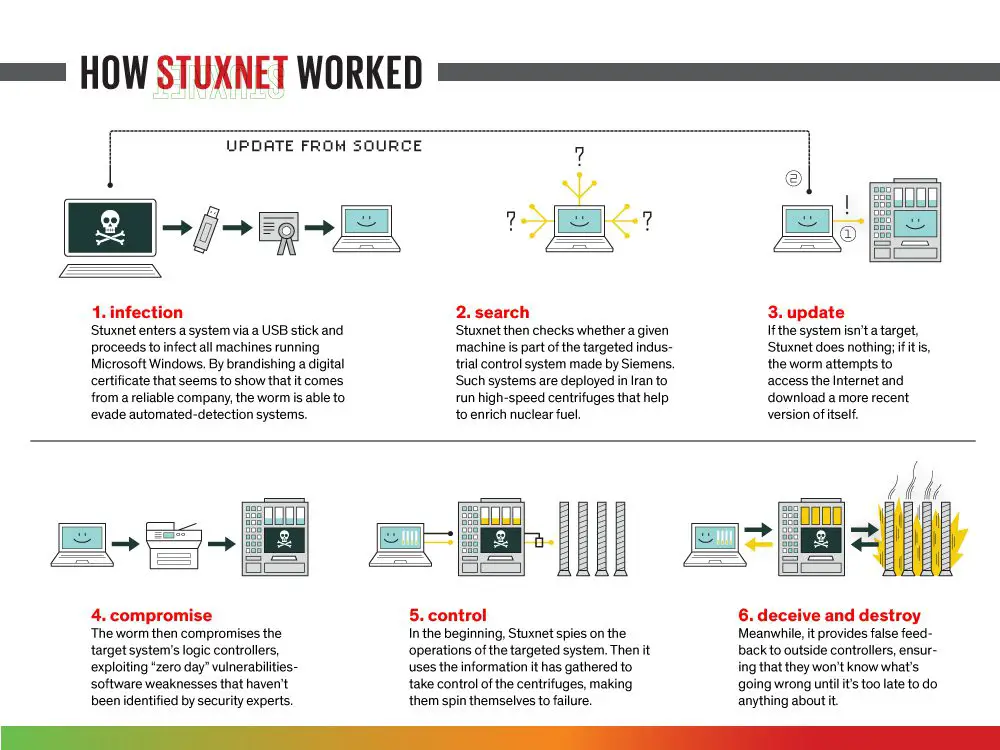
Gigantic Software CEO John Byrd published an article on the subject in Quora about mysterious Stuxnet worm that is now created the most complex software. Stuxnet is a computer worm that was written between 2005 and 2010. This kind of worm may only exist on the U disk at first. Someone finds or receives the U disk from the mail and plugs it into the computer to see what is in it.
When the U disk is plugged into a Windows PC, it will silently run the copy to the machine. There are three ways to run it and switch to another if it is not. At least two methods were not known at the time. It used two kinds of Windows 0day vulnerabilities. Once the worm is running on the computer, it will try to gain administrator rights regardless of whether anti-virus software is installed on the machine.

Image: IEEE
It bypasses most anti-virus software and then uses one of two methods to gain administrative rights based on the version of Windows it is running. It hides traces and antivirus software cannot detect its presence. It will check if the computer is connected to the Internet. If it can connect to the Internet, it will try to visit http://www.mypremierfutbol.com or http://www.todaysfutbol.com. At that time, the two website servers were hosted in Malaysia and Denmark.
It tells the server via an encrypted connection that it has already controlled a new PC. The worm then automatically updates to the latest version. The worm will copy itself to any USB drive inserted into the computer. It installs a fake device driver and uses the signature of the company Realtek in Taiwan.