Infection chain | Image: CRIL
Cyble Research and Intelligence Labs (CRIL) has uncovered a new and highly sophisticated cyberattack that leverages Visual Studio Code (VSCode) to establish unauthorized remote access to victim systems. This attack demonstrates a high level of stealth, bypassing common detection mechanisms and exploiting trusted software to execute malicious actions.
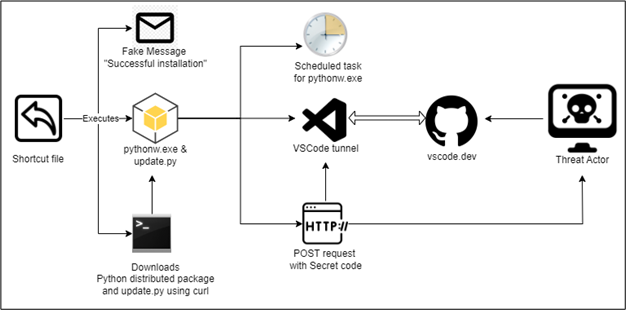
The attack begins with the distribution of a suspicious .LNK file, masquerading as a legitimate installer. The file is delivered through phishing emails, a common method for luring unsuspecting users into initiating the attack. Upon execution, the .LNK file displays a fake success message in Chinese (“安裝成功”), tricking the user into believing that the installation was successful. However, in the background, the .LNK file silently downloads a Python distribution package, along with additional malicious components, using the curl utility.
The downloaded Python script, “update.py,” executes in an obfuscated manner, ensuring that it remains undetected by security tools. Remarkably, at the time of CRIL’s investigation, the script had zero detections on VirusTotal. This provides the attackers with an advantage, allowing the script to slip past standard security measures.
Once launched, the script checks whether VSCode is installed on the victim’s machine. If not, it downloads the VSCode Command Line Interface (CLI) from a legitimate Microsoft source. With VSCode in place, the script creates a scheduled task named “MicrosoftHealthcareMonitorNode,” granting the attackers persistence on the system. This task ensures the script is re-executed regularly, even after reboots, making it harder to eliminate the malware.
VSCode’s Remote – Tunnels extension is designed to connect users to remote machines securely. However, in this campaign, the attackers have found a way to misuse this functionality. By creating a remote tunnel through VSCode, the attackers establish a gateway to the victim’s system. This tunnel allows them to control the machine remotely without relying on typical methods like SSH, making their intrusion difficult to trace.
The attackers then extract an activation code, which is necessary for authenticating their remote session. This code is retrieved from VSCode’s output files and used to associate the victim’s system with the attackers’ GitHub account. With this activation code in hand, they gain full access to the victim’s system through the GitHub login page, opening the door to further malicious activities.
Once inside the system, the attackers begin exfiltrating valuable data. They gather information from key system directories, including program files, user data, and running processes. This data, along with sensitive system details such as the victim’s location, user privileges, and system language settings, is encoded in Base64 and transmitted to the attackers’ command-and-control (C&C) server.
With access to the system, the attackers can execute commands, manipulate files, and install additional malware. They can even deploy tools like Mimikatz and LaZagne to extract passwords, expanding their control over the compromised system.
This attack method bears similarities to tactics used by the Chinese advanced persistent threat (APT) group known as Stately Taurus, as noted by Unit42 researchers. This connection suggests that the attackers in this campaign may be leveraging techniques from sophisticated espionage groups.
Related Posts:
- Malicious VSCode extensions steal PII and enable backdoors
- Chinese APT Stately Taurus Exploits Visual Studio Code in Cyberespionage Attacks