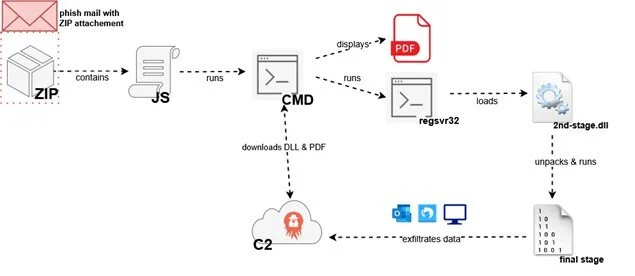
Execution chain of Strela Stealer. Source: SpiderLabs
Trustwave SpiderLabs has published a report on Strela Stealer, a sophisticated infostealer malware that has been active since late 2022, specifically targeting email credentials from Mozilla Thunderbird and Microsoft Outlook users across Europe. The malware has been distributed through large-scale phishing campaigns primarily aimed at users in Spain, Italy, Germany, and Ukraine.
What sets Strela Stealer apart is its focused approach and continuous evolution. Unlike other infostealers that cast a wide net, Strela Stealer precisely targets a narrow data set and specific geographic locations. The attackers have also refined their social engineering tactics over time. Recent campaigns involve forwarding legitimate emails containing invoices, but with the original attachment replaced by a ZIP archive containing the Strela Stealer malware loader.
Threat intelligence suggests that Strela Stealer is likely operated by a single threat actor known as ‘Hive0145’, as IBM X-Force reported. Further analysis of the malware’s infrastructure has traced its Command-and-Control (C2) servers to Russian bulletproof hosting providers, indicating a deliberate operation.
Technical analysis by Trustwave reveals a complex, multi-stage infection chain designed to evade detection and analysis. The initial JScript loader is obfuscated and checks the victim’s locale to ensure it matches German-speaking countries before proceeding. It then fetches a second-stage payload, a packed and obfuscated DLL, from a remote server. This DLL employs techniques like control-flow flattening and junk code insertion to hinder analysis.
The final stage of Strela Stealer is heavily obfuscated and utilizes anti-analysis techniques like opaque predicates, redundant fiber manipulation, and FLS index abuse to further complicate analysis. Once executed, it performs another locale check, targeting Spain, Germany, Italy, Poland, and Ukraine.
The malware then steals email credentials from the targeted email clients and exfiltrates system information, including the list of installed applications, to its command-and-control server.
Users should be wary of unexpected attachments, even in emails from trusted sources, and keep their email clients and operating systems updated to mitigate the risk of infection.
Related Posts:
- Obfuscated JavaScript and WebDAV: Strela Stealer’s New Tools for Credential Theft
- Strela Stealer Surge: Hive0145 Targets European Email Credentials
- Lumma Stealer Malware Campaign Targets Educational Institutions with Deceptive PDF Lures
- Lumma Stealer MaaS: Clipboard Hijacking and LOLBins Used in Latest Campaign
- JavaScript-Based Malware Exploits Steganography for Covert Data Theft