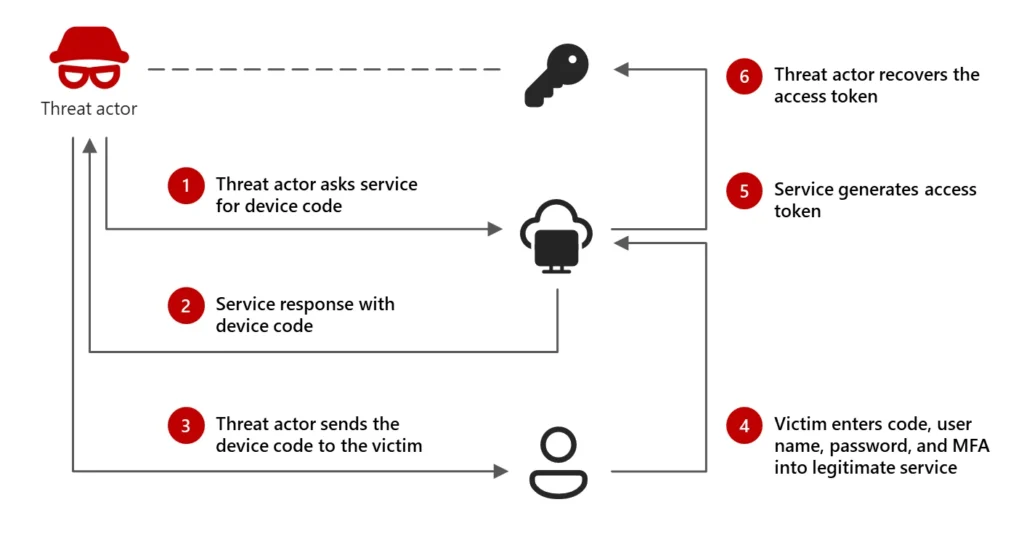
Device code phishing attack cycle
Microsoft Threat Intelligence has uncovered an active and ongoing phishing campaign conducted by the threat actor Storm-2372, a group that Microsoft assesses with medium confidence as aligning with Russian interests, victimology, and tradecraft. This operation, which has been in motion since August 2024, is particularly concerning due to its exploitation of device code authentication, allowing attackers to bypass traditional security measures and gain access to high-value targets without needing valid credentials.
Microsoft explains that Storm-2372’s tactics rely on a social engineering lure that masquerades as messages from widely used applications, including WhatsApp, Signal, and Microsoft Teams. Attackers impersonate prominent individuals relevant to their targets, gaining trust before sending phishing invitations to online meetings. Victims who engage with these fraudulent meeting requests are unknowingly tricked into entering a device code on a legitimate authentication page, effectively handing over their session credentials.
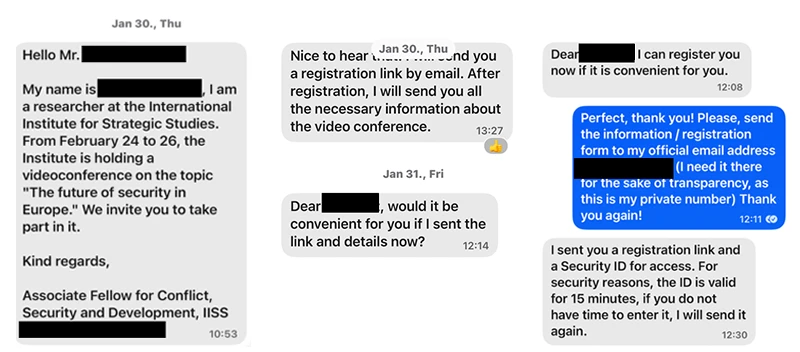
“The phishing attack identified in this blog masquerades as Microsoft Teams meeting invitations delivered through email. When targets click the meeting invitation, they are prompted to authenticate using a threat actor-generated device code. The actor then receives the valid access token from the user interaction, stealing the authenticated session,” Microsoft stated in its report.
Once authenticated, attackers gain access to Microsoft Graph API, enabling them to conduct email harvesting, credential searches, and lateral movement within compromised organizations. Microsoft observed the exfiltration of sensitive emails containing keywords such as “username,” “password,” “admin,” “credentials,” and “gov.”
Microsoft reported that Storm-2372 has recently shifted tactics to leverage Microsoft Authentication Broker’s client ID in the device code sign-in flow. This allows the threat actor to obtain a Primary Refresh Token (PRT), register attacker-controlled devices within Microsoft Entra ID, and gain persistent access to compromised environments.
“Within the past 24 hours, Microsoft has observed Storm-2372 shifting to using the specific client ID for Microsoft Authentication Broker in the device code sign-in flow. Using this client ID enables Storm-2372 to receive a refresh token that can be used to request another token for the device registration service, and then register an actor-controlled device within Entra ID,” the report notes.
This shift in technique suggests that Storm-2372 is adapting its strategy to evade detection and maintain long-term access to infiltrated networks.
Microsoft reports that Storm-2372 is focusing on government agencies, non-governmental organizations (NGOs), IT services, defense, telecommunications, healthcare, higher education, and energy sectors. The campaign is geographically widespread, impacting Europe, North America, Africa, and the Middle East.
The use of regionally appropriate proxies further complicates detection, as attackers attempt to blend into normal login behavior by mirroring the geographical locations of their targets.
Related Posts:
- SpyNote RAT Targets High-Value Individuals in Southern Asia
- Pacific Rim: Sophos Exposes 5 Years of Chinese Cyber Espionage
- Google ban fake ID apps on Play Store