Stealthy New Golang Trojan Exploits Fake Certificates for Evasive Communication
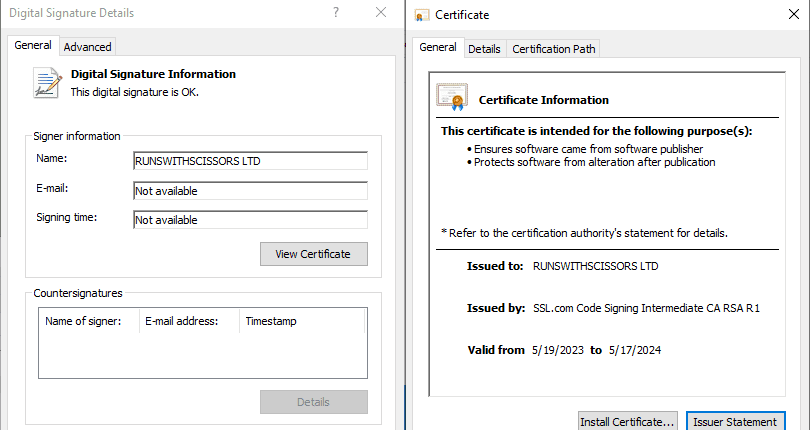
Security researchers at SonicWall Capture Labs have discovered a cunning new Trojan written in the Golang programming language. This insidious malware employs a range of deceptive tactics, including geographical checks and the installation of a fraudulent root certificate, to maintain hidden communication channels with its command-and-control (C2) server.
The Threat Unmasked

There is no signer, email or creation date with this certificate
This sophisticated Trojan first takes a snapshot of the infected system, likely collecting vital information for targeted attacks. It then audaciously installs a fake root certificate in the Windows registry. This nefarious step allows it to intercept and potentially manipulate encrypted HTTPS traffic, leaving users vulnerable to data theft.
While no specific malware family has been linked to this Trojan, researchers warn that the IP and URL addresses involved have been spotted in previous campaigns associated with infamous threats like PureLog Stealer, AgentTesla, and GuLoader.
Under the Hood
Technical analysis reveals unusual aspects of this Trojan. It disguises itself as a benign-looking Golang executable, but closer inspection paints a different picture. Suspicious timestamps, a bogus certificate issuer, and the presence of a Linux-specific ELF section highlight its deceitful nature.
Furthermore, the malware utilizes legitimate GitHub packages to generate and exfiltrate screenshots of victim machines. It also queries system information for details like UUIDs, remote IPs, usernames, and Windows versions – critical pieces in the attack puzzle.
The malware’s communication strategy is particularly alarming. It attempts to determine the victim’s location before contacting its C2 server. Once a connection is established via a seemingly innocuous domain (‘daily-mashriq[.]org’), the malware starts transmitting stolen data using advanced encryption and a unique user-agent.
The Danger is Real
This Golang Trojan’s evasive maneuvers underscore the evolving nature of cyberthreats. Its ability to bypass security measures and steal sensitive information poses a grave risk to individuals and organizations.
How to Stay Safe
- Maintain vigilance: Stay updated on the latest cybersecurity news and threats.
- Patch and update: Install security patches and software updates promptly.
- Be skeptical: Exercise caution when opening attachments or clicking links, even from familiar sources.
- Employ robust security solutions: Use a comprehensive antivirus/anti-malware suite and consider advanced endpoint protection.
In Conclusion
This latest discovery serves as a stark reminder of the importance of proactive cybersecurity defense. By staying informed and implementing robust security practices, we can significantly reduce the risk of falling victim to these ever-evolving threats.





