Morphisec Labs has identified a surge in cyber activity associated with the Sticky Werewolf group, a threat actor with suspected geopolitical or hacktivist ties. This elusive group, first detected in April 2023, has expanded its operations from targeting public organizations in Russia and Belarus to hitting various sectors, including pharmaceuticals, research institutes, and most recently, the aviation industry.
Sticky Werewolf’s latest campaign focuses on the aviation industry, employing sophisticated phishing tactics. The attackers pose as representatives from AO OKB Kristall, a Moscow-based company involved in aircraft and spacecraft production and maintenance. The phishing emails, appearing to come from the First Deputy General Director of AO OKB Kristall, invite recipients to a video conference on future cooperation. These emails contain password-protected archive attachments designed to deceive the recipient into executing malicious files.
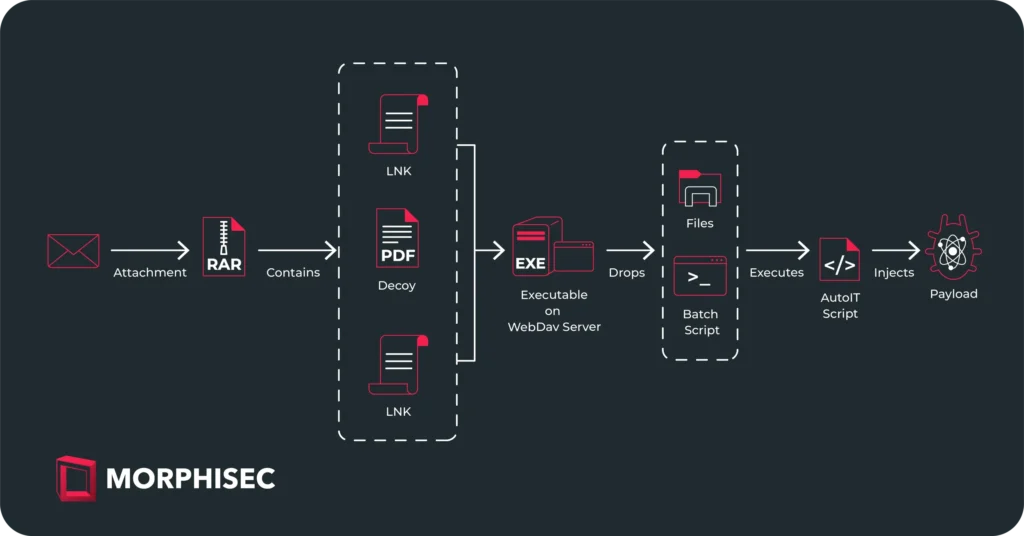
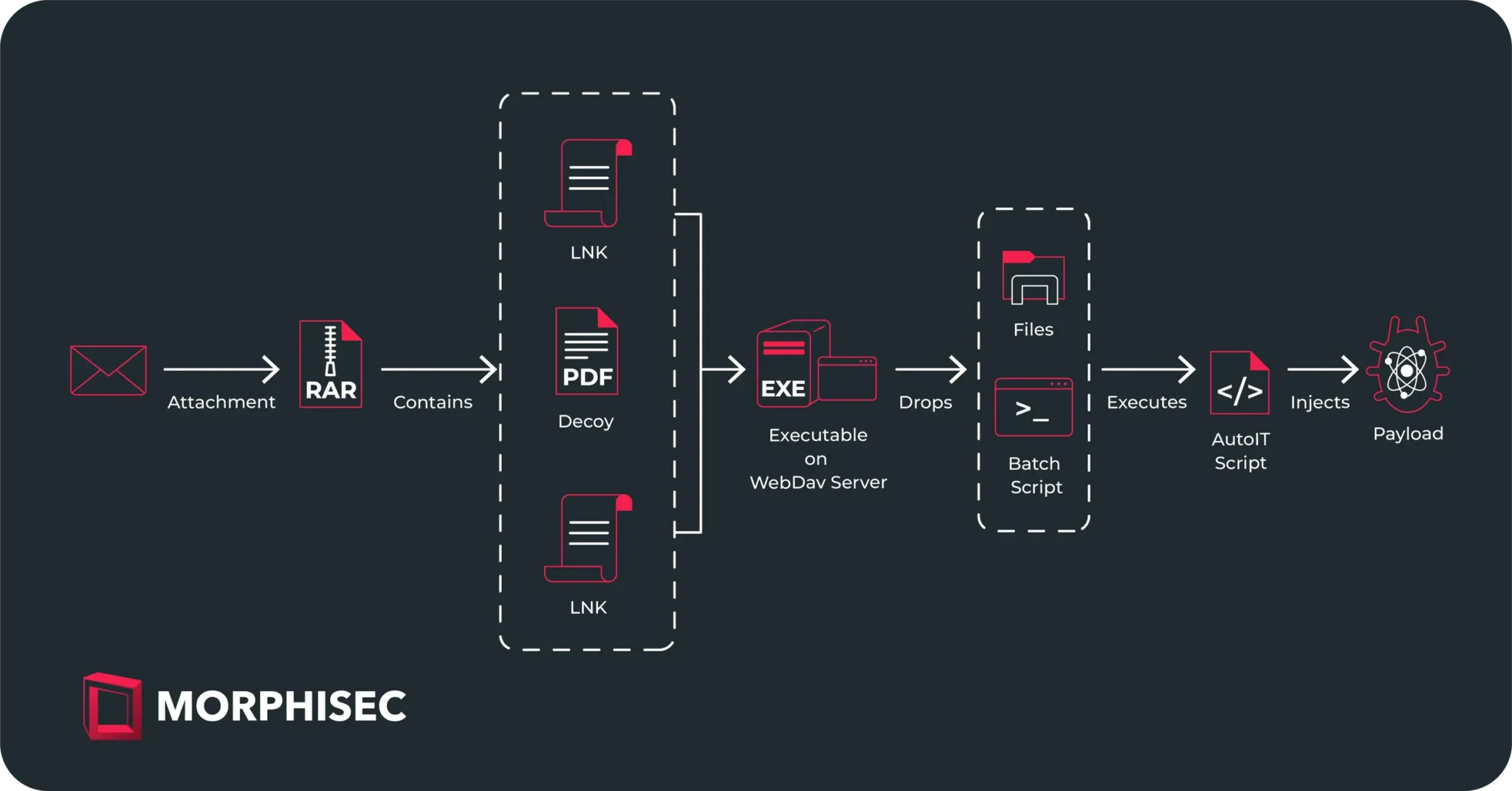
Unlike previous campaigns that used phishing emails with links to malicious files hosted on platforms like gofile.io, this latest campaign delivers malware through an archive file attachment. Here’s a breakdown of the infection chain:
- Email Attachment:
- The phishing email contains an archive with a decoy PDF and two LNK files masquerading as DOCX documents (e.g., “Meeting agenda” and “Mailing list”).
- The PDF serves as a distraction, providing seemingly legitimate content to reduce suspicion.
- LNK Files:
- When executed, the LNK files point to an executable hosted on a WebDAV server.
- This initiates a batch script that launches an AutoIt script, ultimately injecting the final payload.
- Payload Execution:
- The LNK file triggers multiple actions, including adding a registry entry for persistence and copying decoy images to local directories.
- The executable from the network share is an NSIS self-extracting archive, part of a crypter named CypherIT, used to deliver the malicious payload.
The targeting of the aviation industry raises significant concerns due to the potential impact on critical infrastructure and sensitive information. The use of social engineering tactics, combined with advanced malware delivery methods, underscores the need for heightened vigilance and robust cybersecurity measures within the sector.
While the exact motives behind Sticky Werewolf’s activities remain unclear, their expanding scope and increasingly sophisticated tactics necessitate a proactive and coordinated response from the cybersecurity community.