
IBM’s X-Force team has identified a major surge in the distribution of Strela Stealer, a credential-stealing malware linked to the cybercriminal group Hive0145. The malware primarily targets email credentials stored in Microsoft Outlook and Mozilla Thunderbird, posing a significant risk for business email compromise (BEC) across Europe. Recent campaigns have been observed targeting users in Spain, Germany, and Ukraine, with Hive0145 leveraging stolen invoice emails to spread Strela Stealer more effectively.
Strela Stealer’s infection chain begins with authentic-looking phishing emails containing weaponized attachments. In many cases, these emails are real invoice notifications hijacked from previous victims. As IBM X-Force explained, “Hive0145 campaigns have increased in volume, with weekly campaigns as of 17 October 2024.”
In mid-2024, Hive0145 transitioned to using stolen email credentials to distribute phishing emails that appear genuine. By inserting malware into legitimate invoice emails, Hive0145 has refined its approach, creating emails that remain “largely unmodified” except for the attachment, which now contains the malware payload.
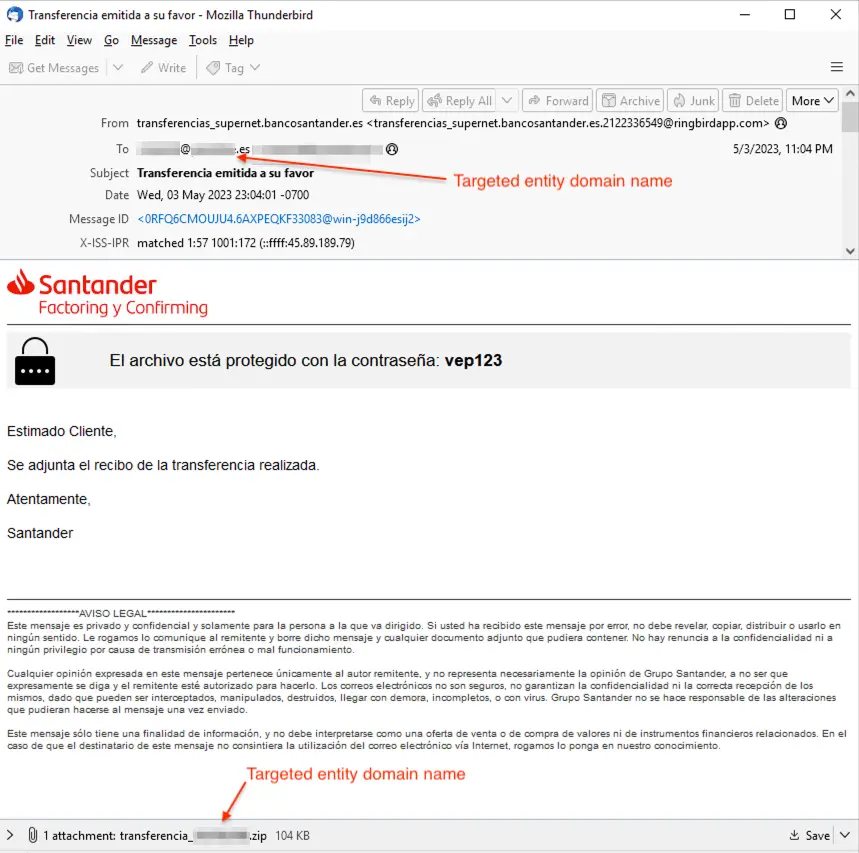
Strela Stealer campaigns target specific language groups, including Spanish, German, and Italian speakers, and have recently expanded to Ukrainian-speaking users. As part of the malware’s infection logic, Hive0145 implemented language checks to ensure relevance. The malware verifies the system’s keyboard language, now including Ukrainian alongside the originally targeted languages. This change signals “a significant development,” IBM X-Force notes, as Hive0145’s expansion to new language regions increases its potential impact.
Hive0145 has employed several advanced techniques to evade detection and improve the effectiveness of Strela Stealer:
- Polyglot Files: These files, used since 2022, can serve as both a DLL and an HTML file, allowing the malware to bypass some security defenses.
- Signed Binaries: Throughout 2023, the group leveraged stolen code-signing certificates, including one from a Brazilian software firm, to disguise the malware as legitimate software.
- Obfuscation and Crypters: Recent campaigns utilize Stellar Loader, a sophisticated crypter designed to evade antivirus detection through heavy obfuscation
IBM X-Force warns organizations to remain vigilant when handling unexpected attachments, especially in languages aligned with recent campaigns.
Related Posts:
- Obfuscated JavaScript and WebDAV: Strela Stealer’s New Tools for Credential Theft
- X-Force Alert: Cybercriminals Zero In on Unsecured Citrix NetScaler Gateways