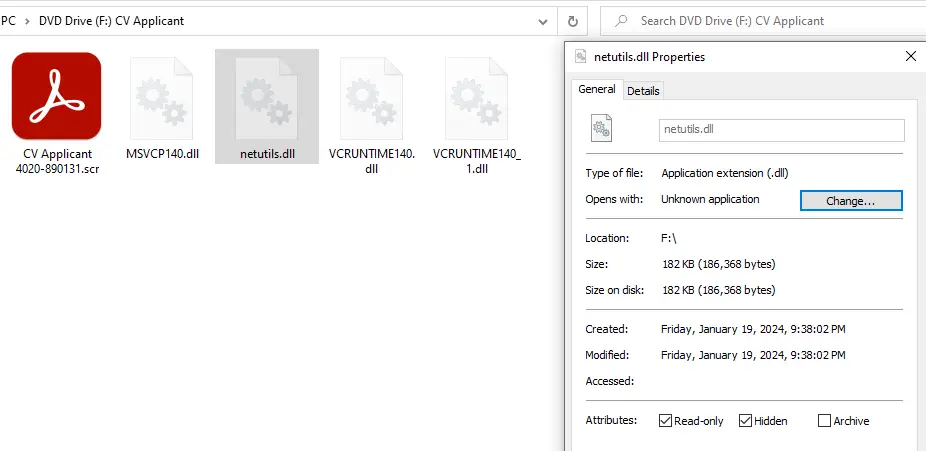
Once the victim mounts the ISO file, they see only one file: “CV Applicant .scr”. This is actually a signed Adobe executable (ADNotificationManager.exe), which, when opened, sideloads the EarthKapre loader (netutils.dll). As TRU notes, “Upon the victim opening the .scr file, the RedCurl/EarthKapre dll (netutils.dll) is side loaded”—a clever technique to bypass security mechanisms.
RedCurl/EarthKapre deploys a multi-stage attack that involves intricate encryption techniques and staged payload delivery. The first stage, a simple downloader, is responsible for retrieving and executing the next phase.
According to TRU, the malware leverages bcrypt.dll APIs to derive an AES encryption key by hashing a predefined string. This technique, previously reported by Trend Micro, allows the malware to encrypt and decrypt its payload dynamically. TRU explains, “The first 16 bytes of the generated SHA256 hash is used as the AES key for decrypting strings via BCryptDecrypt”.
Once decrypted, the malware proceeds to create a scheduled task that ensures persistence. The task, intriguingly named BrowserOSR-<BASE64_ENCODED_COMPUTER_NAME>, executes an action that triggers pcalua.exe, a Windows LOLBin (Living-Off-the-Land Binary), to run the next payload.
TRU highlights that “because the trigger time for the task is a time that technically occurs in the past, it is not immediately triggered. The task is set to run every hour indefinitely.” This approach helps evade immediate detection while ensuring execution of the next stage.
The malware’s communication with its Command-and-Control (C2) infrastructure is designed to be both stealthy and resilient. The first-stage payload sends an HTTP POST request to the C2 server (sm.vbigdatasolutions.workers[.]dev), requesting the second-stage payload.
Interestingly, TRU notes that “Wininet.dll is then loaded and several APIs are resolved”, allowing the malware to communicate covertly. The second-stage payload is delivered in an encrypted format and decrypted using a hardcoded XOR key before being stored in the victim’s AppData directory.
TRU’s researchers were able to replicate the decryption process using a Python script, demonstrating how the payload is extracted and written to disk. The decrypted binary then executes, launching the final stage of the attack.
Once inside the target’s environment, RedCurl/EarthKapre shifts its focus to data collection and exfiltration. The attackers employ a variety of reconnaissance techniques, leveraging Windows utilities like WMIC and Sysinternals AD Explorer.
TRU’s analysis details that the final stage executes a batch script (JKLYjn2.bat), which gathers the following information:
- User account details (net localgroup)
- System information (systeminfo)
- Disk space and antivirus products (wmic logicaldisk get description,name,Size,FreeSpace)
- Active Directory snapshots (ad.exe -accepteula -snapshot)
- Password-protected data archiving (7-Zip)
To exfiltrate the data, RedCurl/EarthKapre takes an unconventional route—leveraging Tab Digital’s cloud storage service. As TRU notes, “Upload the collected data occurs via a PowerShell PUT request to C2 ‘mia.nl.tab[.]digital’”. This method not only blends in with normal traffic but also complicates detection efforts.
A fascinating aspect of this campaign is its reliance on Cloudflare Workers to host C2 infrastructure. This serverless execution environment offers anonymity and resilience, though it also imposes some limitations.
As TRU points out, “there are some limitations to Cloudflare Workers free tier – the threat actors are only able to receive 100,000 requests per day.” This means that RedCurl/EarthKapre’s operations could be disrupted by excessive requests, a tactic TRU successfully used to temporarily cripple the attacker’s infrastructure.
Related Posts:
- SocGholish Campaign Targets Business Networks via Fake Browser Updates
- CVE-2024-6387: Critical OpenSSH Unauthenticated RCE Flaw ‘regreSSHion’ Exposes Millions of Linux Systems
- eSentire Exposes Ongoing More_eggs Malware Campaign Targeting Job Seekers
- AdsExhaust: New Adware Masquerading as Oculus Installer Wreaks Havoc